Configuring the Phishing Watch
To use the Phishing Watch feature, use the Phishing Watch Manager page to create phishing watch snippets, then deploy them on all company web pages that may be used for phishing attacks.
After a snippet is created, you can use the Phishing Watch Manager page to edit, delete, and monitor the snippet status.
This feature is described in Phishing Watch.
Access to the Phishing Watch Manager can be enabled for analyst users, from the Permissions tab on the Settings > Users page.
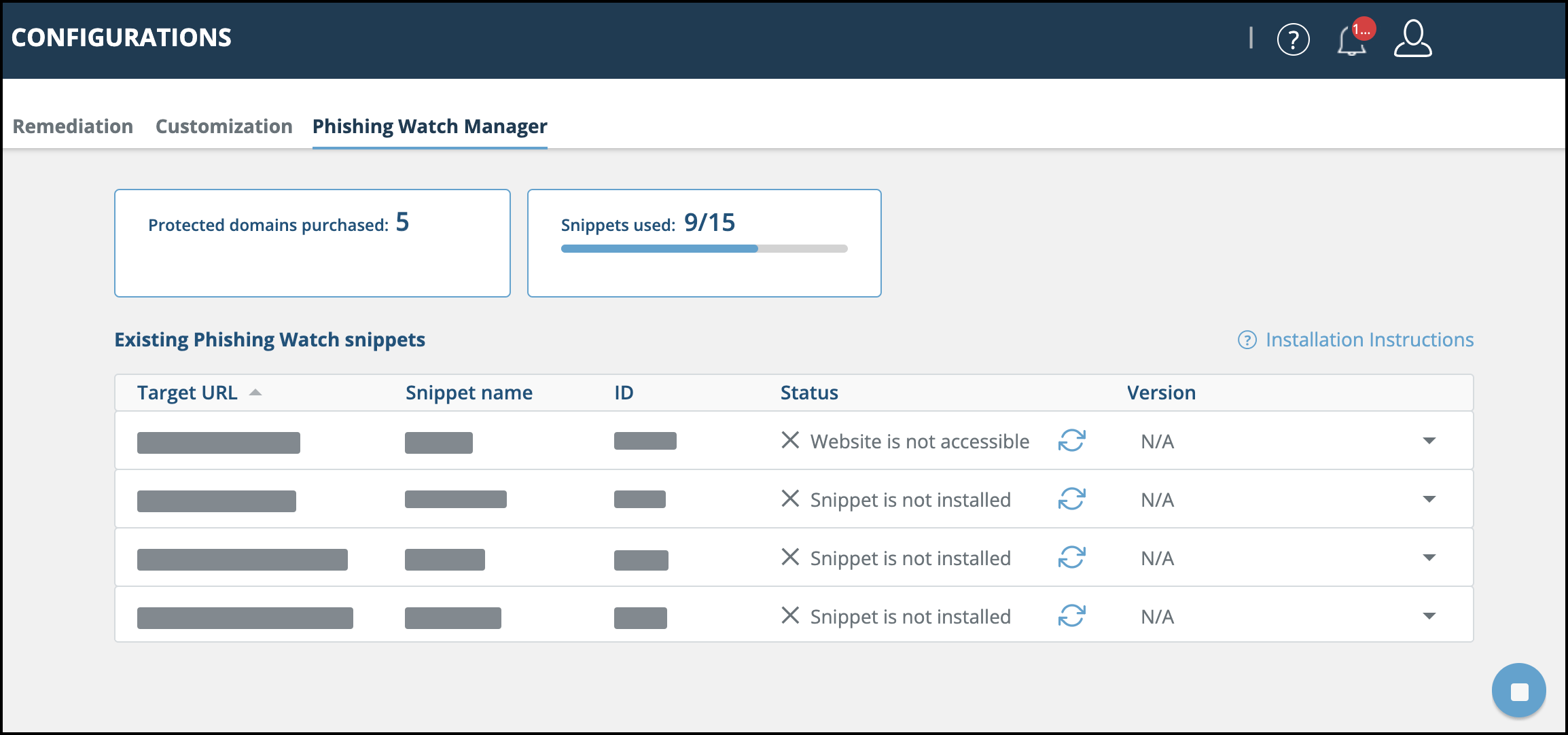
The Phishing Watch Manager shows details about protected domains and snippets:
- Protected domains purchased - The amount of domains that can be protected with the Phishing Watch feature. You can create snippets for pages within a protected domain.
- Snippets used - The total amount of unique snippets that have been created.
Create a Phishing Watch snippet
It is best practice to create a unique snippet for every web page you want to track. This granularity enables you to define different allowlisted domains for every web page so you can focus only on real results. Moreover, you will be able to monitor the status of each individual snippet so you can ensure that the service is up and running in every webpage.
To create a new snippet:
- Select * Digital Risk Protection (Threat Command) >** Configurations > Phishing Watch Manager.
- Click
 on the bottom right corner of the page.
on the bottom right corner of the page.
The Generate New Snippet dialog is displayed.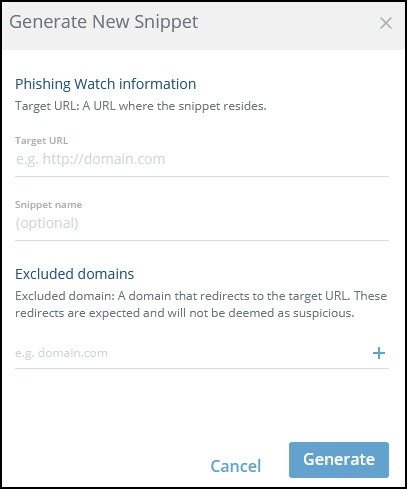
- Type the Target URL, the web page in which the snippet will be installed.
- (Optional) Type a descriptive name to easily identify this snippet.
- (Optional) Type one or more Excluded domains, domains from where the redirection originates from a trusted source.
Be sure to list all of the legitimate domains which redirect to your target URL, in order to avoid generating false positive threats. - Click Generate.
The downloading process will start automatically.
The newly created snippet is now shown in the Existing Phishing Watch snippets table.
- Repeat this process for every snippet to be generated.
After creating a snippet, it must be deployed, as described in the following section.
After a snippet is created, you can download, edit, or delete it. These options are available when you hover the pointer over the snippet line in the table.
Deploy a Phishing Watch snippet
The snippet can be deployed in the following ways:
- Within the web page source code (static deployment).
- Embedded inside known frontend code frameworks (dynamic deployment), similar to the implementation of Google Analytics (for example, Angular, React.JS, Vue.JS).
- Another option is using third-party injection services (e.g., Cloudflare, F5, Akamai). For more information, contact Customer Support.
The following installation examples show how to deploy the Phishing Watch snippet within web pages that might be used for a phishing attack. This usually includes any non-authenticated pages that contain user input elements, such as login pages, “contact us” pages, etc.
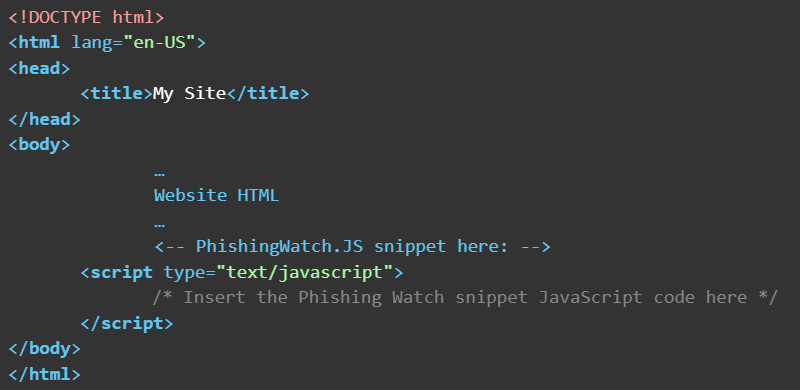
To deploy the snippet on a static website
- Following the download of the JavaScript file, copy its entire contents.
- Paste the contents before the closing </body> tag on any of your site trackable pages, as seen in the following example:
To deploy the snippet on a dynamic website
- Following the download of the JavaScript file, copy its entire contents.
- Locate the global site tag for your property.
- Paste your global site tag into its own include or component files.
- Link the include or component file so that the snippet appears before the closing </body> tag on every webpage you want to track.
The following figure illustrates an example in the Angular environment: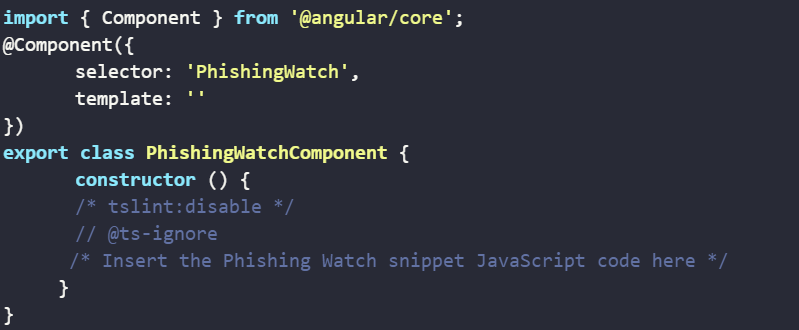
Note: the component needs to be loaded on the framework.
For more information, contact Customer Support.
Monitor Phishing Watch status
A monitoring health check is performed against each existing snippet within the provided Target URL and its status is determined accordingly. The existing snippet status is shown in the Status column of the Phishing Watch Manager page.
Tip: You can copy the target URL with the copy button in the Target URL column (visible when you hover).
To refresh the status of a Phishing Watch snippet:
- Click
 in the snippet row in the Existing Phishing Watch snippets table.
in the snippet row in the Existing Phishing Watch snippets table.
The following table describes the meaning of the Phishing Watch snippet status:
| Status | Meaning | Required Action |
|---|---|---|
| OK | The snippet is functioning correctly | No action required |
| Website is not accessible | The provided “Target URL” is inaccessible | - Check if the website within the provided “Target URL” is online- Check if the provided “Target URL” is properly formatted |
| Snippet is not installed | The snippet was not found in the provided “Target URL” | Check if the snippet is properly installed in the provided “Target URL” |
| Snippet ID mismatch | The monitoring service was expecting to monitor snippet X within the provided “Target URL”, but snippet Y was detected instead | Make sure that the correct snippet was installed in the provided “Target URL” |
| Old version | The installed snippet’s version is out of date | Download a new version using the “Download new version” button |
| Pending | The snippet has recently been created and the monitoring process needs to perform a health check | Wait for the monitoring health check to complete |
| Pending verification | Shown upon clicking the “Verify status” icon A health check is currently being performed | Wait for the monitoring health check to complete |