Amazon Web Services (AWS)
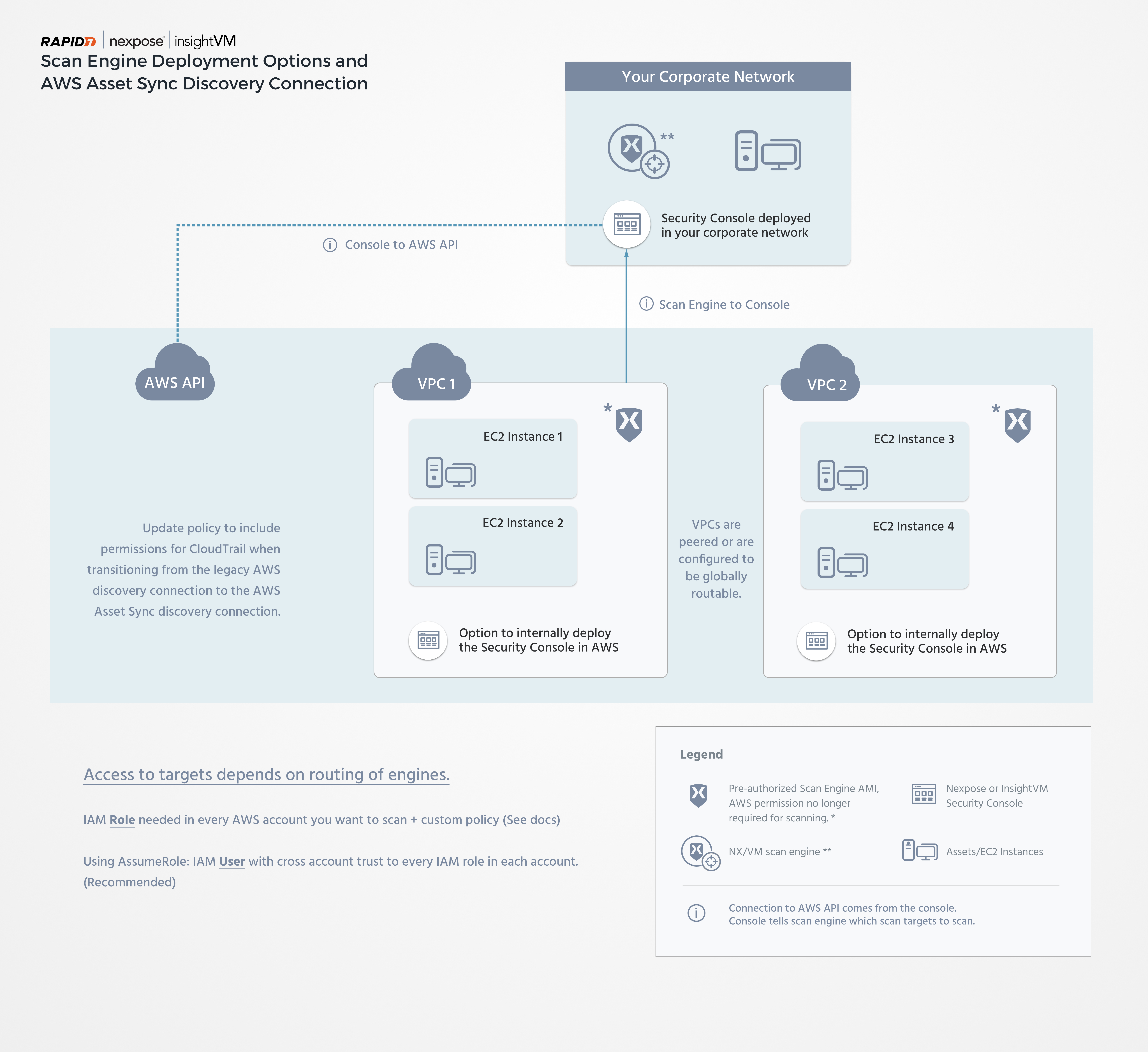
Vulnerability Management (InsightVM) subscribers can scan AWS assets with either a Scan Engine deployed in the AWS environment or a traditionally deployed on-premises Scan Engine. Similarly, the Security Console itself can also be deployed in AWS or on-premises in your own infrastructure. The Security Console can pair with as many Scan Engines as you need to perform vulnerability assessments.
Get started with AWS
While you can choose to scan your AWS assets with either an AWS-based or traditional Scan Engine, the former is the preferable option for several reasons. The AWS Scan Engine is designed to perform internal scans of your AWS environment. It uses Dynamic Discovery to identify all your AWS EC2 instances before scanning them. This ensures that you only scan your own infrastructure. However, it also means that certain restrictions apply:
- Assets must be discovered through the AWS EC2 API. Therefore, a standard broad range network scan is not an option.
- AWS Scan Engines are not accessible through the typical interactive methods that are available for on-premises Scan Engines, such as SSH, RDP, and others. However, if you are running your Scan Engine on an EC2 instance that has the AWS SSM agent, you can use it to gain interactive access.
- You can only scan within peered or globally routable VPCs. You cannot scan the internet.
Configure your AWS environment
Your AWS environment must have the properly configured security groups to support AWS asset scanning. We recommend creating two security groups:
- One for your Scan Engine
- One for your scan targets
The scan target security group should be attached to every EC2 asset you wish to scan. Follow these steps to create a security group in the AWS console:
- In your AWS console, expand the Services dropdown and click EC2 under the Compute category. The EC2 Console page displays.
- In the Network & Security section of the menu, click Security Groups.
- Click Create Security Group.
Create a Scan Engine security group
- Give your Scan Engine security group a descriptive name. Including
scan-enginesomewhere in the name will be useful for identification going forward. - If desired, give the Scan Engine security group a description.
- Select the VPC that your Scan Engine belongs to from the dropdown menu. This security group should have no incoming rules, but you should create outbound rules that allow the engine to scan the network ranges to which you are deploying EC2 instances.
- Click Create.
Create a scan targets security group
- Just like the Scan Engine security group, give your scan target security group a descriptive name. This time, include
scan-targetsin the name for identification purposes. - If desired, give the scan target security group a description.
- Using the dropdown menu, specify the VPC that your intended scan targets belong to from the dropdown menu.
- Under Security Group Rules, select Inbound and Add Rule.
- Under the Type column, select All traffic from the dropdown menu.
- Under the Source column, select Custom from the dropdown menu and type in the Group ID of your Scan Engine security group.
- Click Create.
Cross-account asset import with Dynamic Discovery
If you have multiple AWS accounts that you would like to import assets from, you can do so by providing role Amazon Resource Names (ARNs) from those accounts along with an optional session name when creating your AWS Asset Sync discovery connection. You can read more about using STS Assume Role for cross-account access in the following AWS documentation resources:
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_permissions-to-switch.html
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_common-scenarios_aws-accounts.html
Asset discovery and vulnerability assessment
Be aware that the AWS Asset Sync discovery connection that you configure will only detect assets. You will still need a Scan Engine to assess those assets for vulnerabilities. See the following Cross-account scans section for details on how you can deploy a Scan Engine for this use case.
Cross-account scans
You can use a single Scan Engine to scan multiple VPCs as long as the VPC where the Scan Engine lives can connect to the VPCs where your target assets exist. You can typically satisfy this requirement using VPC peering , but AWS Transit Gateway is another option.