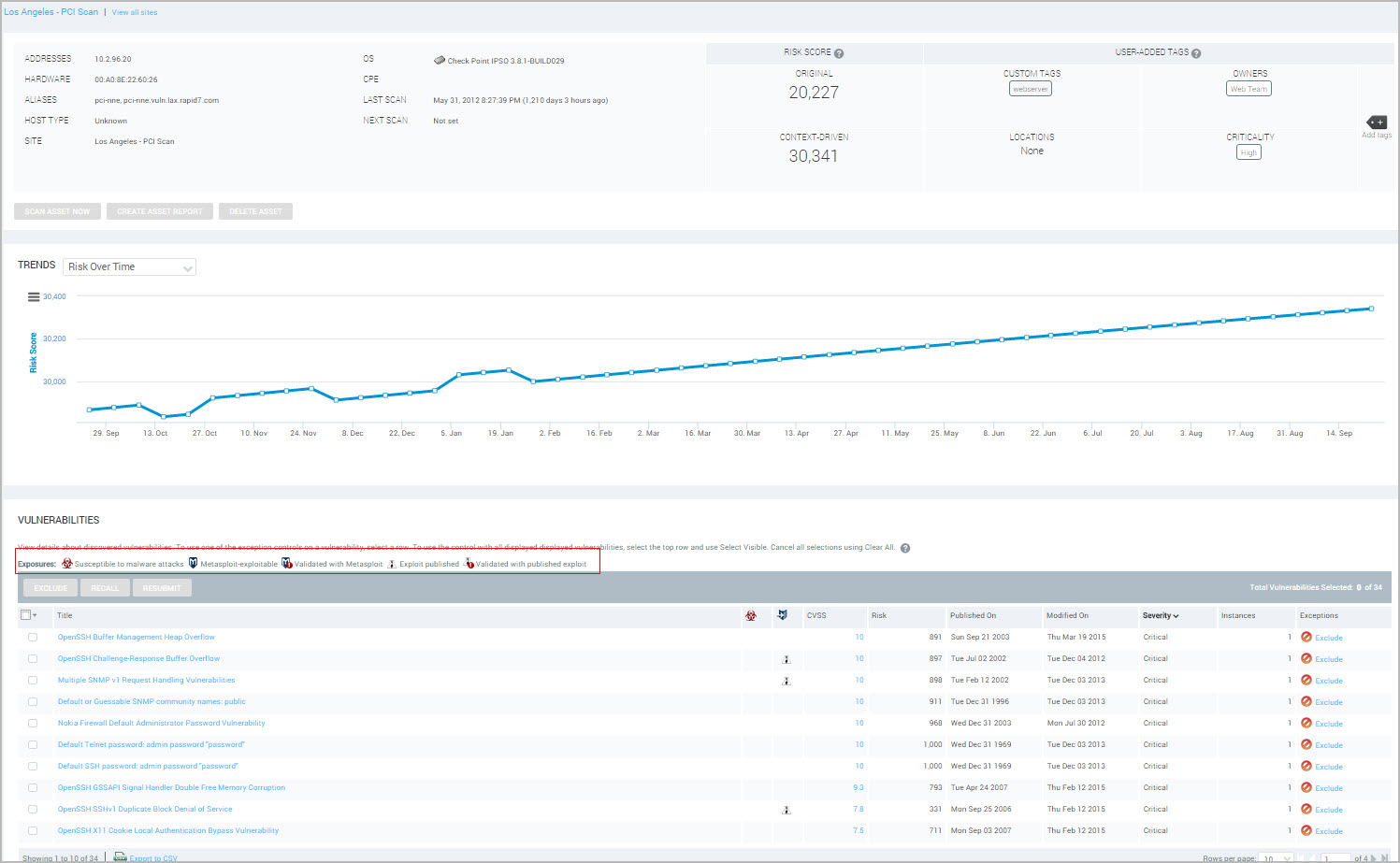
Working with vulnerabilities
Analyze scan results to review, understand, filter, and manage vulnerabilities.
Analyzing scan results
Analyzing the vulnerabilities discovered in scans is a critical step in improving your security posture. By examining the frequency, affected assets, risk level, exploitability and other characteristics of a vulnerability, you can prioritize its remediation and manage your security resources effectively.
Videos of analyzing scan results
Reviewing Scan Results
Review scan results to gain a better understanding of how or why a solution has flagged assets as susceptible to certain vulnerabilities. This is helpful when remediation teams have a different opinion on the validity or accuracy of scan results. We have created two extremely insightful videos for you to review. Review these videos and follow the steps shown to review questionable vulnerability results.
If you feel you have run into vulnerability results that your teams are curious about, or disagree with, please review the steps outlined in the video to determine if what you are seeing is expected behavior or if you should submit a Support case to review a potential inaccurate result.
Every vulnerability discovered in the scanning process is added to vulnerability database. This extensive, full-text, searchable database also stores information on patches, downloadable fixes, and reference content about security weaknesses. The application keeps the database current through a subscription service that maintains and updates vulnerability definitions and links. It contacts this service for new information every six hours.
Vulnerability database details
The database has been certified to be compatible with the MITRE Corporation’s Common Vulnerabilities and Exposures (CVE) index, which standardizes the names of vulnerabilities across diverse security products and vendors. The index rates vulnerabilities according to MITRE’s Common Vulnerabilities Scoring System (CVSS) Version 3.1. If CVSSv3.1 is not available, vulnerabilities will be rated using the next latest version.
An application algorithm computes the CVSS score based on ease of exploit, remote execution capability, credentialed access requirement, and other criteria. The score, which ranges from 1.0 to 10.0, is used in Payment Card Industry (PCI) compliance testing. For more information about CVSS scoring, go to the FIRST website .
Viewing active vulnerabilities
Viewing vulnerabilities and their risk scores helps you to prioritize remediation projects. You also can find out which vulnerabilities have exploits available, enabling you to verify those vulnerabilities. See Using Exploit Exposure.
The Security Console displays the Vulnerabilities page, which lists all the vulnerabilities for assets that the currently logged-on user is authorized to see, depending on that user’s permissions. Global Administrators see all the vulnerabilities in the database because they have access to all assets in your organization.
View vulnerabilities
- In the Security Console, click the Vulnerabilities icon.
- Review, filter, and work with the vulnerabilities listed.
- Click a vulnerability to view more details.
Understanding vulnerability data
The Vulnerabilities page provides high-level vulnerability data.
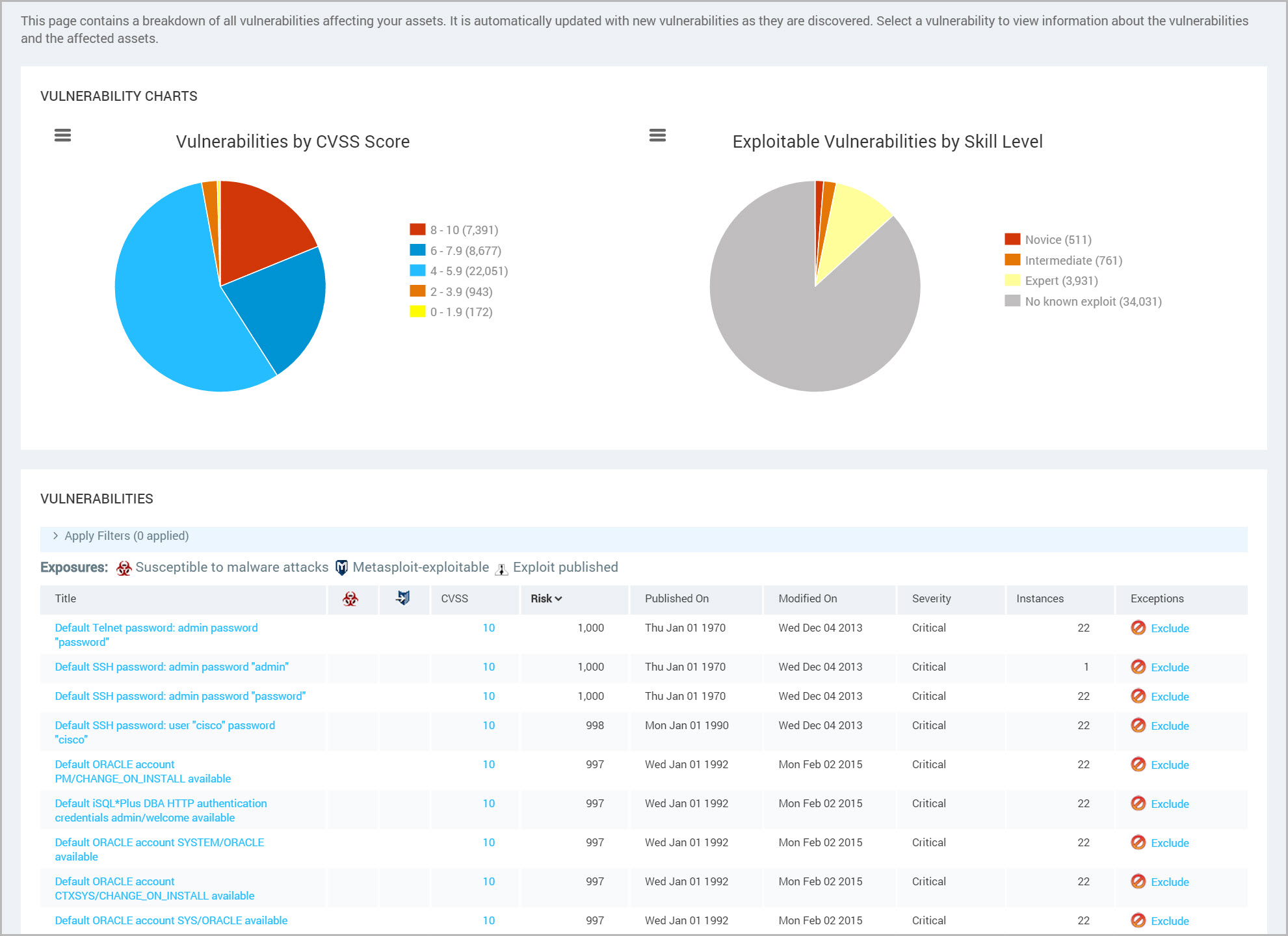
The charts on the Vulnerabilities page display your vulnerabilities by CVSS score and exploitable skill levels.
| Chart | Description |
|---|---|
| CVSS Score | Displays how many of your vulnerabilities fall into each of the CVSS score ranges. This score is based on access complexity, required authentication, and impact on data. The score ranges from 1 to 10, with 10 being the worst, so you should prioritize the vulnerabilities with the higher numbers. |
| Exploitable Vulnerabilities by Skill Level | Shows you your vulnerabilities categorized by the level of skill required to exploit them. The most easily exploitable vulnerabilities present the greatest threat, since there will be more people who possess the necessary skills, so you should prioritize remediating the Novice-level ones and work your way up to Expert. |
In the Vulnerability Listing table, you can view malware, exploit, risk score, and more data to help you prioritize remediation.
Malware
Malware and exploits
| Icon | Description |
|---|---|
 | Susceptible to malware attacks. |
 | Export to CSV |
 | Exploit exists in the Exploit Database. The Exploit Database is an archive of exploits and vulnerable software. |
 | Metasploit module available. Displays a link to a Metasploit module that provides detailed exploit information and resources. |
 | Exploitable |
 | Validated by an exploit through a Metasploit module. |
Malware
Each discovered vulnerability that has at least one malware kit, also known as an exploit kit, associated with it will have a malware exposure icon. If you click the icon, the console displays the Threat Listing pop-up window that lists all the malware kits that attackers can use to write and deploy malicious code for attacking your environment through the vulnerability.
You can generate a comma-separated values (CSV) file of the malware kit list to share with others in your organization. Click the Export to CSV icon. Depending on your browser settings, you will see a pop-up window with options to save the file or open it in a compatible program.
You can also click the Exploits tab in the pop-up window to view published exploits for the vulnerability. A published exploit is one that has been developed in Metasploit or listed in the Exploit Database.
Exploits
Discovered vulnerabilities with an associated exploit have an exploit icon. If you click this icon the console displays the Threat Listing pop-up window that lists descriptions about all available exploits, their required skill levels, and their online sources.
The Exploit Database is an archive of exploits and vulnerable software. If a Metasploit exploit is available, the console displays the Metasploit icon and a link to a Metasploit module that provides detailed exploit information and resources.
There are three levels of exploit skill: Novice, Intermediate, and Expert. These map to Metasploit’s seven-level exploit ranking. For more information, see the Metasploit Framework Exploit Ranking page .
- Novice maps to Great through Excellent.
- Intermediate maps to Normal through Good.
- Expert maps to Manual through Low through Average.
You can generate a comma-separated values (CSV) file of the exploit list and related data to share with others in your organization. Click the Export to CSV icon. Depending on your browser settings, you will see a pop-up window with options to save the file or open it in a compatible program.
You can also click the Malware tab in the pop-up window to view any malware kits that attackers can use to write and deploy malicious code for attacking your environment through the vulnerability.
CVSS scoring systems and behaviors
CVSS scoring systems and behaviors
The CVSS Score column lists the score for each vulnerability. By default, the score shown will be derived from the CVSS Version 3.1 scale, as long as data exists for it. If not, the next latest version’s score will be shown. Scores will show the vector currently being used to produce the value. All CVSS Version 3.1 scores are prefixed with CVSS:3.1 for ease of recognition.
The score link itself will also open the CVSS Details window. This window contains additional information about each metric being applied to the vector currently in use. Should data exist for CVSS Version 3.1, you will have multiple version tabs to choose from.
Default CVSS vector scenario
Rapid7 assigns CVSS scores to vulnerability content in Vulnerability Management according to calculations provided in the National Vulnerability Database (NVD) published by NIST at https://nvd.nist.gov/ and other vendor sources.
In addition to vendor-published CVSS scores, Rapid7 uses an integrated advanced machine learning model to ensure all vulnerabilities are scored accurately. This AI model leverages a broader range of data sources which allows Rapid7 to normalize CVSSv3 scores. The AI is trained to produce predictive CVSS scores by analyzing vulnerability information and comparing it to CVEs scored by industry experts.
Because CVSSv2 was retired by the NVD on July 13 2022 and CVSSv2 severity scores are no longer provided, Rapid7 compensates by using CVSSv3 vectors to populate an equivalent CVSSv2 score.
You can read more about vulnerability metrics and CVSS information at https://nvd.nist.gov/vuln-metrics/cvss .
Customer data is not used to train our AI model
The new AI-powered CVSS Score does not leverage any customer data to generate CVSS scores, and at no time is customer data exposed or used to train the model. The model analyzes historical vulnerability metadata and previously scored CVEs to determine the proper severity classification.
Understanding CVSS 10.0 Scores for Obsolete OS and Obsolete Software
To accurately reflect the risk associated with outdated technology, we assign a Common Vulnerability Scoring System (CVSS) score of 10.0 to any operating system (OS) or software that has reached its end-of-life (EOL).
Why a CVSS of 10.0?
A CVSS score of 10.0 represents the highest level of severity, indicating a critical vulnerability. This designation for EOL software is not arbitrary; it’s based on the inherent and significant risks associated with running obsolete systems:
- No security updates: Once software reaches EOL, vendors cease providing security patches. This means that any newly discovered vulnerabilities will remain unaddressed, leaving your systems exposed to exploitation.
- Known vulnerabilities: EOL software often has a long history of known vulnerabilities. Attackers are aware of these weaknesses and can readily exploit them.
- Unknown vulnerabilities: Beyond known vulnerabilities, there’s a high likelihood of undiscovered flaws in EOL software. These “zero-day” vulnerabilities can be exploited by sophisticated attackers with no patch or future disclosure.
- Increased attack surface: The lack of ongoing security updates expands the attack surface, leaving your systems more susceptible to various threats, including malware, ransomware, and data breaches.
- Compatibility issues: Older software can create compatibility issues with newer security tools and technologies, further hindering your ability to protect your systems.
- Compliance risks: Operating EOL software can violate industry regulations and compliance standards, potentially leading to legal and financial penalties.
- Unpredictable behavior: Without ongoing support, EOL software can become unstable and unpredictable, leading to system crashes and data loss.
What this means for you
A CVSS 10.0 score for EOL software highlights the critical need to:
- Upgrade or Replace: Prioritize upgrading or replacing obsolete OS and software with supported versions.
- Implement Compensating Controls: If immediate upgrades are not feasible, mitigate risks by implementing robust compensating controls, for example, network segmentation, intrusion detection systems, and strict access controls.
- Isolate Obsolete Systems: If complete removal is not possible, isolate obsolete systems from critical networks to limit the potential impact of a breach.
- Regularly Monitor: Closely monitor systems with EOL software for suspicious activity.
By assigning the highest possible CVSS base score of 10.0 to all obsolete checks, we provide you with a clear understanding of the risks associated with EOL software and empower you to take proactive steps to protect your environment.
Risk and Severity
Risk and severity
The Risk column lists the risk score that the application calculates, indicating the potential danger that each vulnerability poses to an attacker exploits it. The application provides multiple risk scoring models which you can configure. See the Risk strategies article for more information on available risk models.
The application assigns each vulnerability a severity level, which is listed in the Severity column. The three severity levels (Critical, Severe, and Moderate) reflect how much risk a given vulnerability poses to your network security. Vulnerability Management uses CVSSv2 scores to rate severity.
The severity ranking in the Severity column is not related to the severity score in PCI reports.
0 to 3.4 = Moderate
3.5 to 7.4 = Severe
7.5 to 10 = Critical
Instances
Instances
The Instances column lists the total number of instances of that vulnerability in your site. If you click the link for the vulnerability name, you can view which specific assets are affected by the vulnerability. See Viewing vulnerability details.
Conditions that can affect the richness of your scan results
An administrative change to your network, such as new credentials, may change the level of access that an asset permits during its next scan. If the application previously discovered certain vulnerabilities because an asset permitted greater access, that vulnerability data will no longer be available due to diminished access. This may result in a lower number of reported vulnerabilities, even if no remediation has occurred. Using baseline comparison reports to list differences between scans may yield incorrect results or provide more information than necessary because of these changes. Make sure that your assets permit the highest level of access required for the scans you are running to prevent these problems.
Solutions
Solutions
The Solution column links to the recommended solution to remediate the vulnerability. The pill icon represents the status of the solution. In most cases, one best solution will have been identified, and clicking the pill icon will take you directly to the recommended solution. Occasionally, there may be more than one possible best solution, depending on your environment. In this case, the icon will change appearance and clicking it will take you to a list of the potential solutions. Below are the potential states of the solutions:
| Icon | Meaning |
|---|---|
 | The application was able to identify a single best solution for this vulnerability on this asset. |
 | The application identified multiple potential best solutions. A human judgment call is needed to identify the best solution for your environment. |
 | Error state. This should appear rarely, but can occur in certain situations, such as if the vulnerability was deprecated, or the console has been decommissioned and is not taking updates. |
Categories and check types
Categories and check types
The Vulnerability Categories and Vulnerability Check Types tables list all categories and check types that the Application can scan for. Your scan template configuration settings determine which categories or check types the application will scan for. To determine if your environment has a vulnerability belonging to one of the listed checks or types, click the appropriate link. The Security Console displays a page listing all pertinent vulnerabilities. Click the link for any vulnerability to see its detail page, which lists any affected assets.
Filtering your view of vulnerabilities
Your scans may discover hundreds, or even thousands, of vulnerabilities, depending on the size of your scan environment. A high number of vulnerabilities displayed in the Vulnerability Listing table may make it difficult to assess and prioritize security issues. By filtering your view of vulnerabilities, you can reduce the sheer number of those displayed, and restrict the view to vulnerabilities that affect certain assets. For example, a Security Manager may only want to see vulnerabilities that affect assets in sites or asset groups that he or she manages. Or you can restrict the view to vulnerabilities that pose a greater threat to your organization, such as those with higher risk scores or CVSS rankings.
The CVSSv3 score filter works with the same operators described above. All operators except is not will limit results to vulnerabilities with Version 3 data.
Working with filters and operators in vulnerability displays
Filtering your view of vulnerabilities involves selecting one or more of the following filters, which are criteria for displaying specific vulnerabilities. For each filter, you select an operator, which controls how the filter is applied.
Site name
Site name is a filter for vulnerabilities that affect assets in specific sites. It works with the following operators:
- The is operator displays a drop-down list of site names. Click a name to display vulnerabilities that affect assets in that site. Using the SHIFT key, you can select multiple names.
- The is not operator displays a drop-down list of site names. Click a name to filter out vulnerabilities that affect assets in that site, so that they are not displayed. Using the SHIFT key, you can select multiple names.
Asset group name
Asset group name is a filter for vulnerabilities that affect assets in specific asset groups. It works with the following operators:
- The is operator displays a drop-down list of asset group names. Click a name to display vulnerabilities that affect assets in that asset group. Using the SHIFT key, you can select multiple names.
- The is not operator displays a drop-down list of asset group names. Click a name to filter out vulnerabilities that affect assets in that asset group, so that they are not displayed. Using the SHIFT key, you can select multiple names.
CVE ID
CVE ID is a filter for vulnerabilities based on the CVE ID. The CVE identifiers (IDs) are unique, common identifiers for publicly known information security vulnerabilities. For more information, see https://cve.mitre.org/cve/identifiers/index.html . The filter applies a search string to the CVE IDs, so that the search returns vulnerabilities that meet the specified criteria. It works with the following operators:
- is returns all vulnerabilities whose names match the search string exactly.
- is not returns all vulnerabilities whose names do not match the search string.
- contains returns all vulnerabilities whose names contain the search string anywhere in the name.
- does not contain returns all vulnerabilities whose names do not contain the search string.
After you select an operator, you type a search string for the CVE ID in the blank field.
CVSS score
CVSS score is a filter for vulnerabilities with specific CVSS rankings. It works with the following operators:
- The is operator displays all vulnerabilities that have a specified CVSS score.
- The is not operator displays all vulnerabilities that do not have a specified CVSS score.
- The is in the range of operator displays all vulnerabilities that fall within the range of two specified CVSS scores and include the high and low scores in the range.
- The is higher than operator displays all vulnerabilities that have a CVSS score higher than a specified score.
- The is lower than operator displays all vulnerabilities that have a CVSS score lower than a specified score.
After you select an operator, enter a score in the blank field. If you select the range operator, you would enter a low score and a high score to create the range. Acceptable values include any numeral from 0.0 to 10. You can only enter one digit to the right of the decimal. If you enter more than one digit, the score is automatically rounded up. For example, if you enter a score of 2.25, the score is automatically rounded up to 2.3.
Risk score
Risk score is a filter for vulnerabilities with certain risk scores. It works with the following operators:
- The is operator displays all vulnerabilities that have a specified risk score.
- The is not operator displays all vulnerabilities that do not have a specified risk score.
- The is in the range of operator displays all vulnerabilities that fall within the range of two specified risk scores and include the high and low scores in the range.
- The is higher than operator displays all vulnerabilities that have a risk score higher than a specified score.
- The is lower than operator displays all vulnerabilities that have a risk score lower than a specified score.
After you select an operator, enter a score in the blank field. If you select the range operator, you would type a low score and a high score to create the range. Keep in mind your currently selected risk strategy when searching for assets based on risk scores. For example, if the currently selected strategy is Active Risk, you will not find assets with scores higher than 1,000. Learn about different risk score strategies. Refer to the risk scores in your vulnerability and asset tables for guidance.
Vulnerability category
Vulnerability category is a filter that lets you search for vulnerabilities based on the categories that have been flagged on them during scans. Lists of vulnerability categories can be found in the scan template configuration or the report configuration.
The filter applies a search string to vulnerability categories, so that the search returns a list of vulnerabilities that either are or are not in categories that match that search string. It works with the following operators:
- contains returns all vulnerabilities whose category contains the search string. You can use an asterisk (*) as a wildcard character.
- does not contain returns all vulnerabilities that do not have a vulnerability whose category contains the search string. You can use an asterisk (*) as a wildcard character.
- is returns all vulnerabilities whose category matches the search string exactly.
- is not returns all vulnerabilities that do not have a vulnerability whose category matches the exact search string.
- starts with returns all vulnerabilities whose categories begin with the same characters as the search string.
- ends with returns all vulnerabilities whose categories end with the same characters as the search string.
After you select an operator, you type a search string for the vulnerability category in the blank field.
Vulnerability title
Vulnerability title is a filter that lets you search vulnerabilities based on their titles.The filter applies a search string to vulnerability titles, so that the search returns a list of assets that either have or do not have the specified string in their titles. It works with the following operators:
- contains returns all vulnerabilities whose name contains the search string. You can use an asterisk (*) as a wildcard character.
- does not contain returns all vulnerabilities whose name does not contain the search string. You can use an asterisk (*) as a wildcard character.
- is returns all vulnerabilities whose name matches the search string exactly.
- is not returns all vulnerabilties whose names do not match the exact search string.
- starts with returns all vulnerabilities whose names begin with the same characters as the search string.
- ends with returns all vulnerabilities whose names end with the same characters as the search string.
After you select an operator, you type a search string for the vulnerability name in the blank field.
You can only use each filter once. For example, you cannot select the Site name filter twice. If you want to specify more than one site name or asset name in the display criteria, use the SHIFT key to select multiple names when configuring the filter.
Applying vulnerability display filters
To apply vulnerability display filters, take the following steps:
- In the Security Console, click the Vulnerabilities tab. The Security Console displays the Vulnerabilities page.
- In the Vulnerability Listing table, expand the section to Apply Filters.
- Select a filter from the drop-down list.
- Select an operator for the filter.
- Enter or select a value based on the operator.
- Use the + button to add filters. Repeat the steps for selecting the filter, operator, and value. Use the - button to remove filters.
- Click Filter. The Security Console displays vulnerabilities that meet all filter criteria in the table.
Currently, filters do not change the number of displayed instances for each vulnerability.
Tip: You can export the filtered view of vulnerabilities as a comma-separated values (CSV) file to share with members of your security team. To do so, click the Export to CSV link at the bottom of the Vulnerability Listing table.
Viewing vulnerability details
To view detailed information about a vulnerability, click the link for any vulnerability listed on the Vulnerabilities page.
At the top of the page is a header containing details about the vulnerability. These include the following:
- Name and description of the vulnerability
- ID
- Severity level
- Risk Score
- CVSS version ratings and score
- CVSSV3 version ratings and score
- Date that information about the vulnerability was made publicly available
- Dates when the vulnerability data was added or modified by Rapid7
- Exploitability rating
- Vulnerability categories
- Common Vulnerabilities and Exposures (CVEs), if available
Below these items is a table listing each affected asset, port, and the site on which a scan reported the vulnerability. You can click on the link for the device name or address to view all of its vulnerabilities. You also can click the site link to view information about the site.
| Table | Description |
|---|---|
| Assets | The Port column in the Assets table displays the port that the application used to contact the affected service or software during the scan. The Network Interface column lists the unique network interface cards that the vulnerability was present on. The Status column lists a Vulnerable status for an asset if the application confirmed the vulnerability. It lists a Vulnerable Version status if the application only detected that the asset is running a version of a particular program that is known to have the vulnerability. The Proof column lists the method that the application used to detect the vulnerability on each asset. It uses exploitation methods typically associated with hackers, inspecting registry keys, banners, software version numbers, and other indicators of susceptibility. The First Found column displays the date on which the vulnerability was first detected in the environment. The Reintroduced column indicates if and when the vulnerability was reintroduced into your environment after a previous resolution. |
| Exploits | The Exploits table lists descriptions of available exploits and their online sources. The Exploit Database is an archive of exploits and vulnerable software. If a Metasploit exploit is available, the console displays the Metasploit icon and a link to a Metasploit module that provides detailed exploit information and resources. |
| Malware | The Malware table lists any malware kit that attackers can use to write and deploy malicious code for attacking your environment through the vulnerability. This table is not displayed if there is no known malware for the vulnerability. |
| References | The References table lists links to Web sites that provide comprehensive information about the vulnerability. |
| Remediations | At the very bottom of the page is the Remediations pane, which lists remediation steps and links for downloading patches and fixes. This pane includes two tabs:
|
When you view the vulnerabilities page for an asset, there will be additional tabs that categorize the vulnerabilities by relevance to that asset.
If you wish to query the database for a specific vulnerability, and you know its name, type all or part of the name in the Search box that appears on every page of the console interface, and click the magnifying glass icon. The console displays a page of search results organized by different categories, including vulnerabilities.
Calculate the mean time to remediation (MTTR)
While you are monitoring vulnerabilities, it’s important to have visibility into any vulnerabilities in your environment that were remediated and later reintroduced. With first_found and reintroduced timestamp data, you can conduct a root-cause analysis to identify how a vulnerability was allowed back into the system.
Mean time to remediation (MTTR) is a key metric that is calculated using the date a vulnerability was first introduced on an asset and, if applicable, the date it was reintroduced after patching.
By using this timestamp data to calculate the MTTR, and subsequently comparing that MTTR metric to your service level objectives (SLO), you can potentially identify process issues within your security program.
This is particularly helpful for decision-makers on the security program to track whether the number is increasing; if it is increasing, that may indicate that the security team is under-resourced and unable to remediate vulnerabilities within the specified SLO time frame.
Note: The API defines the remediation time for a vulnerability as the first date when an asset was scanned and that particular vulnerability was not found.
You can report on first-found and reintroduced data in these report types:
- XML Export 2.0
- SQL Query Export
- CSV Exports
- Custom Reports
- Data Warehouse
About vulnerability correlation
The vulnerability correlation algorithm in the Security Console enables vulnerabilities to be identified on individual Network Interface Cards (NICs). You can report on your assets with multiple NICs.
Why has my vulnerability count and risk score increased? The correlation algorithm can increase the number of vulnerabilities reported for assets with multiple network interfaces and therefore, increase overall vulnerability totals and risk score.
You can see NIC information after an authenticated vulnerability scan. NICs are discovered using vulnerability scans and correlated to an asset. Once a NIC is found, vulnerabilities are correlated at the NIC level.
- Supported APIs APIv4 (Integrations, ServiceNOW)
- Supported OS:
- Windows Assets with IPv4 addresses or hostnames that resolve to IPv4 addresses. -Linux assets with IPv4 addresses or hostnames that resolve to IPv4 addresses.
- Supported scans This feature only supports authenticated vulnerability scans.
- What does this feature not support? This feature doesn’t provide Multi-NIC support for the following:
- Data Warehouse
- IPv6 (only IPv4 is supported)
- APIv3
- Agent scanning and assessment
- Global IP search
Working with validated vulnerabilities
There are many ways to sort and prioritize vulnerabilities for remediation. One way is to give higher priority to vulnerabilities that have been validated, or proven definitively to exist. The application uses a number of methods to flag vulnerabilities during scans, such as fingerprinting software versions known to be vulnerable. These methods provide varying degrees of certainty that a vulnerability exists. You can increase your certainty that a vulnerability exists by exploiting it, which involves deploying code that penetrates your network or gains access to a computer through that specific vulnerability.
As discussed in the topic Viewing active vulnerabilities, any vulnerability that has a published exploit associated with it is marked with a Metasploit or Exploit Database icon. You can integrate Rapid7 Metasploit as a tool for validating vulnerabilities discovered in scans and then have Vulnerability Management indicate that these vulnerabilities have been validated on specific assets.
Metasploit is the only exploit application that the vulnerability validation feature supports. See a tutorial for performing vulnerability validation with Metasploit.
Work with validated vulnerabilities
To work in Vulnerability Management with vulnerabilities that have been validated with Metasploit, take the following steps:
- After performing exploits in Metasploit, click the Assets in the Security Console.
- Locate an asset that you would like to see validated vulnerabilities for. See Locating and working with assets.
- Double-click the asset’s name or IP address. The Security Console displays the details page for the asset.
View the Exploits column in the Vulnerabilities table.
- If a vulnerability has been validated with an exploit via a Metasploit module, the column displays the Metasploit icon with a validation symbol overlayed.
- To sort the vulnerabilities according to whether they have been validated, click the title row in the Exploits column.
As seen in the following screenshot, the descending sort order for this column is:
- vulnerabilities that have been validated with a Metasploit exploit
- vulnerabilities that can be validated with a Metasploit exploit
- vulnerabilities that have been validated with an Exploit database exploit
- vulnerabilities that can be validated with an Exploit database exploit