Creating and managing Dynamic Discovery connections
Creating and managing Dynamic Discovery connections
This action provides Vulnerability Management with the information it needs to contact a server or process that manages the asset environment.
You must have Global Administrator permissions to create or manage Dynamic Discovery connections. See Managing users and authentication.
Creating a connection
- On the Administration page, click Assets > Discovery Connections. The Security Console displays the General page of the Asset Discovery Connection panel.
- On the New Discovery Connection page, select a connection type:
- Exchange ActiveSync (LDAP) is for mobile devices managed by an Active Directory (AD) server.
- Exchange ActiveSync (WinRM/PowerShell) is for mobile devices managed by an on-premises Exchange server accessed with PowerShell.
- Exchange ActiveSync (WinRM/Office 365) is for mobile devices managed by Cloud-based Exchange server running Microsoft Office 365.
- vmware vSphere is for environments managed by VMware vCenter or ESX/ESXi.
- AWS is for environments managed by Amazon Web Services.
- DHCP Service is for assets that Scan Engines discover by collecting log data from DHCP servers.
- McAfee Security ePolicy Orchestrator is for assets managed by Intel Security ePolicy Orchestrator (ePO).
- Active Directory (LDAP) is for devices managed by an Active Directory (AD) server.
- Intel Security Data Exchange Layer is for identifying malicious events on files present in systems managed by ePO, and for communicating Nexpose assessment data for consumption in Intel Security products.
Adding a Mobile Device Connection
- Enter a unique name for the new connection on the New Discovery Connection page.
- Enter the name of the Active Directory (AD) server to which the Security Console will connect.
- Select a protocol from the drop-down list. LDAPS, which is LDAP over SSL, is the more secure option and is recommended if it is enabled on your AD server.
- Enter a user name and password for a member of the Organization Management Security Group in Microsoft Exchange. This account will enable the Security Console to discover mobile devices connected to the AD server.
- Click Save.
- Continue with Initiating Dynamic Discovery.
Add an Amazon Web Services Asset Sync Connection
AWS requires a static site
Amazon Web Services Asset Sync connections require a static site.
- Enter a unique name for the new connection.
- From the drop-down list, select the geographic region where your AWS instances are deployed. A single connection can specify multiple regions, if necessary.
- If the Security Console is deployed inside the AWS network, select the appropriate check box. If you indicate that the Security Console is inside the AWS network, the Credentials link disappears from the left navigation pane. You do not need to configure credentials, since the AWS API recognizes the IAM role of the AWS instance that the Security Console is installed on.
- If the Scan Engine you will use to scan the AWS environment is deployed inside the AWS network, select the appropriate check box. This will enable the application to scan private IP addresses.
- Enter an Access Key ID and Secret Access Key with which the application will log on to the AWS API.
- If you are using AWS AssumeRole for cross-account access, enter one role ARN per line and an optional Session Name for the assumed role session. The session name is a string of characters consisting of upper- and lower-case alphanumeric characters with no spaces. You can also include underscores or any of the following characters: =,.@-
TIP
When multiple ARNs are present, the application will iterate over each ARN and attempt to import assets from the region(s) specified.
- If desired, click Test Credential to confirm that the connection is successful.
- Select Synchronize Amazon Web Services Asset Sync assets to import AWS assets and remove stale assets.
- Select a site to associate the assets with. To exclude specific assets from being imported, enter the tags in the Do not import assets with the following tags: box. The format is key:value + key:value +… If this box is empty, all assets are imported.
- Select Import tags to import all Amazon Web Services tags. To include specific tags, enter these tags in the Only import the following tags: box. The format is key:value + key:value +… If this box is empty, all tags are imported. AWS tags are imported as custom tags on the corresponding asset, and can be easily identified by the prefix Amazon-web-services.
Default Tag Creation
By default, and regardless of the state of the Import Tags check box, the Amazon Web Services Asset Sync connection will create a Security Console tag based on the imported VPC ID of the instance.
- Click Save.
Adding a VMware vSphere Connection
NOTE
VMware vSphere connections require a dynamic site.
- Enter a unique name for the new connection on the New Discovery Connection page.
- Enter a fully qualified domain name for the server that the Security Console will contact in order to discover assets.
- Enter a port number and select the protocol for the connection.
- Enter a user name and password with which the Security Console will log on to the server. Make sure that the account has access to any virtual machine that you want to discover.
- Click Save.
- Continue with Initiating Dynamic Discovery.
Adding a DHCP-Directory Watcher Connection
NOTE
DHCP connections require a dynamic site.
- Enter a unique name for the new connection on the New Discovery Connection page.
- Select an event source.
- Select Directory Watcher as the collection method.
- Enter a network path to the folder containing the DHCP server logs to be monitored. Use the format
//server/path/to/folder. The server can be either a host name or IP address. - Select the Scan Engine that will collect the DHCP server log information.
- Enter the administrative user name and password for accessing the DHCP server.
- Click Save.
- Continue with Initiating Dynamic Discovery.
Tip: If you create a connection and later change it to reference a different DHCP server, your asset discovery results will change. Therefore, if it is important to you to associate assets with specific DHCP servers in Nexpose, consider associating the name of the connection with the DHCP server and changing that name if you change the referenced server. Also, note that you cannot create duplicate DHCP connections.
Adding a DHCP-Syslog Connection
NOTE
DHCP connections require a dynamic site.
TIP
Syslog is the only available data collection method for the Infoblox Trinzic event source.
- Enter a unique name for the new connection on the New Discovery Connection page.
- Select an event source type.
- Select the Syslog collection method.
- Select the number of the port that the syslog parser listens on for log entries related to asset information.
- Select the protocol for the port that the syslog parser listens on for log entries related to asset information.
- Select the Scan Engine that will collect the DHCP server log information.
- Click Save.
- Continue with Initiating Dynamic Discovery.
Adding a McAfee ePolicy Orchestrator Connection
- Enter a unique name for the new connection.
- Enter the username and password for the user to connect to McAfee ePolicy Orchestrator (ePO). For security best practices, this should be a service user exclusively for use with the Nexpose integration. The Nexpose ePo extension automatically creates a user called NexposeServiceUser.
- Enter the IP address or the hostname of the server where ePO is installed.
- Enter the port on which ePO is running.
- If the ePO server uses a self-signed certificate, select Untrusted Certificate Permitted. Otherwise, leave it clear.
- Select Consume McAfee ePolicy Orchestrator assets. This setting is necessary for the initial configuration in order for Nexpose to collect information about the assets. If you do not want to continue to collect information about the assets on an ongoing basis (for instance, if you believe the information will seldom change), you can return to the configuration at a later time and clear this setting.
- Select a site to which to associate the assets.
- To populate the Rapid7 Nexpose Insight: Top 10 Riskiest Systems dashboard in ePO with data, select Push risk scores. The data will be automatically updated whenever a Nexpose scan finds risk score changes in ePO managed assets.
- If desired, click Test Credential to confirm that the username and password connect as expected.
- Click Save.
- Navigate back to the site. The assets will have populated within the site. You can now create dynamic asset groups and scan the assets.
Adding an Active Directory Connection
- Enter a unique name for the new connection.
- Enter the Server IP or host name of the Active Directory (AD) server to which the Security Console will connect.
- Select a protocol from the drop-down list. LDAPS, which is LDAP over SSL, is the more secure option and is recommended if it is enabled on your AD server.
- Enter a user name and password, and optionally click Test Credential to confirm that the credentials connect as expected.
- If desired, use the Base Query field to specify the portion of the Domain Component (DC) tree you would like to import, and the Search Query field to further qualify the computers you would like to discover, using an LDAP Query: https://technet.microsoft.com/en-us/library/aa996205(v=exchg.65).aspx
- Select Consume Active Directory (LDAP) assets. This setting is necessary for the initial configuration in order for Nexpose to collect information about the assets. If you do not want to continue to collect information about the assets on an ongoing basis (for instance, if you believe the information will seldom change), you can return to the configuration at a later time and clear this setting.
- Select a site to which to associate the assets.
- If desired, click the Preview button to see the top 50 results of your query to make sure your query is working as expected.
- Click Save.
- Navigate back to the site. The assets will have populated within the site. The time it takes to completely populate the site will vary, based on how long it takes the active directory to respond to the query. You can now create dynamic asset groups and scan the assets.
Adding a McAfee Data Exchange Layer Connection
- Enter a unique name for the new connection.
- Enter the username and password for the user to connect to McAfee ePolicy Orchestrator (ePO), which generates certificates that allow communication with McAfee Data Exchange Layer (DXL). For security best practices, this should be a service user that was created specifically for use with the Nexpose integration. The user should be in an ePO permission set with the DXL McAfee MePO Certificate Creation permission assigned. Your IP address and hostname will be the same as for your ePO connection, but the username and password should be different
- Enter the IP address or the hostname of the server where ePO with McAfee Data Exchange Layer is installed.
- Enter the port on which ePO is running.
- Select Find details of a vulnerability to gather vulnerability details that have already been collected. This setting is checked by default and cannot be modified. The setting is mandatory because it enables clients to get additional details for a particular vulnerability that Nexpose publishes.
- Select Publish vulnerabilities to publish information about vulnerabilities discovered by Nexpose back to McAfee Data Exchange Layer.
- If desired, click Test Credential to confirm that the username and password connect to ePO as expected.
- Click Save.
Once a Security McAfee Data Exchange Layer (DXL) connection has been saved, additional changes will not apply until the Security Console is restarted. You can edit, test, and save the credential configuration but the changes will only be applied upon Security Console restart. This also applies to deleting a connection; although the deleted connection will no longer appear in the Nexpose Security Console interface, you will not be able to create a new DXL connection with the same credential configuration until a Nexpose Security Console restart.
Preparing Vulnerability Management
Outbound access required to .azure.com and .microsoftonline.com
The Vulnerability Management console needs outbound access to .azure.com and .microsoft online.com on port 443. The discovery connection is created from the console itself (not the engines).
Adding a Microsoft Azure Connection
- Enter a unique name for the new connection.
- Enter the tenant ID associated with your Azure instance.
- Enter the application ID associated with the Rapid7 application created in your Azure AD instance.
- Enter the application secret key generated for the Rapid7 application created in your Azure AD instance.
- If desired, click Test Credential to confirm that the connection is successful.
- If the Scan Engine you will use to scan the Azure environment is deployed inside the Azure network, select the appropriate check box. This will enable the application to scan private IP addresses.
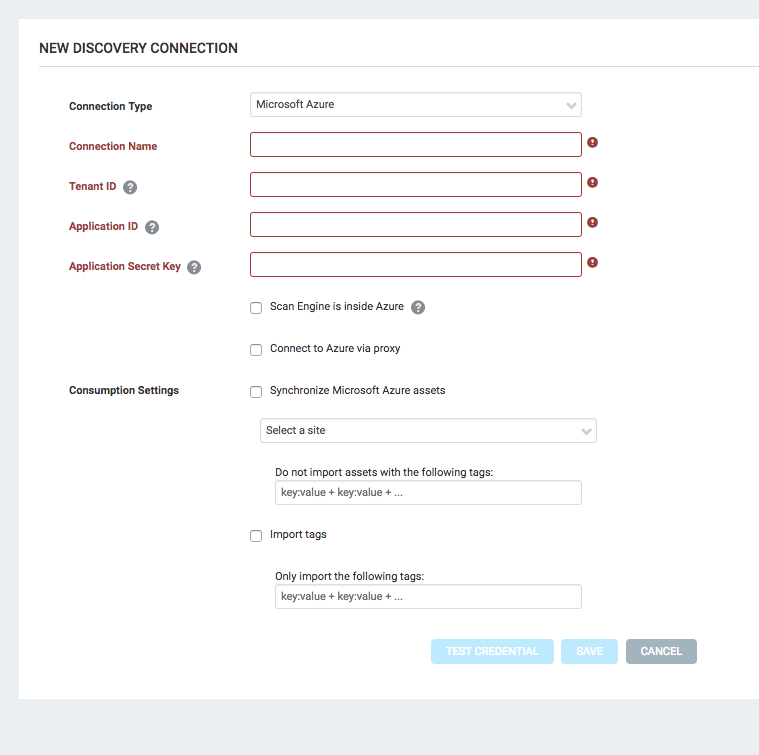
- Select Synchronize Microsoft Azure assets to import Azure assets and remove stale assets.
- Select a site to which to associate the assets.
- To exclude specific assets from being imported, enter the tags in the “Do not import assets with the following tags:” box. The format is
key: value + key: value +...If this box is empty, all assets are imported. - Select Import tags to import all Azure tags.
- To include specific tags, enter these tags in the “Only import the following tags:” box. The format is
key: value + key: value +...If this box is empty, all tags are imported. - Click Save.
View available connections
- Click the Administration page, click Assets > Discovery Connections. The Discovery Connections page displays your existing connections.
Edit existing connections
NOTE
Connections that are opened for editing do not display or remember sensitive fields such as passwords or secret keys. If you attempt to edit a connection, you must reenter these values.
- On the “Discovery Connections” page described previously, click the name link of any discovery connection to open it.
- Modify the fields as desired.
- Click Save when finished.
Delete connections
WARNING
The Security Console does not ask you to confirm the deletion of a connection. Make sure you fully intend to delete a connection before proceeding.
- On the Discovery Connections page, browse to the connection you want to delete.
- Click the trash icon under the “Delete” column to delete the connection.
You cannot delete a connection that has a dynamic site or an in-progress scan associated with it. Also, changing connection settings may affect asset membership of a dynamic site. See Configuring a site using a Dynamic Discovery connection. You can determine which dynamic sites are associated with any connection by going to the Discovery Management page. See Monitoring Dynamic Discovery.
If you change a connection by using a different account, it may affect your discovery results depending which virtual machines the new account has access to. For example: You first create a connection with an account that only has access to all of the advertising department’s virtual machines. You then initiate discovery and create a dynamic site. Later, you update the connection configuration with credentials for an account that only has access to the human resources department’s virtual machines. Your dynamic site and discovery results will still include the advertising department’s virtual machines; however, information about those machines will no longer be dynamically updated. Information is only dynamically updated for machines to which the connecting account has access.
Creating a connection in a site configuration
NOTE
Only the connections listed below can be created within a site configuration.
If you want to create a connection while configuring a new site, click the Create site button on the Home page. OR Click the Create tab at the top of the page and then select Site from the drop-down list.
If you want to create a connection for an existing site, click that site’s Edit icon in the Sites table on the Home page.
- Click the Assets link in the site configuration.
- Select Connection as the option for specifying assets.
- Click Create Connection.
- Select a connection type:
- Exchange ActiveSync (LDAP) is for mobile devices managed by an Active Directory (AD) server.
- Exchange ActiveSync (WinRM/PowerShell) is for mobile devices managed by an on-premises Exchange server accessed with PowerShell.
- Exchange ActiveSync (WinRM/Office 365) is for mobile devices managed by Cloud-based Exchange server running Microsoft Office 365.
- vmware vSphere is for environments managed by VMware vCenter or ESX/ESXi.
- DHCP Service is for assets that Scan Engines discover by collecting log data from DHCP servers.
Adding an Exchange ActiveSync (LDAP) Connection
NOTE
ActiveSync connections require a dynamic site.
- Enter a unique name for the new connection on the New connection tab.
- Enter the name of the Active Directory (AD) server to which the Security Console will connect.
- Select a protocol from the drop-down list. LDAPS, which is LDAP over SSL, is the more secure option and is recommended if it is enabled on your AD server.
- Enter a user name and password for a member of the Organization Management Security Group in Microsoft Exchange. This account will enable the Security Console to discover mobile devices connected to the AD server. Note: Once you save credentials in this setting, changes will not take effect until you restart Nexpose.
- Click Save. The connection appears in the Connection drop-down list, which you can view by clicking Select Connection.
- Continue with Initiating Dynamic Discovery.
Adding an Exchange ActiveSync (WinRM/PowerS/hell or WinRM/Office 365) Connection
NOTE
ActiveSync connections require a dynamic site.
- Enter a unique name for the new connection on the Vulnerability Management tab.
- Enter the name of the of the WinRM gateway server to which the Security Console will connect.
- Enter a user name and password for an account that has WinRM permissions for the gateway server.
- Enter the fully qualified domain name of the Exchange server that manages the mobile device information.
- Enter a user name and password for an administrator account or a user account that has View-Only Organizational Management or higher role of the Organization Management Security Group in Microsoft Exchange.
- Click Save. The connection appears in the Connection drop-down list, which you can view by clicking Select Connection.
- Continue with Initiating Dynamic Discovery.
Adding a VMware vSphere Connection (site configuration)
NOTE
VMware vSphere connections require a dynamic site.
- Enter a unique name for the new connection on the New connection tab.
- Enter a fully qualified domain name for the server that the Security Console will contact in order to discover assets.
- Enter a port number and select the protocol for the connection.
- Enter a user name and password with which the Security Console will log on to the server. Make sure that the account has access to any virtual machine that you want to discover.
- Click Save. The connection appears in the Connection drop-down list, which you can view by clicking Select Connection.
- Continue with Initiating Dynamic Discovery
Adding a DHCP-Directory Watcher Connection (site configuration)
NOTE
DHCP connections require a dynamic site.
- Enter a unique name for the new connection.
- Select an event source type.
- Select the Directory Watcher collection method.
- Enter a network path to the folder containing the DHCP server logs to be queried. Use the format
//server/path/to/folder. The server can be either a host name or IP address. - Select the Scan Engine that will collect the DHCP server log information.
- Enter the administrative user name and password for accessing the DHCP server.
- Click Save. The connection appears in the Connection drop-down list, which you can view by clicking Select Connection.
- Continue with Initiating Dynamic Discovery.
Adding a DHCP-Syslog Connection (site configuration)
NOTE
DHCP connections require a dynamic site.
TIP
Syslog is the only available collection method for the Infoblox Trinzic event source.
- Enter a unique name for the new connection.
- Select an event source type.
- Select the Syslog collection method.
- Enter the number for the port that the syslog parser listens on for log entries related to asset information.
- Select the protocol for the port that the syslog parser listens on for log entries related to asset information.
- Select the Scan Engine that will collect the DHCP server log information.
- Click Save. The connection appears in the Connection drop-down list, which you can view by clicking Select Connection.
- Continue with Initiating Dynamic Discovery.