Enhanced vulnerability detection for Multi-NIC assets
`
Historical product limitations
Historically, when assets were scanned as part of fingerprinting, network interface details were not intrinsically identified as the data was gathered. On multi-homed assets, our correlation algorithms have therefore not accounted for accurately tracking vulnerability data across multiple interfaces on the same asset. There is some complexity in addressing this issue on assets that have two or more network interfaces (Network Interface Cards - NICs).
An asset with multiple network interfaces could have network services that do not listen on all interfaces. Each network interface could have one or more IP addresses. For example, a network interface could have a primary IP address and zero or more alias addresses. Each IP address may have associated services and each service may have corresponding vulnerabilities. When an asset with multiple network interfaces was scanned, depending on the order they are assessed, the results from the last IP address scanned have taken precedence over the results of all previously scanned IP addresses on the asset.
As a result, Nexpose and Vulnerability Management (InsightVM) vulnerability correlation have not merged results from other IP addresses associated with that asset. Therefore, there is a chance a vulnerability will be incorrectly shown as remediated because the most recently scanned network interface is considered to be the only network interface on the asset. If a follow-up scan is executed and another NIC is assessed last, then the result may change and again show the existence of the vulnerability.
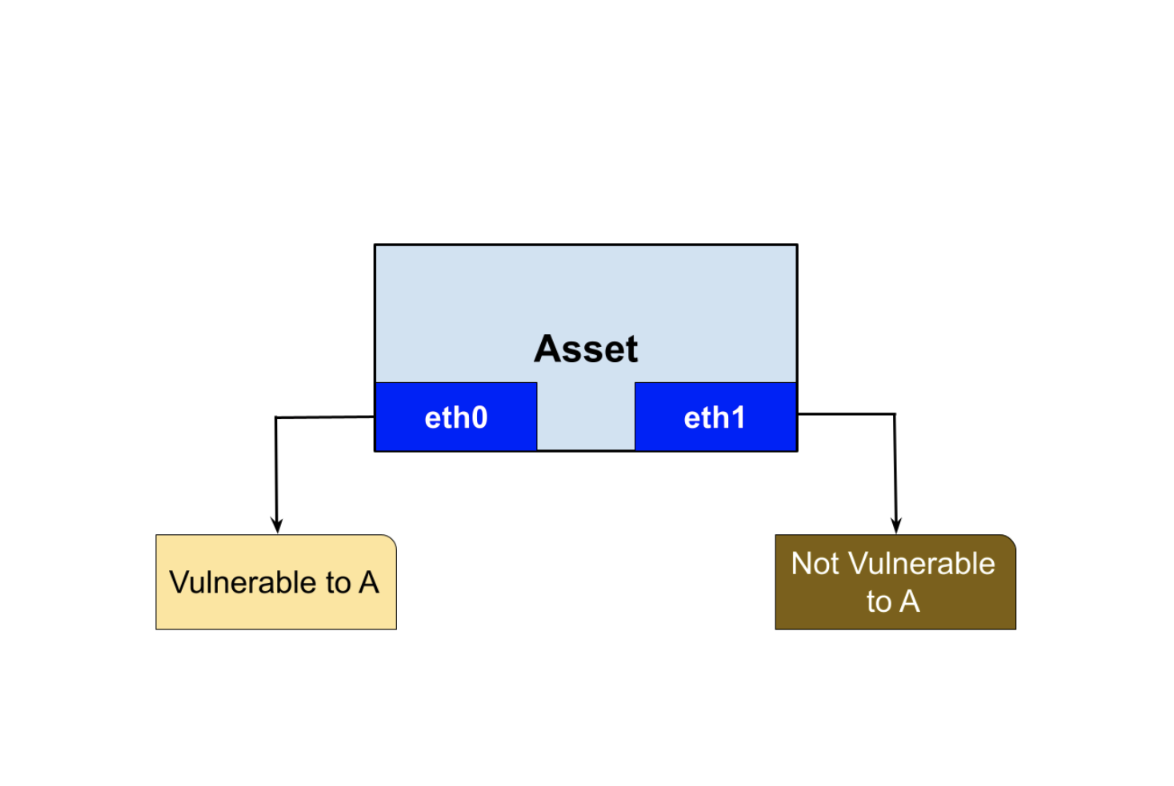
The following is a common scenario that demonstrates this issue:
- An asset contains two network interfaces, eth0 and eth1.
- Eth0 is vulnerable to vulnerability A and eth1 is not.
- A scan is performed and eth0 is found vulnerable. The vulnerability is assessed and stored.
- Eth1 is then scanned and the product determines that the asset is no longer vulnerable to vulnerability A and erroneously remediates it.
Solution
Vulnerability Management (InsightVM) fingerprinting capabilities are now enhanced to capture network interface data from Microsoft Windows and Linux assets. Additional metadata is collected to allow interfaces to be associated with IP addresses, services, and endpoints, i.e ports and protocols. This allows the Security Console to use the network interface when identifying if an endpoint is vulnerable, or is no longer vulnerable on successive scans. With this feature, customers observe more accurate endpoint vulnerability detection on their multi-homed assets. If the same vulnerability exists on more than one network interface card, multiple instance counts of the vulnerability are reported in the UI.
Multi-NIC vulnerability correlation feature
This feature can be enabled upon request for any customers that have multi-homed assets with multiple interface cards and would like to experience the initial release of this enhanced capability.
Initial release limitations and caveats
| Components | Details | |
|---|---|---|
| OS Support | Microsoft Windows and Linux assets only. | |
| Scan Types | This feature requires an authenticated scan of the multi-homed asset to be performed. | |
| Interface Vulnerability Data | Data is collected for scanned interfaces only. | |
| Correlation | Vulnerability correlation only. | |
| Link Aggregation | Channel Bonding (Linux) and NIC Teaming (MS Windows) scenarios are supported. On MS Windows, when two or more physical interfaces are assigned to a NIC Team, the NIC Team virtual interface may be assigned the IP address of one of its underlying physical NICs. I.e. the IP Address is reused. A “DHCP renew” request from the asset can alleviate this issue. | |
| UI Reporting Limitation | With this initial release, vulnerability details are not explicitly reported by the network interface, within the Security Console UI but it is possible to filter by Network Interface within the EA platform. Security Console reporting enhancements will be addressed in a future release of the feature. In this release, note that multi-interface vulnerability data is represented in some Security Console data tables as additional instances of vulnerabilities, assets, or services. These additional instances are not duplicates, but a more accurate listing of detected vulnerabilities across all scanned interfaces. The associated IP address is the most recently scanned interface on the asset. Also note that vulnerability proof data does not provide explicit vulnerability mappings by interface | |
| Considerations for API users | Any direct consumers of data via the API see additional vulnerability instances which appear identical, but represent an instance of the vulnerability on each interface of a multi-homed asset. Consumers should be aware that any logic they have in place to de-duplicate identical vulnerabilities on an asset, will therefore remove these additional instances. |
Vulnerability Management (InsightVM) feature reporting
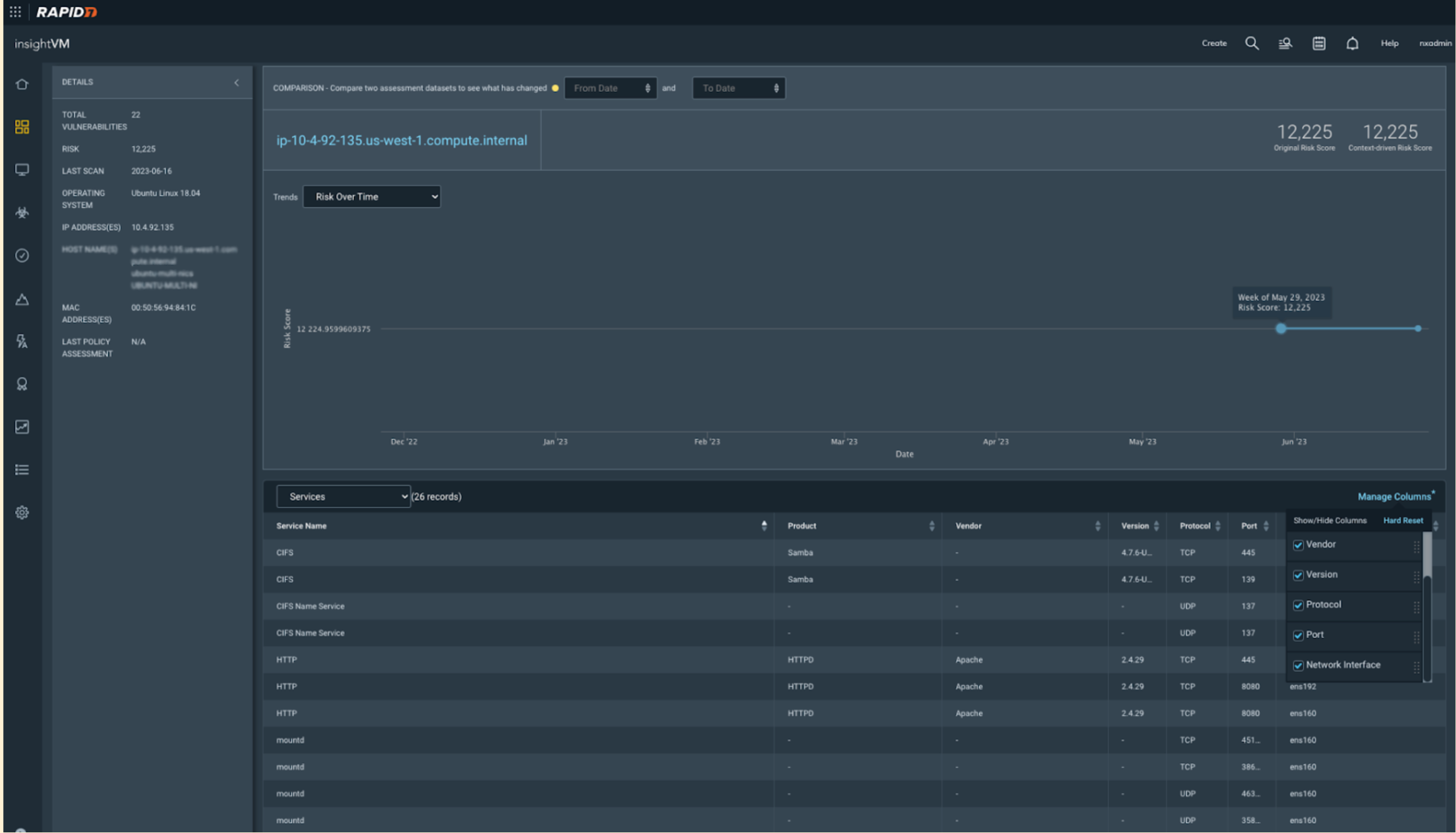
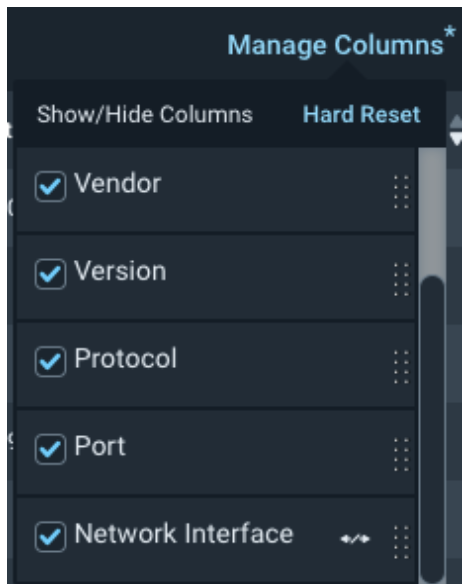
The Vulnerability Management (InsightVM) Exposure Analytics platform has been updated to display additional vulnerability instances if they are found on multiple interfaces (Asset Details Page). When multi-interface assets are present, it is now possible to use a new feature within the Manage Columns interface to filter Service results by network interface.
Asset detail page
Important considerations when using Multi-NIC vulnerability correlation feature
When a running a remediation scan:
- Users must scan the same NIC to verify remediation as integration does not correlate NIC details from other NIC scans.
- Users must not remove the NIC as part of remediation as integration is unaware of deleted NICs.