Integrate a Fortinet FortiManager On-Premises Device
Configure a Fortinet FortiManager on-premises device.
The following table shows device-specific integration characteristics:
| Characteristic | Description |
|---|---|
| Method of push | All new IOCs that were discovered since the previous update are pushed to the device. |
| IOC types supported | Domains, IP addresses, and URLs. |
| IOC group limitation | All IOC types can be pulled in the same group. |
| Device IOC limit | The device is limited to 300,000 IOCs. |
Device-specific integration characteristics table
IOCs are pushed from Digital Risk Protection (Threat Command) to the device.
To integrate the device, perform these steps (described in the following sections):
- Add the device to Digital Risk Protection (Threat Command) with the virtual appliance web interface.
- Configure an IOC group whose IOCs will be pushed to the device.
Add a Fortinet FortiManager on-premises device
Use the Digital Risk Protection (Threat Command) virtual appliance to integrate the device with Digital Risk Protection (Threat Command).
Prerequisites:
- You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
- You have the credentials to access the Digital Risk Protection (Threat Command) virtual appliance web interface.
- You have the administrative credentials to access the device management console.
- All managed FortiGate firewalls are configured with the inspection engine in ‘Proxy’ mode.
- ‘Flow’ mode is not supported for this integration due to limitations in FortiGate Firewall.
- You know whether you want to push IOCs to the FortiManager Root ADOM or the Global Database ADOM.
To integrate a FortiManager device:
- From an internet browser, navigate to https://<virtual appliance IP address>
- Log in to the Digital Risk Protection (Threat Command) virtual appliance using the web access username and password.
- From the Devices page, click Devices.
- Click Add new device.
- In the Devicesscreen, set up the new device:
- Type a user-defined, unique device name (for example, FortiDemo).
- Select the FortiManager device type.
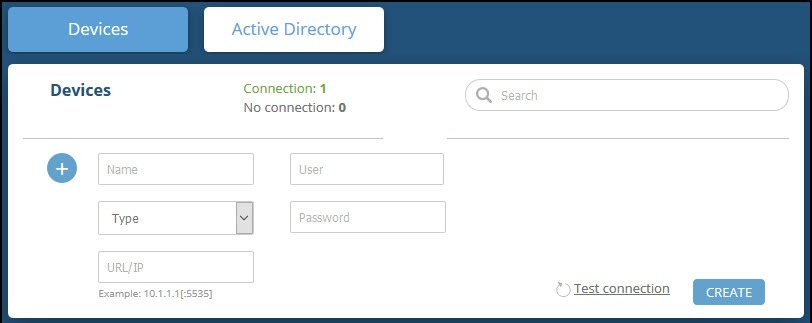
- Type values for User and Password. These should be the same values used to access the FortiManager web management console.
- Type the URL or IP address of the FortiManager machine.
- Select the FortiManager Workspace Mode:
- To push IOCs to the root ADOM, do not select Workspace Mode (default).
- To push IOCs to the Global Database ADOM, select Workspace Mode.
- (Optional) You can test the connection by clicking Test connection.
- Click Create.
- Review and approve messages.
- Verify that the new device is displayed in Digital Risk Protection (Threat Command):
- Log in to Digital Risk Protection (Threat Command) at https://dashboard.ti.insight.rapid7.com
- From the main menu, selectAutomation > Integrations. If this window is already open, refresh it by selecting Automation > Integrations from the menu. The new device is displayed in the On-Premises tab.
The following figure shows a newly added device in the Automation > Integrations window: 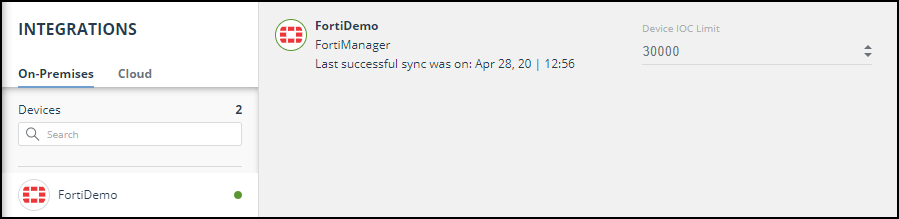
Configure an IOC group to push IOCs to the device
Once the FortiManager device has been added and is synching with the Digital Risk Protection (Threat Command) virtual appliance, it is ready to receive IOCs that are pushed from Digital Risk Protection (Threat Command). IOCs are pushed by creating an IOC group for this device in Digital Risk Protection (Threat Command).
When creating IOC groups, you can choose whether the matched IOCs should be monitored or blocked in the FortiManager device. This choice is transmitted to the device, together with the IOC identification.
Create the IOC group, as described in Create an IOC group.
Verify that IOCs are being pushed to the device
You can verify that IOCs are being pushed to the FortiManager device.
To verify IOCs:
- From the Digital Risk Protection (Threat Command) main menu, select Automation > Integrations.
- Select the device.
- On an IOC group of the device, click the Information icon:
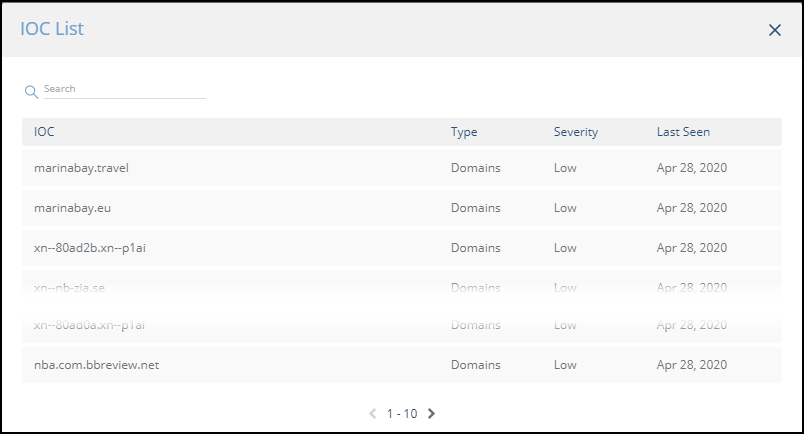
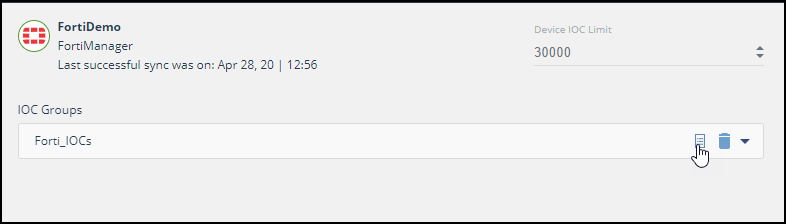 The IOCs in the group are displayed:
The IOCs in the group are displayed:
- In the FortiManager management console, select Policy & Objects > Object Configurations > Security Profiles > Web Filter.
Digital Risk Protection (Threat Command) IOCs are displayed in the User-Defined section under the following name format (in lower case):
<DeviceName_IOCGroupName> for example, fortidemo_forti_iocs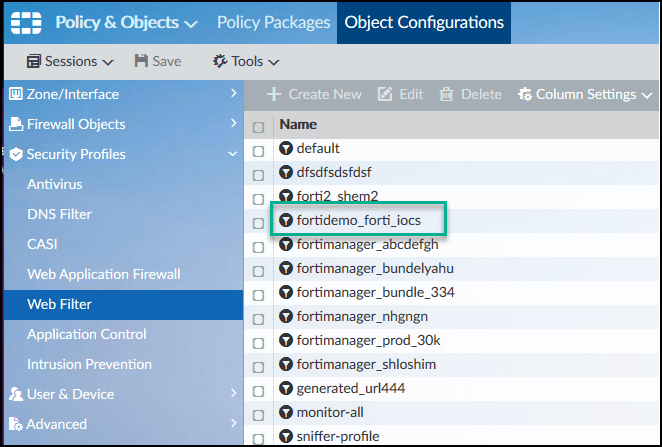
Ensure that you are in the correct ADOM.
Double-click the IOCs listing to see the IOCs: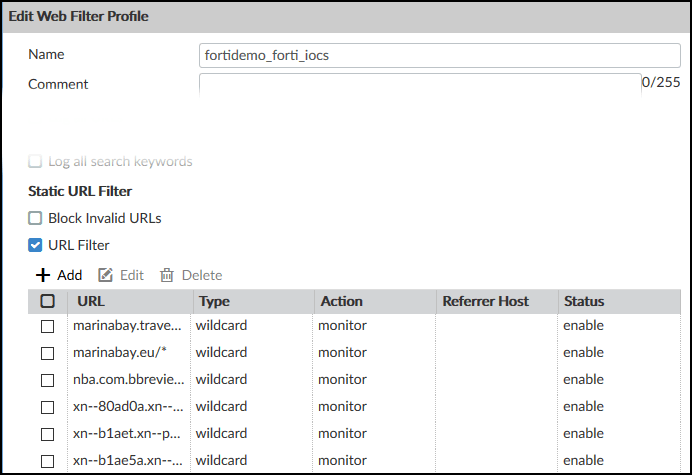
Note that the “monitor” action was passed from Digital Risk Protection (Threat Command).