MISP Cloud Device
Configure a MISP cloud device to pull IOCs from Digital Risk Protection (Threat Command).
The following table shows IOC pull characteristics:
| Characteristic | Description |
|---|---|
| Method of pull | All new IOCs that were discovered since the previous update are pulled. If IOCs were deleted from the MISP, and they are part of a new event, they will be pulled again. |
| IOC types | Domains, URLs, email addresses, IP addresses, and file hashes (MD5, SHA-1, and SHA-256). All IOC types can be together in the same IOC group. |
| Device IOC limit | The device is limited to 50,000 IOCs. |
IOCs are pulled, together with the following Rapid7 enrichment data:
- First seen
- Last seen
- Source name
- Source confidence
- Severity
- Alert ID
- User tags
- System tags
- Threat actors
- Campaigns
- Associated malware families
You must first add the device to Digital Risk Protection (Threat Command) and then configure the device to pull IOCs from Digital Risk Protection (Threat Command).
Add a MISP cloud device to Digital Risk Protection (Threat Command)
Add a cloud device to Digital Risk Protection (Threat Command).
Prerequisites
- You have the credentials to access the device.
- You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
To add a cloud device to Digital Risk Protection (Threat Command):
- Log in to Digital Risk Protection (Threat Command) at https://dashboard.ti.insight.rapid7.com
- From the main menu, select Automation -> Integrations.
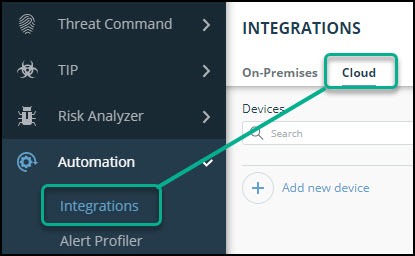
- From the Integrations page, click Cloud.
- Click Add new device.
- In the Add New Cloud Device dialog, type a user-defined name for the device. The name can contain a maximum of 50 letters, spaces, numbers, and underscores.
- Select the Device type.
The default device IOCs limit is displayed. - (Optional) You can change the IOCs limit.
- Click Add.
- To verify that the new device is added, refresh the Automation > Integrations page.
The new device is added to the cloud integrations device list. Next to the device name, there is a red dot, indicating that communication has not yet been established. The dot will change to green when the device is synchronized. If the device cannot synchronize for more than 48 hours, an email warning is sent to the account administrator.
Configure a MISP cloud device to pull IOCs
After a device has been added, you must enable the pulling of IOCs by the MISP device from Digital Risk Protection (Threat Command).
Before you begin, ensure:
-
You have the device login credentials.
-
The device has been added.
-
You have administrative credentials to access Digital Risk Protection (Threat Command) with a subscription to the Automation and TIP modules.
-
An IOC group for this device exists in Digital Risk Protection (Threat Command).
Creating IOC groups is described in Create an IOC group -
You have the Digital Risk Protection (Threat Command) account ID and appliance key, as described in API key, account ID, and appliance key.
To configure a MISP cloud device:
-
From Digital Risk Protection (Threat Command), copy the IOC group URL into MISP:
- From the main menu, select Automation > Integrations.
- From the Cloud device list, select the MISP device.
- Click the link icon to the far right of the device IOC group.
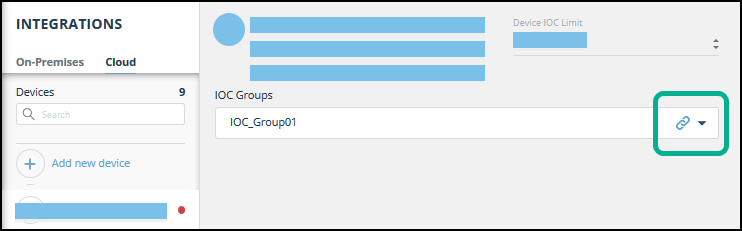
The IOC Group URL dialog is displayed.
- From the IOC Group URL dialog, copy the URL.
-
Log in to the MISP device.
-
Choose Sync Actions > List Feed, then select Add Feed.
-
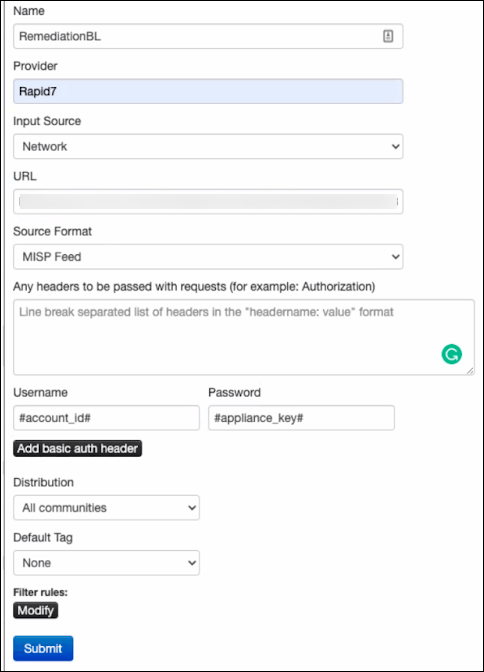
Configure the feed:
- Select Enabled.
- Enter a feed name and the provider name (for example, Rapid7).
- For Input Source, ensure that Network is selected.
- In the URL field, paste the IOC Group URL.
- Click Add Basic Auth.
- Type the Digital Risk Protection (Threat Command) account ID and appliance key.
-
Trigger event fetching:
- Click Add basic auth header.
In the List Feeds, all events should be listed as being pulled after some time. - To trigger event pull, click Fetch all events :
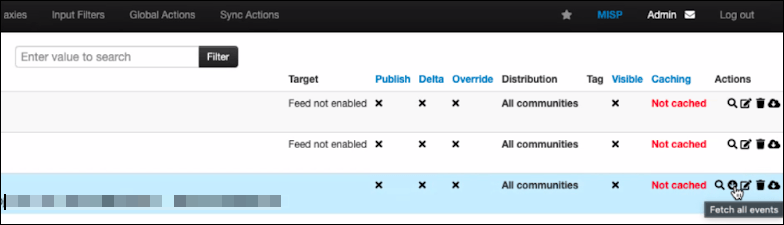
Events will start to pull into MISP as MISP events.
The name of the MISP event will indicate the IOC group name and the current date, for example: #IOC_group_name - #current_date
- Click Add basic auth header.