Risk Strategies
Legacy risk strategies have been deprecated as of January 21, 2026
As of January 21, 2026, all legacy risk strategies have been deprecated: RealRisk, Temporal, TemporalPlus, Weighted, and PCI ASV 2.0. To ensure continued support and access to the most effective risk prioritization, switch to the Active Risk strategy. Active Risk uses continuously updated CVSS data, threat intelligence, and proprietary Rapid7 research to provide the most accurate risk assessment for your assets.
To learn more, see our Legacy Risk Strategies End of Life Announcement.
Active Risk is Rapid7’s recommended built-in strategy for assessing and analyzing vulnerability risk on a scale of 0-1000. Active Risk uses the latest CVSS score with intelligence from threat feeds like AttackerKB, Metasploit, ExploitDB, Project Lorelei, CISA KEV list, and other third-party dark web sources to provide security teams with a threat-aware vulnerability risk score and to help prioritize remediation for the most critical vulnerabilities.

This approach evaluates key characteristics of vulnerabilities and assets in your environment.
- Vulnerabilities are evaluated on how easy they are to exploit, as well as potential attacker outcomes.
- Assets are evaluated for business sensitivity. For example, if a database that contains credit card numbers is compromised, the damage to your organization will be significantly greater than if a printer server is compromised.
With Active Risk, you can:
- Sort vulnerabilities by risk score: By sorting vulnerabilities by risk score, you can make a quick visual determination as to which vulnerabilities need your immediate attention and which are less critical.
- View risk trends over time in reports: Track progress in your remediation effort or determine whether risk is increasing or decreasing over time in different segments of your network.
To determine likelihood and impact, the Active Risk algorithm applies unique exploit and malware exposure metrics for each vulnerability which is then compounded with CVSS base metrics.
Active Risk is computed using the latest version of CVSS metrics
Active Risk uses the latest CVSS version available for a vulnerability when calculating the risk score. Active Risk will use a CVSSv3.1 score if it is available, and if not, it will use the next most recent version available such as CVSSv3 or CVSSv2.
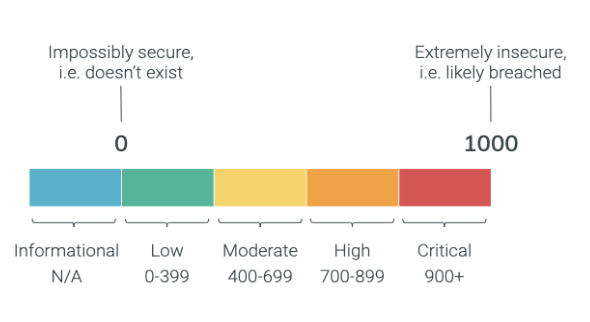
In contrast to traditional CVSS scores that use a 1-10 system, this algorithm allows for greater incrementation throughout our risk score assessments. Thousands of vulnerabilities may have a CVSS score of 10, making it difficult to determine remediation priorities.
How does Active Risk’s scoring algorithm work?
The model computes a maximum impact between 0 and 1000 based on the following vulnerability attributes:
| Attribute | Description |
|---|---|
| CVSS score | The Common Vulnerability Scoring System (CVSS) Score is a numerical value (ranging from 0.0 to 10.0) that represents the severity of a vulnerability. By default, the Executive Risk View uses v3 scores where available, otherwise v2 scores are used. For zero-day scenarios where a CVSS score has not yet been assigned but exploitation in the wild has been observed, the CVSS score is not considered. |
| Exploitability | If an exploit or exploit kit exists for a vulnerability, based on Metasploit and ExploitDB data. “Exploitation” is a cybersecurity term for the ability to leverage an attack on a vulnerability by hackers. Read our blog for more information. |
| Exploited in the Wild | If a vulnerability has been actively targeted by attackers in the real world, based on Rapid7 Research, CISA KEV, and Third-Party Feeds. “Exploited in the Wild” is a cybersecurity term for malware that is actively being used by attackers and can be found on devices belonging to ordinary users. |
| AttackerKB | An assessment for how valuable a vulnerability is to an attacker and how easily exploitable a vulnerability is in real environments. |
| Exceptions | If a vulnerability exception has been applied in Vulnerability Management. An exception is accepted risk for a vulnerability. |
After you’ve selected Active Risk as your strategy, use the Vulnerability Findings by Active Risk Score Severity and Vulnerability Findings by Active Risk Score Severity and Publish Age dashboard cards to view your active risks.
Changing your risk strategy
You may choose to change the current risk strategy to get a different perspective on the risk in your environment, for example a custom risk strategy.
Active Risk can't be changed back to legacy risk strategies or recalculated with historical data
You are not able to change your risk strategy to a legacy risk strategy after selecting Active Risk, even if it was your previous risk strategy. Legacy risk strategies - Temporal, TemporalPlus, Weighted, and PCI ASV 2.0 - have been deprecated as of January 21, 2026. To ensure continued support and access to the most effective risk prioritization, switch to the Active Risk strategy. Additionally, historical data cannot be recalculated with Active Risk as it is not available. For more information on adopting Active Risk, see the adoption guide or the risk score comparison guide .
- In the Security Console, click Administration > Risk Score Settings > Risk Strategy.
- Click the arrow of any risk strategy to view information about it. Information includes a description of the strategy and its calculated factors, the strategy’s source (built-in or custom), and how long it has been in use if it is the currently selected strategy.
- Select the radio button for the risk strategy you want to change to.
- Click Save.
(Optional) View risk strategy usage history
This allows you to see how different risk strategies have been applied to all of your scan data. It also is useful for determining why segments of risk trend data appear inconsistent.
- Under the Risk Strategies Usage section, click the Current Usage tab.
- In the Current Usage tab, view all the risk strategies that are currently applied to your entire scan data set. The Status column indicates whether any calculations did not complete successfully.
- Click the Change Audit tab to view every modification of risk strategy usage in the history of your installation. The table in this section lists every instance that a different risk strategy was applied, the affected date range, and the user who made the change. This information may also be useful for troubleshooting risk trend inconsistencies or for other purposes.
- (Optional) Click the Export to CSV icon to export the change audit information to CSV format, which you can use in a spreadsheet for internal purposes.
Review your custom strategy XML file
Make sure that your custom strategy XML file is well-formed and contains all required elements to ensure that the application performs as expected.
Understanding how risk scoring works with scans
An asset goes through several phases of scanning before a completed status for that scan will display. An asset that has not gone through all the required scan phases has a status of in progress. Vulnerability Management only calculates risk scores based on data from assets with completed scan status.
If a scan pauses or stops, The application does not use results from assets that do not have a completed status for the computation of risk scores. For example, 10 assets are scanned in parallel. Seven have completed scan status; three do not. The scan is stopped. Risk is calculated based on the results for the seven assets with completed status. For the three in progress assets, it uses data from the last completed scan.
To determine scan status consult the scan log. See Viewing the scan log.