Public Repositories Scenario Rule Conditions
This topic describes the conditions that you can use to create rules and the default rules provided for the public repositories scenario.
Public repositories includes the following scenarios:
Each scenario has its own conditions and default rules.
Leaked secrets
Leaked secrets - conditions The following table describes the conditions that you can use to create rules. When using a regular expression, don’t surround the expression with quotation marks.
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | identified/did not identify | An exposed secret | Did the Digital Risk Protection (Threat Command) internal algorithm identify an exposed secret? |
| Asset name | in/not in | Select assets | Does the found repository contain selected assets from Company name, Brand name, Domain, Public repository queries, or Public repositories? |
| Asset tags | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Days since the commit | ==, !=, >=, <=, >, < | User will type # of days since commit was deployed | Was the secret committed to a public repository within a defined time frame? |
| Developer email | is/is not | ”email address” | Was the secret committed to a public repository by a developer with a specific email address? |
| Developer email | in/not in | ”Regex list” | Was the secret committed to a public repository by a developer whose email address contains a pattern, such as an email domain (can be expressed by regular expression)? |
| Developer name | is/is not | ”exact name” | Was the secret committed to a public repository by a developer with a specific name? |
| File content | contains/does not contain | Select assets | Does the file contain the secret, together with selected assets from Company name, Brand name, Domain, or Public repository queries assets? |
| File path | is/is not | ”URL address” | Was the secret found in a specific public repository source path? |
| Matched subdomain | in/not in | Type subdomains to search for | Does the found repository contain specific subdomains? |
| Proximity (in lines) between the secret and the Company Names asset | ==, !=, >=, <=, >, < | Type a number of lines | Was the number of lines of code between the Company Names asset and the secret a specific number? |
| Proximity (in lines) between the secret and the Domains asset | ==, !=, >=, <=, >, < | Type a number of lines | Was the number of lines of code between the Domains asset and the secret a specific number? |
| Proximity (in lines) between the secret and the Public repository queries asset | ==, !=, >=, <=, >, < | Type a number of lines | Was the number of lines of code between the Public repository queries asset and the secret a specific number? |
| Repository full name | is/is not | ”exact name” | Was the secret found in a public repository whose full name exactly matches? |
| Repository full name | in/not in | ”regex list” | Was the secret found in a public repository whose full name contains a pattern (can be expressed as a regular expression)? |
| Repository name | is/is not | ”exact name” | Was the secret found in a public repository whose name exactly matches? |
| Repository name | in/not in | ”regex list” | Was the secret found in a public repository whose name contains a pattern (can be expressed as a regular expression)? |
| Secret type | is/is not | Dropdown | Does the secret type (such as API key or AWS key) match a selected type? |
| Secret value | contains/does not contain | Dropdown | Does the secret contain selected assets from Company name, Brand name, Domain, or Public repository queries assets? |
| Secret value | in/not in | ”regex list” | Does the secret value contain a pattern (can be expressed as a regular expression)? |
| Source | is/is not | ”GitHub” | Was the secret found in a GitHub public repository? |
| Source | is/is not | ”GitLab” | Was the secret found in a GitLab public repository? |
Leaked secrets - default rule The following table lists the rules that are provided to get you started quickly.
| Rule name | Description of match | Default state |
|---|---|---|
| Exposed Secret Key - Default Detection Rule | A company secret on GitHub or GitLab was detected by the internal Digital Risk Protection (Threat Command) detection algorithm. | Enabled |
Matched secrets Alert Profiler examples This example shows one way to use the Alert Profiler.
Problem : Company developers may be uploading company secrets to a public repository on GitHub.
Solution : Create a rule that will alert whenever someone from the company commits a secret to a public repository on GitHub.
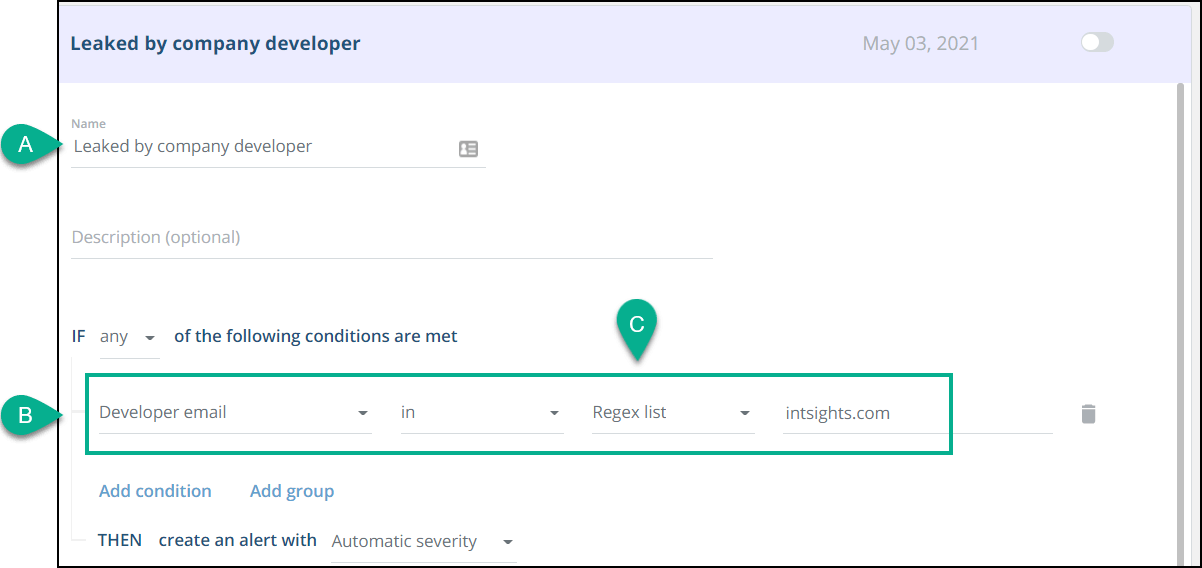
Customize alert triggering with the Alert profiler :
- Add a new rule.
- Add the Developer email condition.
- Add the company domain Regex to match commits by company employees.
Asset mentions
The following table describes the conditions that you can use to create rules. When using a regular expression, don’t surround the expression with quotation marks. Asset mentions - conditions
| Features | Operator | Value | Description |
|---|---|---|---|
| Detection algorithm | identified/did not identify | An exposed exact asset mention | (Default) Did the Digital Risk Protection (Threat Command) internal algorithm identify an exposedexactasset mention? |
| Detection algorithm | identified/did not identify | An exposed substring asset mention | Did the Digital Risk Protection (Threat Command) internal algorithm identify an exposed asset mention, even if not exact? |
| Asset name | in/not in | Code mentions | Does the asset mention contain a matched Code mentions asset? |
| Asset name | in/not in | Domains | Does the asset mention contain a matched Domains asset? |
| Asset tags | in/not in | Select tags | Are any of the threat’s matched assets tagged with any of the specified tags? |
| Matched Subdomain | in/not in | Subdomain name list | Does the asset mention contain a company subdomain? |
| Repository creator description | contains/doesn’t contain | regex list | Was the asset mention found in a repository that was created by a user whose description contains a pattern (can be expressed as a regular expression)? |
| Repository creator nickname | contains/doesn’t contain | regex list | Was the asset mention found in a repository that was created by a user whose nickname contains a pattern (can be expressed as a regular expression)? |
| Repository description | contains/doesn’t contain | regex list | Was the asset mention found in a repository whose description contains a pattern (can be expressed as a regular expression)? |
| Repository full name | contains/doesn’t contain | regex list | Was the asset mention found in a repository whose full name contains a pattern (can be expressed as a regular expression)? |
| Repository full name | is/is not | exact name | Was the asset mention found in a repository whose full name exactly matches a specific name? |
| Repository name | contains/doesn’t contain | regex list | Was the asset mention found in a repository whose name contains a pattern (can be expressed as a regular expression)? |
| Repository name | is/is not | exact name | Was the asset mention found in a repository whose name exactly matches a specific name? |
Asset mentions - default rule
The following table lists the rule that is provided to get you started quickly:
| Rule name | Description of match | Default state |
|---|---|---|
| Asset Mention - Default Detection Rule | A Code mention asset type was found in a repository:. | Disabled |
By default, Asset mentions alerts are disabled. When you enable this rule, the alerts are automatically aggregated daily, by file:
- If multiple assets were found multiple times in the same code file - 1 threat will be created.
- If a single asset was found multiple times in multiple code files - multiple threats will be created.
You can modify aggregation options as described in Aggregate Alerts.