Filter and Search Alerts
You can filter and search the Alerts page with built-in filters (Basic Mode or by querying with the Digital Risk Protection (Threat Command) Query Language (Query Mode).
From each mode, you can easily switch to the other:
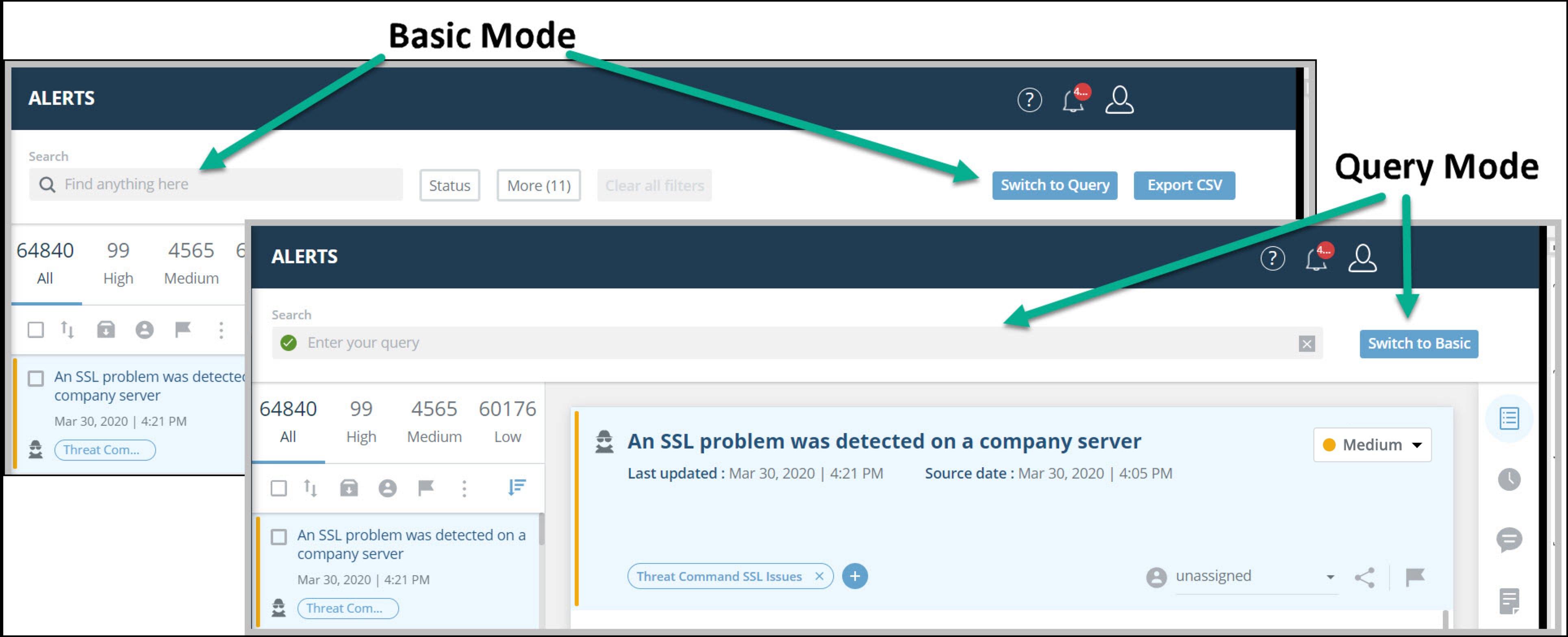
Filter the Alerts list in Basic Mode
You can filter the Alerts list to display alerts that match selected filter criteria.
To filter the Alerts list with Basic Mode:
- From the main menu, select * Digital Risk Protection (Threat Command) > Alerts**.
- If the Search bar displays a
 , you are in Basic Mode. Otherwise, click Switch to Basic.
, you are in Basic Mode. Otherwise, click Switch to Basic. - Note: If you are in Query Mode, you may need to click
 in the Search bar before you can click Switch to Basic.
in the Search bar before you can click Switch to Basic.
-
Filter the Alerts list, according to the options in the following table:
To do this Do this
| Filter alerts by severity. | Select a severity in the severity filter, on top of the Alerts list. | | Find an alert by its ID. | Type the alert ID in the Search bar. | | Show alerts in a specific status. | Click the Status filter and select statuses to show. | | Show alerts of a specific type. | Click the Type filter and select alert types to show. | | Show alerts from a specific source type. | Click the Source Type filter and select sources from which to show alerts. | | Show alerts that are flagged. | Click the Flagged filter and select whether to show only alerts that are flagged. | | Show alerts based on a specific asset. | Click the Asset filter and select assets to which alerts were matched. | | Show alerts whose source date is in a specific date range. | Click the Source Date filter and enter a date range. | | Show alerts assigned to a specific assignee or that are unassigned. | Click the Assignee filter and select which alerts to show. | | Show alerts with specific watchers. | Click the Watcher filter and select watchers. | | Show alerts with/without specific tags. | Click the Tags filter and select tags to match. | | Show alerts that were updated in a specific date range. | Click the Last Update filter and enter a date range. | | Show alerts in a specific remediation state. | Click the Remediation Status filter and select the statuses to match. | | Show alerts about which an analyst was contacted. | Click the Ask an Analyst filter and select Show only alerts with ask an analyst chat. | | Show alerts from the dark or clear web. | Click the Network Type filter and select the networks to match. | | Show alerts that were reported in a specific date range. | Click the Report Date filter and enter a date range. | | Show alerts that are associated with specific MITRE techniques. | Click the MITRE Technique filter and select techniques. | | Show all alerts | Click Clear all filters. |
The selected alerts are displayed.
Filter the Alerts list in Query Mode
You can search and filter the Alerts page using complex search queries, similar to those used in other popular tools such as Splunk and Jira, combining various data fields and logical operators to obtain nearly any desired result.
The original filters are still available in Basic Mode or you can use Query Mode to achieve results that are not available with the current filters. For example, in Query Mode you can apply several filters with a logical OR relationship between them, while with the current filtering options, there is a built-in AND relationship between different filters. You can easily select between using the query language, “Query Mode” or the existing filters, “Basic Mode.”
The intuitive query interface supports automatic suggestions and completions, making it very easy to use without needing to remember exact field names or operators.
Queries can consist of the following elements:
- Field - A word that represents a field in the Digital Risk Protection (Threat Command) Query Language. In most cases, fields correspond to alert filter names.
- Operator - A word or symbol that compares the value of the field with the value. Only results whose value matches are returned.
- Value - A value that is used to test if it matches.
- Keyword - A word or phrase that joins clauses or alters the logic of clauses or operators.
To filter the Alerts list using the Query Language in Query Mode:
- From the main menu, select * Digital Risk Protection (Threat Command) > Alerts**.
- If the Search bar displays a
 or an
or an  , you are in Query Mode. Otherwise, click Switch to Query.
, you are in Query Mode. Otherwise, click Switch to Query.
- Click anywhere in the Search bar.
The list of available fields is displayed. - Create a query by selecting or typing a combination of fields, operators, values, and keywords.
You can use the arrow and enter keys to easily select from the options in the dropdown.
Query creation is not case sensitive. - Press Enter.
- The Alerts list is filtered according to your search query.
- To cancel a query, click
 in the Search bar.
in the Search bar.
Example of a simple query:
| Field | Operator | Value | Description |
|---|---|---|---|
| Severity | = | High | Returns alerts whose severity is high. |
Examples of more complex queries:
-
“Source Type” = “Application Store” AND “Source URL” ~ “sameapk.com” AND Title ~ “Vulnerability”
This query searches for mobile application alerts, found in an application store whose URL contains “sameapk.com”, where the alert title includes the word “Vulnerability”
-
“Remediation Status” = Failed AND Assignee IS EMPTY AND (Severity != Low OR Flagged = true)
This query searches for alerts that have failed remediation, that are of some importance (high or medium severity, or flagged alerts), and are not assigned to anyone.
-
(Title ~ Password OR Title ~ “Dark Web” OR Description ~ “Exposed publicly”) AND Status IN (Open,“In Progress”) AND “Source Date” >= 03-12-2020
This query searches for alerts that contain certain keywords (such as “Dark Web” or “Exposed publicly”) in their title or description, that are not closed, and were found after March 12th, 2020.
You can use the following operators:
| Operator | Meaning | Usage | Example |
|---|---|---|---|
| = | Exactly matches | Enclose multi-word phrases in quote-marks (”). | Title = “Dark Web” |
| != | Does not match exactly | Enclose multi-word phrases in quote-marks (”). | Title != dark |
| IN | Matches any members of a list | Enclose the list items in parentheses, comma-separated. Enclose multi-word phrases in quote-marks (”). | Status IN (Open,“In Progress”) |
| NOT IN | Does not match any member of a list | Enclose the list items in parentheses, comma-separated. Enclose multi-word phrases in quote-marks (”). | Status NOT IN (Open,“In Progress”) |
| ~ | Contains | Type a string. If it’s multi-word, enclose in quote-marks (”). | Description ~ “leaked credentials” |
| !~ | Does not contain | Type a string. If it’s multi-word, enclose in quote-marks (”). | Description !~ password |
| IS | Equals | Used to find empty values (only with Assignee field), always with EMPTY. | Assignee IS EMPTY |
| IS NOT | Does not equal | Used to find non-empty values (only with Assignee field), always with EMPTY. | Assignee IS NOT EMPTY |
| > | Greater than | In date searches, means later than. Date format is MM-DD-YYYY. | ”Source Date” > 03-12-2020 |
| >= | Greater than or equal to | In date searches, means later than or equal to. Date format is MM-DD-YYYY. | ”Source Date” >= 03-12-2020 |
| < | Less than | In date searches, means earlier than. Date format is MM-DD-YYYY. | ”Source Date” < 03-12-2020 |
| <= | Less than or equal to | In date searches, means earlier than or equal to. Date format is MM-DD-YYYY. | ”Source Date” <= 03-12-2020 |
The following table describes which operators are valid for each field:
| Field | Operators | Value | Description |
|---|---|---|---|
| ”Alert ID” | = != IN NOT IN | Type an alert ID. | Find an alert by its ID. |
| ”Activity ID” | = != IN NOT IN | Type an activity ID. | Each alert action by a user has an activity ID. It can be seen when clicking an activity in the notification area (the bell icon) and seeing the ID that appears automatically in the Search bar of the Basic mode. |
| Title | = != IN NOT IN ~ !~ | Type a string. | Search for exact titles, search among multiple exact titles (using IN or NOT IN), or search for partial strings in the title. |
| Description | = != IN NOT IN ~ !~ | Type a string. | Search for exact descriptions, search among multiple exact descriptions (using IN or NOT IN), or search for partial strings in the description. |
| ”Source URL” | ~ !~ | Type a string. | Search for a string contained in the Source URL, or for keywords or strings within the Source URL. |
| Severity | = != IN NOT IN | Select alert severity. | Search for a certain severity, or not with a certain severity, or among multiple severities (using IN or NOT IN). |
| Status | = != IN NOT IN | Select alert status. | Search for a certain status, or not with a certain status, or among multiple statuses (using IN or NOT IN). |
| Type | = != IN NOT IN | Select alert type. | Search for certain types, or not of a certain type, or among multiple types (using IN or NOT IN). |
| ”Source Type” | = != IN NOT IN | Select source type. | Search for certain source types, or that do not have a certain type, or among multiple source types (using IN or NOT IN). |
| Flagged | = != | Select true or false. | Search for flagged or unflagged alerts. |
| Asset Type | = != IN NOT IN | Select asset. | Search for alerts that match or do not match a selected asset or among multiple assets (using IN or NOT IN). |
| ”Asset Name” | = != IN NOT IN ~ !~ | Type a string. | Search for alerts that match or do not match specified assets or among multiple assets (using IN or NOT IN). |
| ”Source Date” | = != > >= < <= | Type a date (MM-DD-YYYY). | Search for alerts whose source date is before, after, or equal to a certain date. |
| Assignee | = != IS IS NOT IN NOT IN | Select or type an assignee. | Search for assignees or among multiple assignees (using IN or NOT IN). You can also search for alerts that are not assigned to anyone with the value “EMPTY”, for example: “Assignee IS EMPTY” |
| Watcher | = != IN NOT IN | Type a name. | Search for alerts being watched or among multiple watchers (using IN or NOT IN). |
| Tags | = != IN NOT IN ~ !~ | Select or type tags. | Search for certain exact tags or multiple exact tags (using IN or NOT IN), or for partial strings in the tags. |
| ”Last Update” | = != > >= < <= | Type a date (MM-DD-YYYY). | Search for alerts that were last updated before, after, or equal to a certain date. |
| ”Remediation Status” | = != IN NOT IN | Select remediation status. | Search for a remediation status or multiple statuses (using IN or NOT IN). |
| ”Ask an Analyst” | = != | Select true or false. | Search for alerts for which Ask an Analyst has or hasn’t been initiated. |
| ”Network Type” | = != IN NOT IN | Select network type. | Search for specific network types or multiple values (using the IN or NOT IN). |
| ”Report Date” | = != > >= < <= | Type a date (MM-DD-YYYY). | Search for alerts whose report date is before, after, or equal to a certain date. |
| ”Leaked Email” | = != IN NOT IN ~ !~ | Type an email address, domain, or a part thereof | Search for an email address or use a wildcard (*) to search for any address from a specific email domain. This field cannot be filtered on in the Basic query. |
| ”MITRE Technique” | = != IN NOT IN | Select technique ID | Search for alerts with a specific MITRE technique assigned to them. |