Using the Rapid7 Agent (Insight Agent) with Vulnerability Management (InsightVM)
As an Vulnerability Management (InsightVM) subscriber, you can access several feature-rich cloud capabilities powered by the Insight platform. To complement the on-premises scanning infrastructure that you may already have, you can also install the Rapid7 Agent (Insight Agent) across your network for the purpose of vulnerability assessment.
Why use the Rapid7 Agent (Insight Agent) with Vulnerability Management (InsightVM)?
The Rapid7 Agent (Insight Agent) best addresses the vulnerability assessment needs of assets that have the following characteristics:
Assets running from remote locations
You may have assets in your organization that operate outside of your company network for long periods of time and regularly connect to the internet in different locations. While a traditional scan requires target assets to be present on your network in order to be assessed, the Rapid7 Agent (Insight Agent) can send vulnerability data to the Command Platform (Insight Platform) as long as the asset has an internet connection. Whether the asset is on your company network or on its assigned user’s home network, the Rapid7 Agent (Insight Agent) has you covered.
Assets with heavy scanning restrictions
Some of your assets may serve in roles that are too business-critical to absorb the load of a traditional scan during standard hours of operation. This means you often have to find a suitable scanning window for these assets, which can be difficult depending on the role they play. Rapid7 Agents (Insight Agents) are considerably less burdensome by comparison because the actual assessment process is the responsibility of the Insight platform.
Assets restricted by credentials
Traditional scans rely on configured credentials in Vulnerability Management (InsightVM) in order to authenticate to the target asset, which yields more comprehensive vulnerability results. Since Rapid7 Agents (Insight Agents) monitor the asset from within, their assessments are functionally authenticated already, thus sparing you from having to configure credentials at all.
Where can I view my Rapid7 Agents (Insight Agents) after I've deployed them?
The Agent Management view in your Insight platform account page is the central location for monitoring all the Rapid7 Agents (Insight Agents) you have deployed across your organization.
See the Agent Management Help page to learn how to access this view.
Rapid7 Agent (Insight Agent) and Vulnerability Management (InsightVM) scans
For the most accurate view of your environment, we recommend using agent scans for authenticated (local) assets and unauthenticated engine scans for unauthenticated (remote) assets.
Scan capability comparison
The Rapid7 Agent (Insight Agent) and Scan Engine are designed to complement each other. If both scan the same asset, the Security Console automatically recognizes the data and merges the results.
| Rapid7 Agent (Insight Agent) | Unauthenticated scan (Scan Engine) | Authenticated scan (Scan Engine) | Scan Assistant (Scan Engine) | |
|---|---|---|---|---|
| Speed | Fastest | Faster | Fast | Fastest |
| Credentials | N/A | Not required | Required | N/A |
| Scheduled scans | No | Yes | Yes | Yes |
| Scan blackouts | No | Yes | Yes | Yes |
| Scan Templates | N/A | Yes | Yes | Yes |
| Collection | Regularly | During scan | During scan | During scan |
| Type of check | Local only | Remote only | Local, remote, and policy | Local, remote, and policy (CIS only) |
Usage scenarios
| Scan source | Common usage |
|---|---|
| Scan Engine | |
| Rapid7 Agent (Insight Agent) | |
| Scan Engine and Rapid7 Agent (Insight Agent) on the same asset |
Using the Scan Assistant
The Scan Assistant provides a more secure way to scan your assets, removes the need for administrative credential management, consumes much fewer resources, and significantly decreases the time to complete for policy scans. The Scan Assistant can be leveraged to expand and extend enterprise vulnerability coverage as it is an extension of the Scan Engine that’s complementary to the Rapid7 Agent (Insight Agent) and compatible with the Vulnerability Management (InsightVM) cloud platform.
Better security
The Scan Assistant leverages Transport Layer Security (TLS) with elliptic curve asymmetric encryption (ECDSA) and advanced encryption standard (AES) and digital certificates to create a trusted secure channel between the Scan Engine and the Scan Assistant.
No credential management
The Scan Assistant provides the only access needed for you to run an authenticated scan. There is no need for privileged Admin account access to assets. This means that the Scan Assistant can perform scans without the hassle of managing credentials to assets.
You do not need to use SSH, CIFS, WMI or other traditional account-based credentials alongside the Scan Assistant, since the Scan Assistant acts as your credential type. Note that the Scan Engine prioritizes the Scan Assistant over other credential types when it is present.
Efficiency
The Scan Assistant is lightweight and efficient. It consumes minimal memory and CPU resources. Once installed, the Scan Assistant provides Registry and File System (Windows) or Command Execution (Linux) services on the local asset. The Scan Assistant only runs when scans are initiated.
Faster policy scans
Due to the large amounts of data being collected, policy scans usually take a while to complete. With the Scan Assistant, policy scan time completion improves vastly.
Usage scenarios
| Scenario | How the Scan Assistant Helps |
|---|---|
| Authenticated scan credentials are difficult to administer | The Scan Assistant uses digital certificates instead of traditional administrative credentials |
| Need more control over site parameters | The Scan Assistant does not require Internet connectivity |
| Concerns about agent resource utilization for mission critical assets | The Scan Assistant is only active during scans initiated by the Scan Engine |
| Need granular control over assessment parameters for particular assets | The Scan Assistant responds to specific scan parameters defined by the Console to the Scan Engine |
| Need to accelerate completion times for vulnerability and policy scans | Compared to traditional authenticated scans, the Scan Assistant will be faster for vulnerability scans and orders of magnitude faster for policy scans |
Complementary scanning
If you deploy Scan Engines and Rapid7 Agents (Insight Agents) together to assess your assets for vulnerabilities, you can enable complementary scanning to do the following:
| Use case | Value | Required credentials |
|---|---|---|
| To gain an external perspective of remote access vulnerabilities | Get the external perspective by identifying remote access vulnerabilities that the devices might be exposed to | Scan Engine: Unauthenticated (remote) scan does not require elevated credentials Rapid7 Agent (Insight Agent): None |
| To complete assessments more quickly and improve performance | Allows you to skip checks that the Scan Engine knows the Rapid7 Agent (Insight Agent) is running, increasing efficiency. Stress on the Security Console is reduced since the Scan Engine won’t need to produce as many results for integration | Scan Engine: Authenticated scan (local) requires root permission Rapid7 Agent (Insight Agent): None |
Requirements
The following requirements must be satisfied for complementary scanning to be enabled:
- Your asset must be running Rapid7 Agent (Insight Agent) version 2.7.17 or later.
- Highest permissions are required. Depending on your operating system, you must have Administrative or Root credentials.
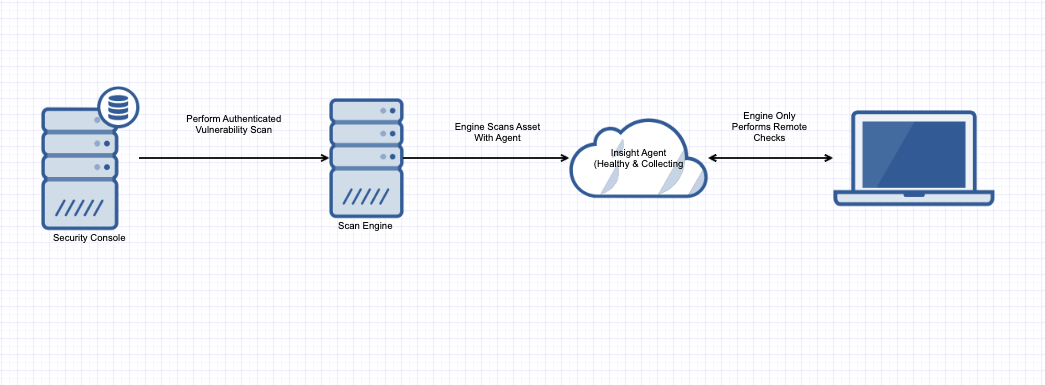
How does complementary scanning work?
The Rapid7 Agent (Insight Agent) keeps a record of the vulnerability assessments it runs for the asset on which it is installed. When complementary scanning is enabled, your Scan Engine consults this record to determine if running authenticated vulnerability checks is necessary. As long as the last Rapid7 Agent (Insight Agent) assessment was successful and ran within the normal data collection schedule, the Scan Engine skips all authenticated vulnerability checks for that asset.
Complementary scanning does not affect the Rapid7 Agent (Insight Agent)
Enabling complementary scanning only affects what actions the Scan Engine will be responsible for during a scan job. The feature itself will not direct an Rapid7 Agent (Insight Agent) to collect new data if the Scan Engine determines that the last agent assessment did not run successfully, or if the agent did not collect new data as scheduled.
Enable complementary scanning
This feature is available for all scan templates that have the Vulnerabilities check type enabled. Enable complementary scanning by adjusting your scan template configuration:
- In the Security Console, click the Administration tab in your left menu.
- In the Scan section, click Scans > Scan Templates > Manage scan templates.
- Select and open the scan template you want to configure by clicking its name link.
- On the Scan Template Configuration page, under Types of Checks, select the Vulnerabilities check box > click the Vulnerability Checks tab.
- In the Check Configuration section, select the Skip checks performed by the Rapid7 Agent (Insight Agent) check box.
- Click Save.
Learn more about the Rapid7 Agent (Insight Agent)
Rapid7 Agents (Insight Agents) are an important part of any Vulnerability Management (InsightVM) deployment, and even more so if your organization also subscribes to SIEM (InsightIDR) or Log Management (InsightOps) . For this reason, Rapid7 continually develops and maintains a dedicated documentation set for all Rapid7 Agent (Insight Agent) related resources.
Check out the Rapid7 Agent (Insight Agent) help pages to learn more about the following topics:
- Overview information, including the types of data that the Rapid7 Agent (Insight Agent) collects and how the agent software updates
- Comprehensive requirements, including supported operating systems, network configuration, and application settings
- Complete download and install instructions for both Rapid7 Agent (Insight Agent) installer types
- Mass deployment guidelines
- Advanced configuration options
- Common troubleshooting solutions