Website Redirect Detection
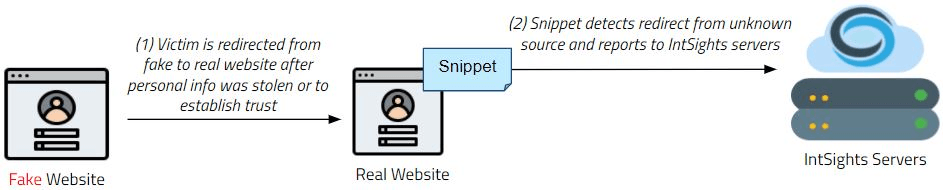
A common practice of a phishing website attack technique is to redirect users to the official website after stealing their login credentials, financial details, or personally identifiable information (PII), so as not to raise suspicion. The Phishing Watch detects scenarios where users are being redirected to the official company website from a suspicious or unknown domain.
The following steps illustrate how the Phishing Watch works when a website redirect is made:
- The Phishing Watch JavaScript snippet is created and embedded in the website.
- The snippet launches each time the webpage is loaded or refreshed.
- When the snippet identifies a non-formal, suspicious website (by inspecting the URL of the webpage), it reports the suspicious URL back to Digital Risk Protection (Threat Command) servers in a stealthy, low footprint manner.
- The Digital Risk Protection (Threat Command) phishing detection algorithm determines whether the reported website could be used for phishing.
- The snippet’s allowlist excludes cases where it may be operating on the organization’s official website.