Enhance vulnerability scans with the Metasploit Remote Check Service
The Metasploit Remote Check Service expands the remote vulnerability check capabilities of a Scan Engine, allowing it to utilize Metasploit modules to perform vulnerability checks.
Requirements
These requirements are subject to change
The Metasploit Remote Check Service is currently being made available in the beta phase. System requirements may change as development continues.
The Metasploit Remote Check Service requires the following to run:
- The Scan Engine must be installed on a host running a Linux operating system.
- The Scan Engine must be on product version 6.6.63 or later.
- The service will consume an average of 1GB of additional RAM on your Scan Engine host compared to standard scanning. Verify that your Scan Engine host’s existing RAM can absorb this additional load before enabling the service.
- Only distributed Scan Engines and the local Scan Engine housed in the Security Console itself are eligible to use the service.
- Hosted Scan Engines provided through the External Scanning Service are not supported.
Before you begin
You will need to use the Vulnerability Management command console to enable the Metasploit Remote Check Service on one or more eligible Scan Engines. Your user account must have the Global Administrator role to access this console and execute commands.
The command console features commands that allow you to:
- Enable or disable the Metasploit Remote Check Service on all supported Scan Engines paired to the Security Console.
- Enable or disable the Metasploit Remote Check Service on a custom list of Scan Engines paired to the Security Console according to the Scan Engine name.
- If you’re unsure of the names assigned to the Scan Engines that are paired to your Security Console, navigate to the engine management screen to review them.
Enable the Metasploit Remote Check Service
Enabling the Metasploit Remote Check Service on one or more Scan Engines may take several minutes. Once complete, the command console will inform you. It will also report if any of the affected Scan Engines failed to enable the Metasploit Remote Check Service.
Enable the Metasploit Remote Check Service on all supported Scan Engines paired to a Security Console:
Local Scan Engine inclusion for Security Consoles on Linux hosts
Running the following command for a Security Console installed on a Linux host will also enable the Metasploit Remote Check Service on the Local Scan Engine.
- In the command console, enter and execute the following command:
enable mrc-service on all engines- The command console will inform you once the command completes.
Enable the Metasploit Remote Check Service on a selection of one or more Scan Engines paired to a Security Console:
- In the command console, enter and execute the following command that lists the Scan Engines you want to target by name. Separate multiple engines with commas (as shown below with the
engine name-#examples):
enable mrc-service on engines engine-name-1, engine-name-2, engine-name-3- The command console will inform you once the command completes.
Disable the Metasploit Remote Check Service
The commands to disable the Metasploit Remote Check Service work in the same way as their enablement counterparts.
Run the following command to disable the Metasploit Remote Check Service on all Scan Engines paired to your Security Console:
disable mrc-service on all enginesTo disable the service on a custom list of Scan Engines, run the following command with each Scan Engine specified by name. Separate multiple engine names with commas:
disable mrc-service on engines engine-name-1, engine-name-2, engine-name-3Configure scan templates for the Metasploit Remote Check Service
Once enabled on a Scan Engine, all future scans will use the Metasploit Remote Check Service as long as the scan template being used is configured to perform vulnerability checks. If you want to enable or disable Metasploit Remote Checks on a scan-by-scan basis, you can make the following adjustments in the scan template to accommodate this:
- Modifying the Use the Metasploit Remote Check Service when available (Beta) checkbox
- Modifying the included vulnerability check types
Scan template requirements for this service
For the Metasploit Remote Check Service to run, your scan template must have both the corresponding checkbox enabled and the Metasploit check type included. Disabling either of these configurations will disable the entire service when this template is used. If you prefer to disable the service for a specific scan, you only need to disable one of these configurations.
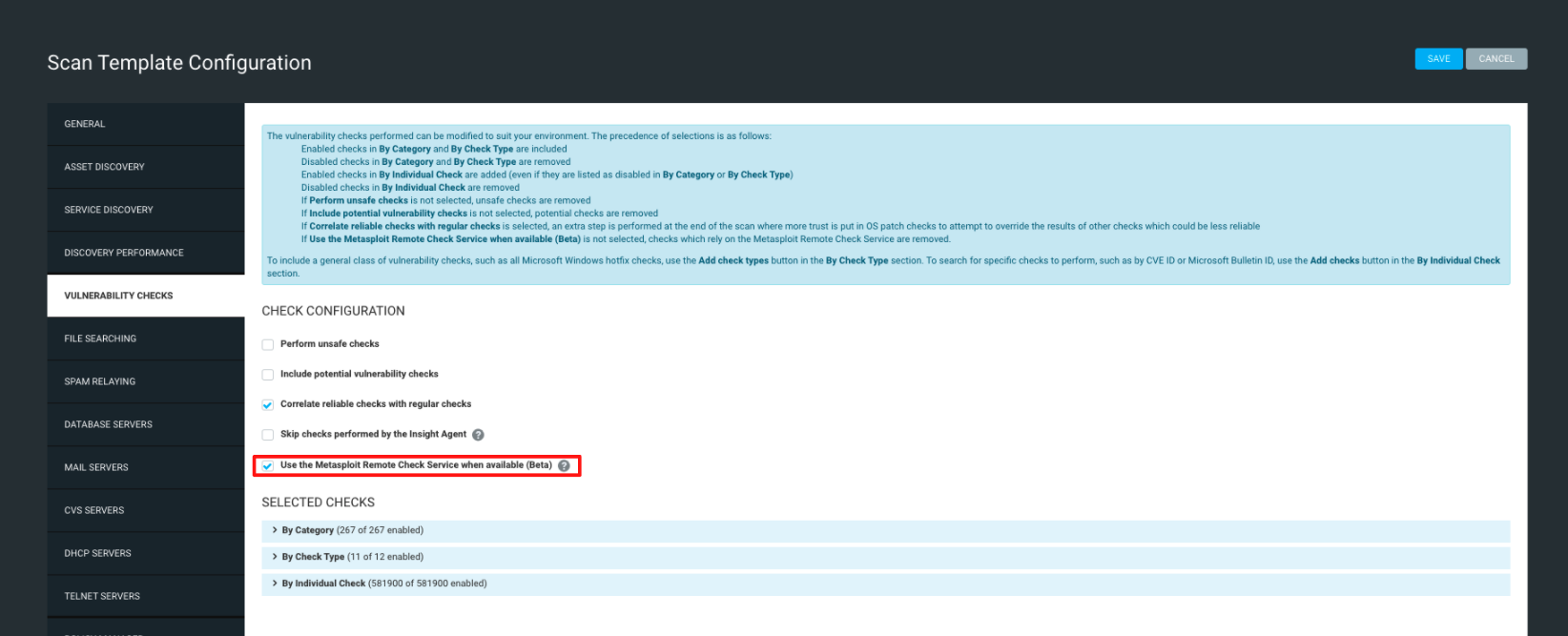
Enable or disable Metasploit Remote Checks using the Scan Configuration checkbox:
- On the Scan Template Configuration page, click the Vulnerability Checks tab.
- Under Check Configuration, toggle the Use the Metasploit Remote Check Service when available (Beta) checkbox as desired.
Enable or disable Metasploit Remote checks using the vulnerability check type:
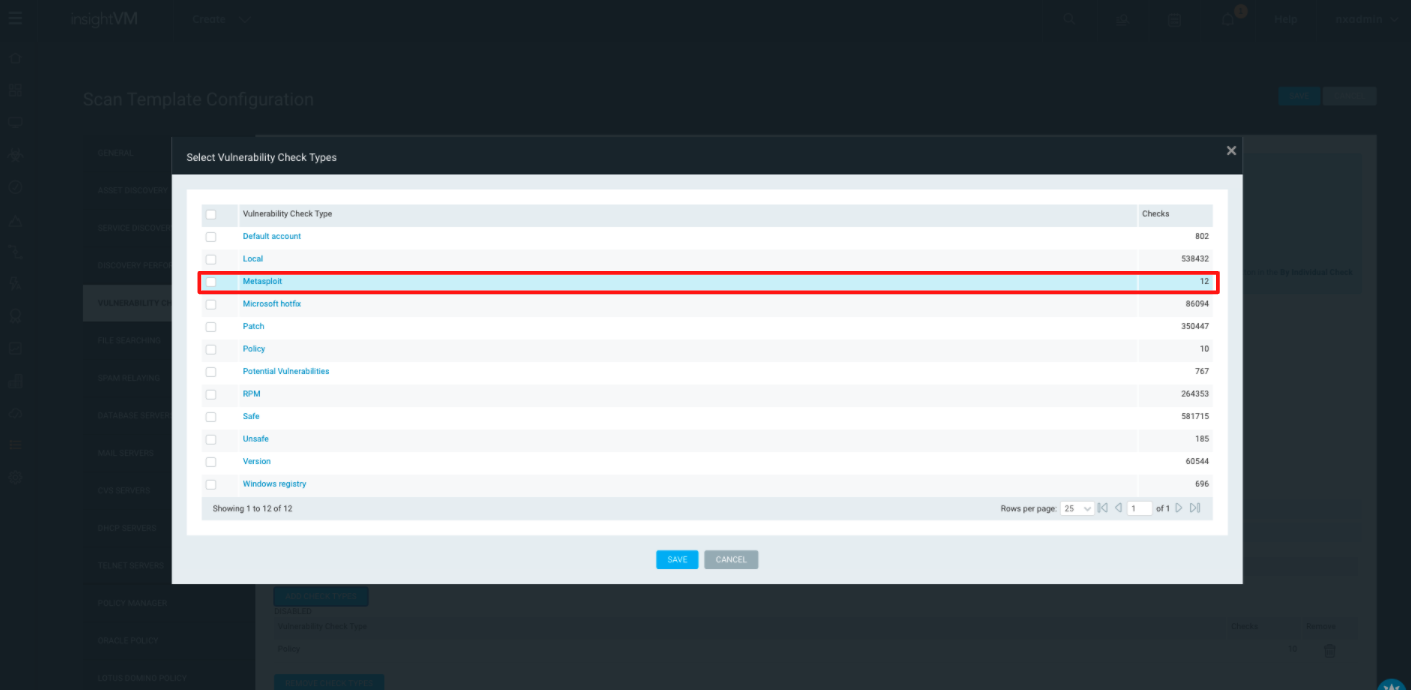
- On the Scan Template Configuration page, click the Vulnerability Checks tab.
- Under Selected Checks, expand the By Check Type dropdown.
- By default, the Metasploit check type will already be included. If you wish to disable the Metasploit Remote Check Service, click Remove Check Types and select the checkbox for the Metasploit vulnerability check type, then click Save.
- If you wish to enable the Metasploit check type again after disabling it initially, repeat the previous step with the Add Check Types button.
Support options
If you experience issues with the Metasploit Remote Check Service on a Scan Engine, verify that your Scan Engine host meets the requirements detailed at the beginning of this article.
If you’re still having trouble, submit a case with the Rapid7 Support team so we can troubleshoot the issue. Our Support Engineers will be in the best position to assist you if you also include a support package for the Scan Engine that is having problems with the Metasploit Remote Check Service. The support command in the command console can generate a support package that you can attach to your case manually as a file or send to our Support team directly. See the Vulnerability Management command console documentation for additional instructions on using this command.