Dark Web Threats
The Dark Web page shows threats for the following scenarios:
- Credit cards for sale
Company credit cards that are offered for sale on the dark web. - Bot data for sale
Company compromised accounts that were harvested by bots and are offered for sale. - Black markets
Company products that are offered for sale on the dark web.
To enable threat and alert creation, you must define certain assets:
- For Credit Cards for Sale, you must define the BIN numbers asset.
- For Bot Data for Sale, you must define at least one of these assets: Domains, Brand names, Company names, External IP addresses, or Login pages.
- For Black Markets, you must define at least one of these assets: Domains, Brand names, or Company nam For more information, see Configuring Assets.
Credit card threats
Each line on the Credit Cards for Sale tab shows one credit card for sale.
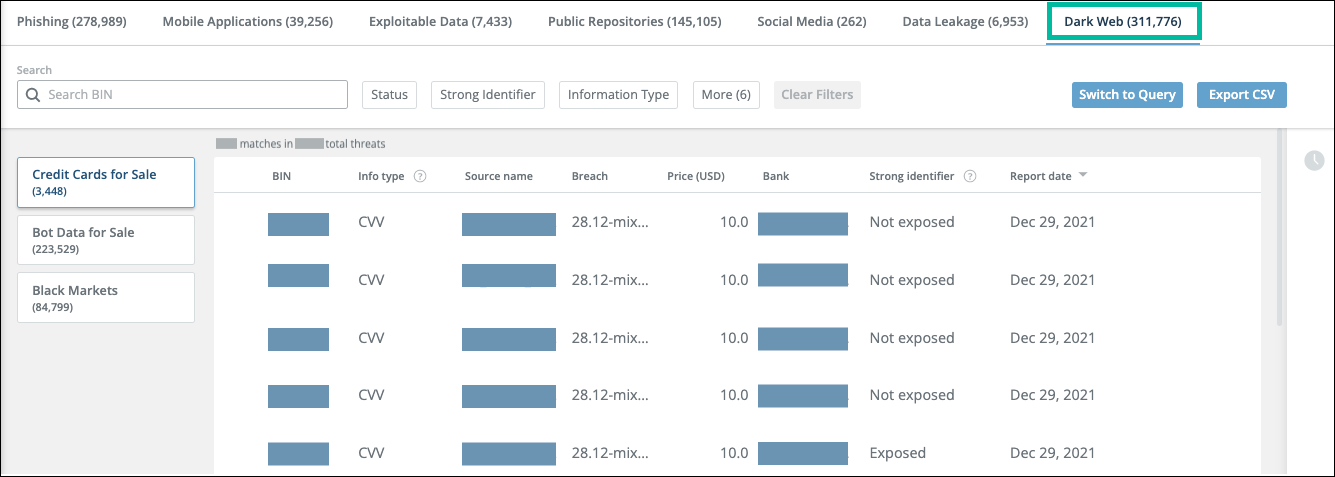
The threats are refreshed each time you open the tab, so they are shown only if they are currently a threat. By default, the threats are sorted by the date of the last report, with the most recent first. You can reverse the sort order or sort by the number of mentions.
With the Timeline function, you can see in-house threat activity (viewed a threat, etc.).
New credit Card threats are added to the page when the page is refreshed.
You can filter the view by searching, clicking the filter buttons above the table, or by using the Query Language. For more information, see Filter and search threats.
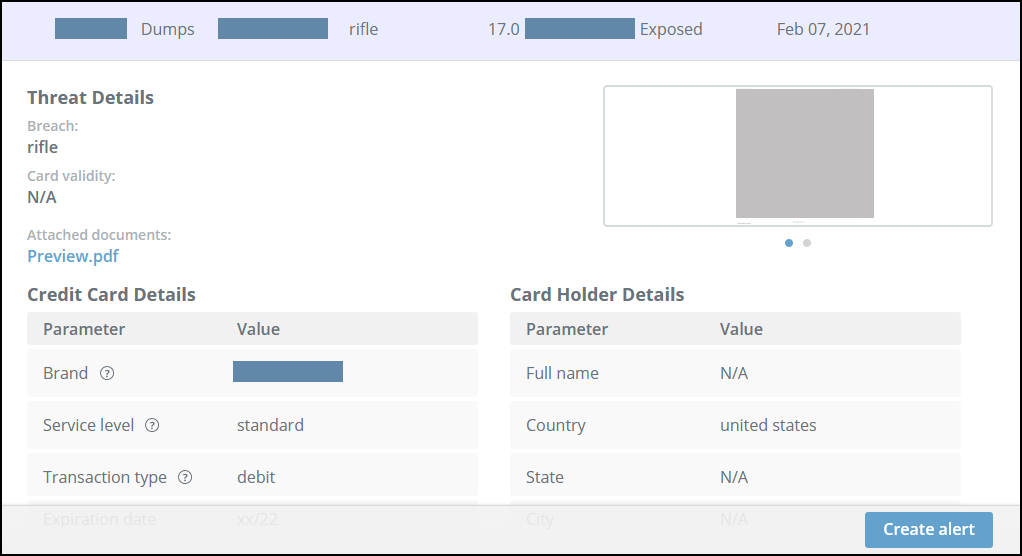
Alerts are triggered when the card for sale contains a strong indicator that can help trace the original card, such as the cardholder address or phone number.
You can use the Alert Profiler to aggregate alerts, for example, all cards found for sale in a 6-hour period will generate one alert (instead of perhaps hundreds or thousands). Each of these aggregate alerts will contain the details for all of the cards founds. For more information, see Alert Profiler.
You can use the Alert Profilerto fine-tune which threats trigger alerts.
Bot data for sale threats
Each line on the Bot Data for Sale tab shows one bot offered for sale. Each bot can contain several host URLs.
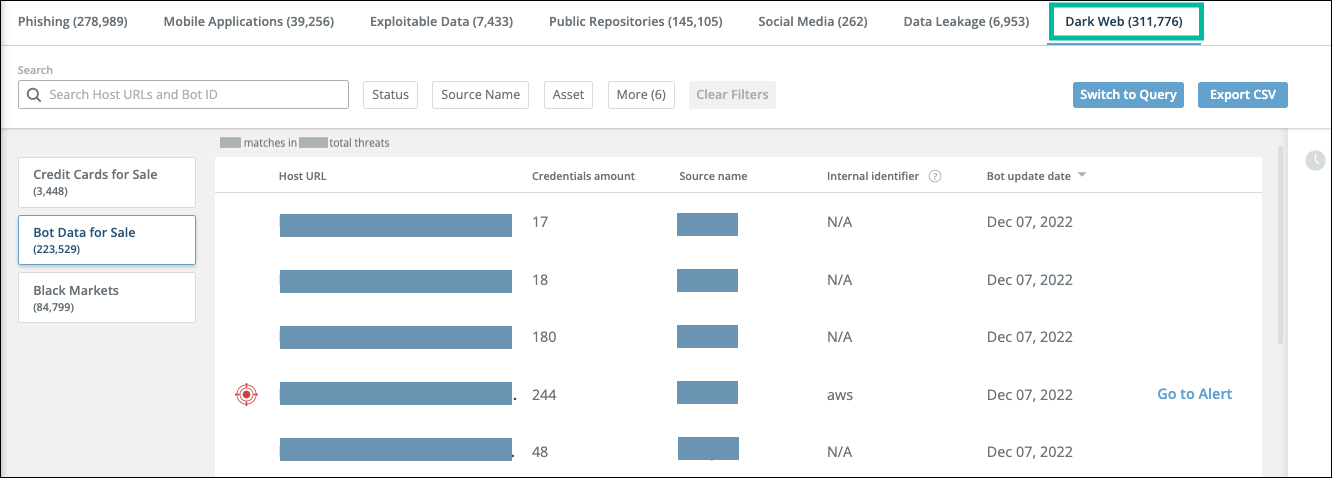
By default, the threats are sorted by the date of the last report, with the most recent first. You can reverse the sort order or sort by the number of mentions.
The Internal identifier indicates if there is evidence that the Host URL may be an internal page.
With the Timeline function, you can see in-house threat activity (viewed a threat, etc.).
You can filter the view by searching, clicking the filter buttons above the table, or by using the Query Language. For more information, see Filter and search threats.
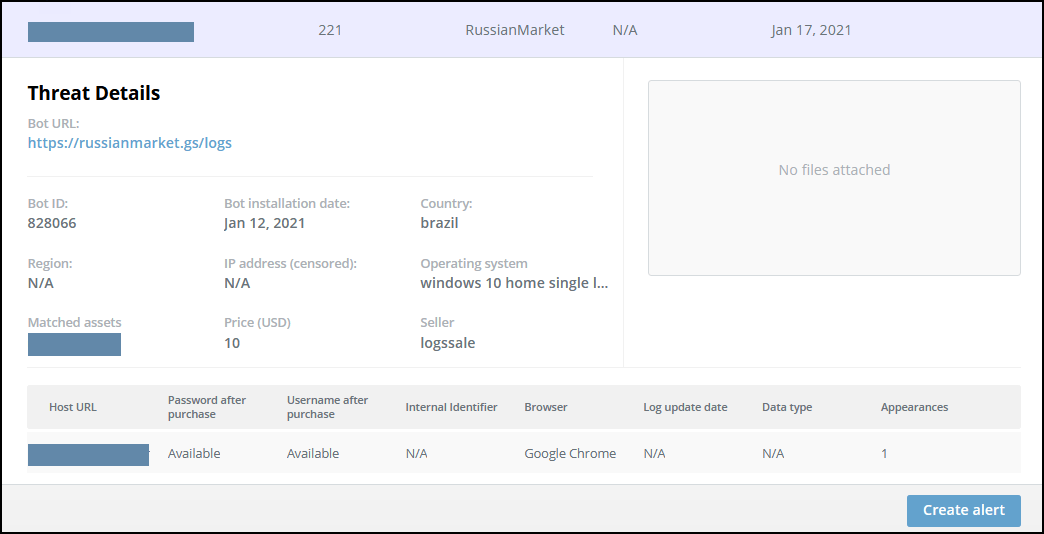
You can use the Alert Profiler to fine-tune which threats trigger alerts.
The default Alert Profiler rule generates alerts when at least one of the following conditions is met:
- There is an indication that the credentials were used in a company’s internal page.
- The host URL matched a company’s domain.
Black market threats
Each line on the Black Markets tab shows one company-related product that is offered for sale on a black market.
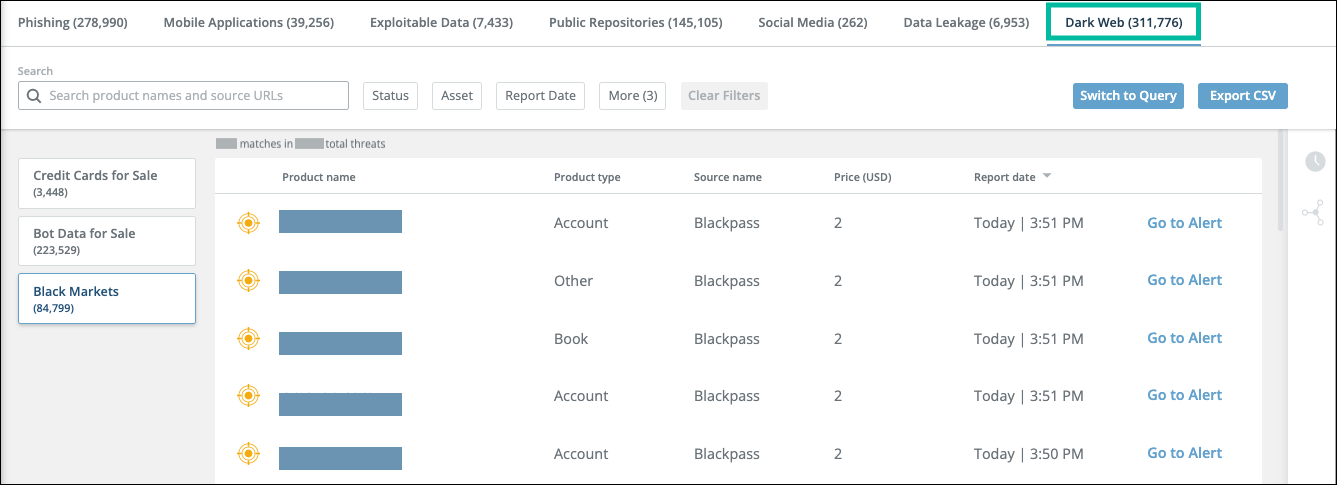
The threats are refreshed each time you open the tab, so they are shown only if they are currently a threat. By default, the threats are sorted by the date of the last report, with the most recent first. You can reverse the sort order or sort by the other columns.
With the Timeline function, you can see in-house threat activity (viewed a threat, etc.)
You can filter the view by searching, clicking the filter buttons above the table, or by using the Query Language. For more information, see Filter and search threats.
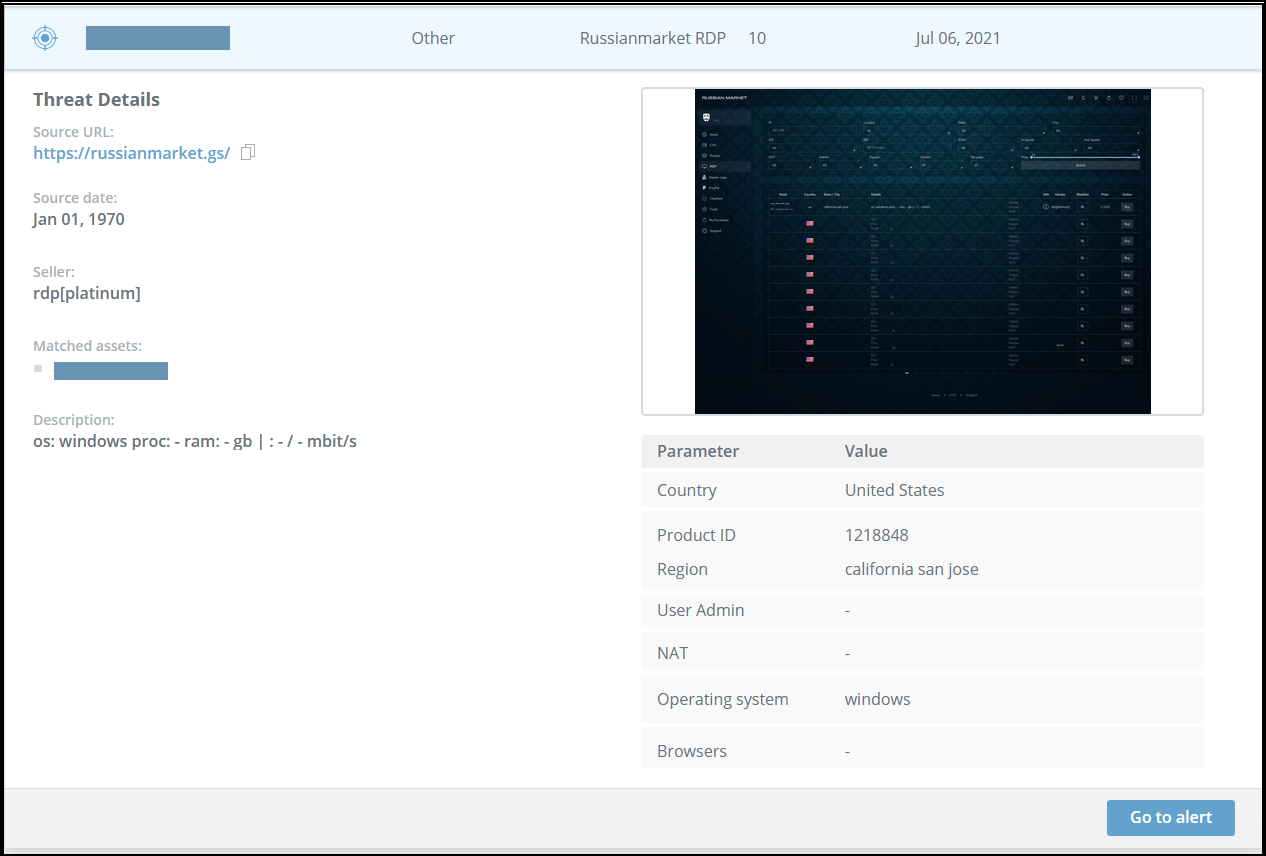
Alerts are triggered when a company asset is matched inthe product title and the product is of any of the following types: account, hacking tutorial, phishing kit, gift card, SSN/PII, database, fraud service, hacking tool, fraud tool, RDP, shell, or exploit.
In the expanded threat details, you can see:
- Product name
- Product type (e.g. account, phishing kit, hacking tool, gift card, etc.)
- Store name
- Price
- Source URL
- Source date
- Seller name
- Matched assets
- Screenshot
- Description of the product that is offered for sale
The Parameter table is dynamic and changes in accordance to the product type.
You can use the Alert Profilerto fine-tune which threats trigger alerts.