Integrate a Cisco Firepower Cloud Device
Configure a Cisco Firepower cloud device to pull IOCs from Digital Risk Protection (Threat Command). You must first add the device to Digital Risk Protection (Threat Command) and then configure the device to pull IOCs from Digital Risk Protection (Threat Command).
Limitations
The Cisco Firepower integration is subject to the following limitations:
-
Cisco Firepower supports only SHA-256 file-hash.
-
The Cisco Firepower Threat Intelligence Director (TID) must enabled on the Cisco Management Center.
-
URLs that contain port, protocol, or authentication information, and that also use the normalized version when detecting indicators are normalized. For example, TID normalizes any of the following URLs to google.com/index.htm : http://google.com/index.htm , http://google.com:8080/index.htm , google.com:8080/index.htm , or google.com/index.htm
Or, for example, TID normalizes http://abc@google.com:8080/index.htm as abc@google.com/index.htm/
For additional limitations, see the Cisco Firepower documentation.
Add a Cisco Firepower cloud device
Add a cloud device to Digital Risk Protection (Threat Command).
Prerequisites
- You have the credentials to access the device.
- You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
To add a cloud device to Digital Risk Protection (Threat Command):
- Log in to Digital Risk Protection (Threat Command) at https://dashboard.ti.insight.rapid7.com
- From the main menu, select Automation -> Integrations.
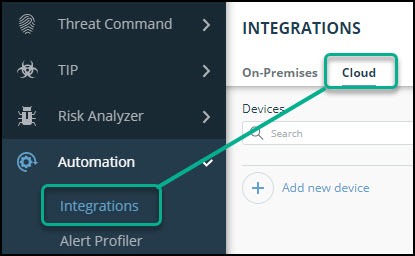
- From the Integrations page, click Cloud.
- Click Add new device.
- In the Add New Cloud Device dialog, type a user-defined name for the device. The name can contain a maximum of 50 letters, spaces, numbers, and underscores.
- Select the Device type.
The default device IOCs limit is displayed. - (Optional) You can change the IOCs limit.
- Click Add.
- To verify that the new device is added, refresh the Automation > Integrations page.
The new device is added to the cloud integrations device list. Next to the device name, there is a red dot, indicating that communication has not yet been established. The dot will change to green when the device is synchronized. If the device cannot synchronize for more than 48 hours, an email warning is sent to the account administrator.
Configure a Cisco Firepower device to pull IOCs
After a device has been added, you must enable it to pull IOCs from Digital Risk Protection (Threat Command).
Before you begin, ensure:
- You have the device login credentials.
- The device has been added.
- You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
- An IOC group for this device exists in Digital Risk Protection (Threat Command).
Creating IOC groups is described in Create an IOC group
When creating the IOC group for a Cisco Firepower device, keep the following in mind:
- The device has a maximum limit of 500,000 IOCs. You can decrease this limit when creating IOC groups.
- Due to device limitations, IOC groups can consist of only one type of IOC: domains, URLs, IP addresses and file hashes (SHA 256 only). To support more than one type, create multiple IOC groups.
-
From Digital Risk Protection (Threat Command), copy the Cisco Firepower IOC group URL into the Cisco Firepower Management Center:
- From Digital Risk Protection (Threat Command), select Automation > Integrations.
- From the On-Premises device list, select the Cisco Firepower device.
- Click the link icon to the far right of the device IOC group.
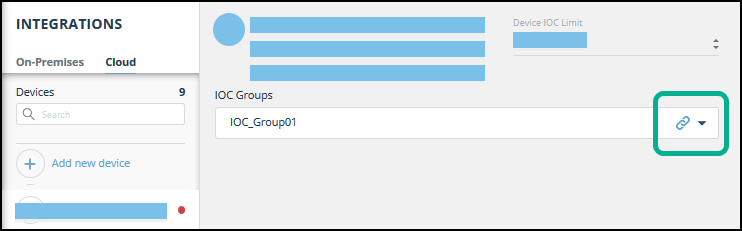
The IOC Group URL dialog is displayed.
- From the IOC Group URL dialog, copy the URL.
-
Log in to the Cisco Firepower Management Center.
-
Navigate to Intelligence > Sources.
-
In the top right, click + to add a new source.
The Add Source dialog is displayed.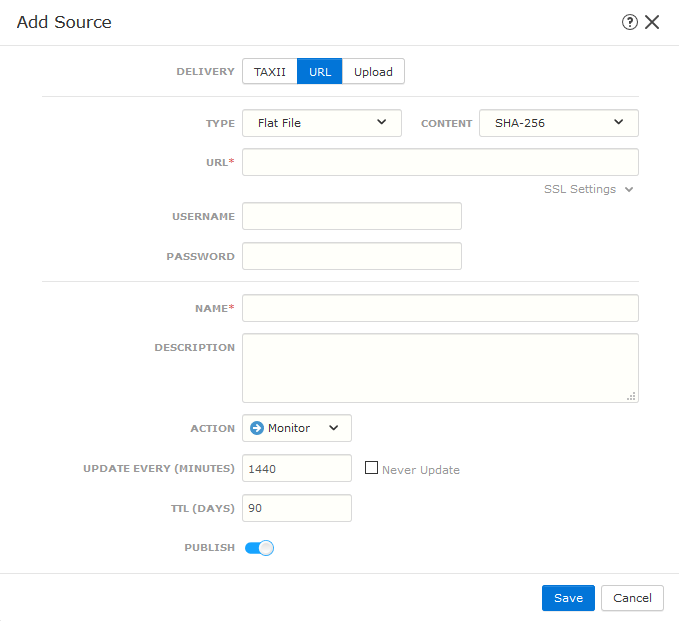
-
In the Add Source dialog, fill the fields, as follows:
- For Delivery, select URL.
- For Type, select Flat File.
- In the URL field, paste the IOC group URL from Digital Risk Protection (Threat Command).
- In the Content drop-down, select the content type that matches the content of the IOC group (for example, Domain, URL, or IPs).
- Type a user-defined name.
- To begin pulling IOCs immediately, select Publish.
- Click Save.
-
To verify that IOCs are being pulled into the Cisco Firepower console, navigate to Intelligence > Sources > Sources. The Status will be displayed as Completed.
This could take some time. Refresh to synchronize the status.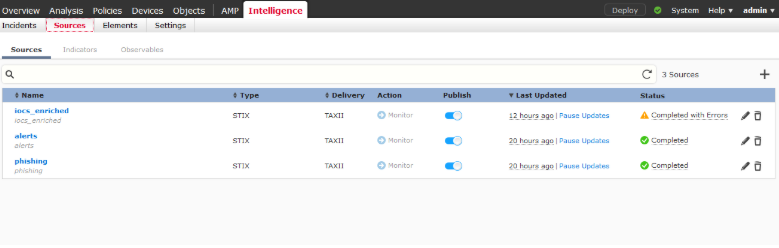
You can use the Cisco Firepower Management Center Indicators and Observables tabs to drill down in the IOCs and to perform related activities.