Access AWS Resources with EC2 IAM Roles
You can use an Amazon Elastic Compute Cloud (EC2) instance within your AWS environment to securely create connections between your SIEM (InsightIDR) Collector and your AWS services without relying on IAM Keys or IAM Users. This process involves installing the SIEM (InsightIDR) Collector on an AWS EC2 instance and designating a role for that server instead of relying on IAM Keys.
When you use SIEM (InsightIDR) to add AWS event sources, the Collector can use its role permissions rather than the IAM Key to create a secure connection.
To utilize this secure communication method for your SIEM (InsightIDR) Collector:
- Configure an IAM Policy for AWS-related event sources
- Configure an IAM Role for AWS-related event sources
- Create an EC2 Instance configured for the same roles
- Install your SIEM (InsightIDR) Collector on the EC2 instance
- Manage AWS Related Event Sources
Configure IAM Policy
To configure the IAM policy:
- Log in to your AWS Console.
- From the “Services” tab, select IAM.
- From the left menu, select the Policies page.
- Click the Create Policy button at the top of the page.
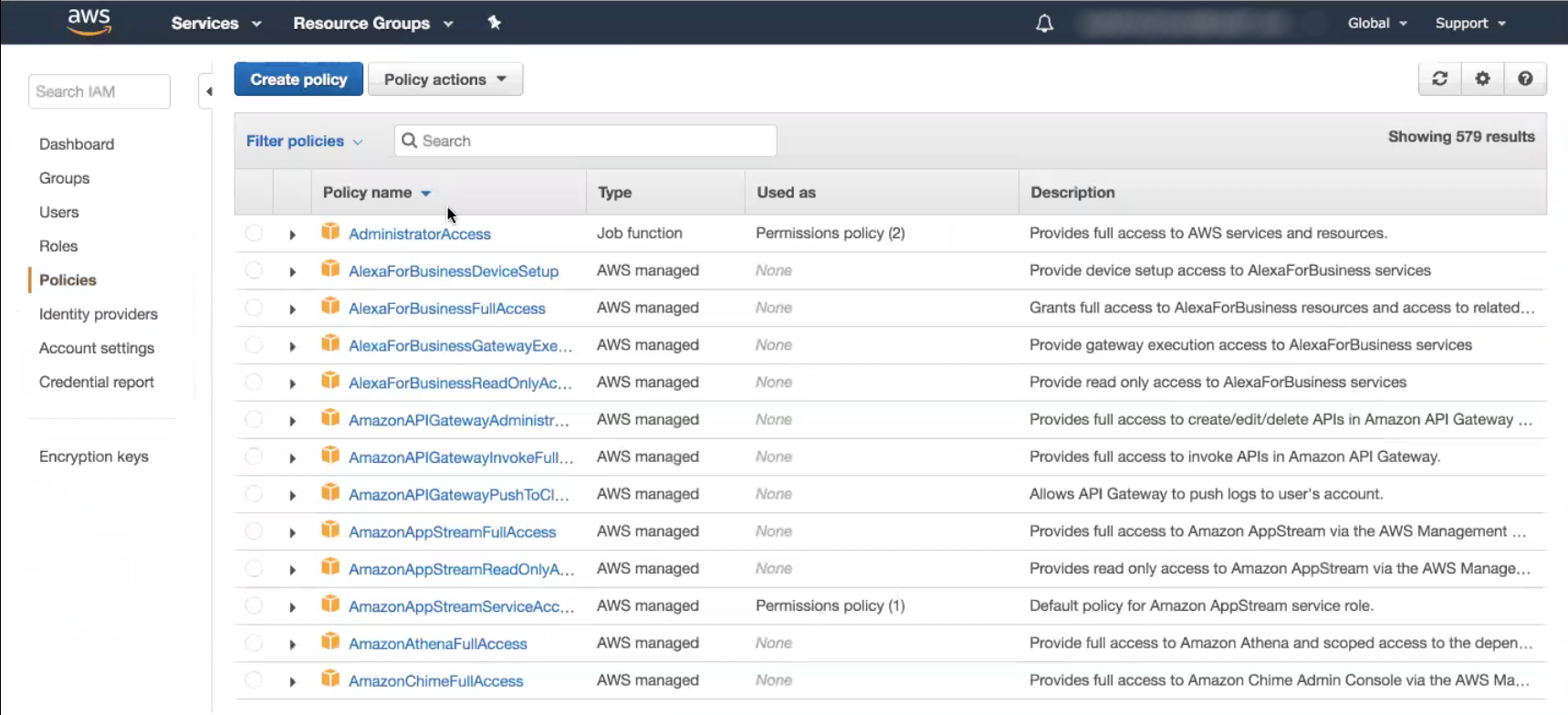
- Select the JSON tab.
- Copy and paste the Policy IAM from the “Event Source” help page.
- For example, the AWS CloudTrail help page.
- Enter the relevant information for your organization and AWS account.
- Click the Review Policy button.
- In the “Name” field, enter a name for your IAM policy.
- Click the Create Policy button.
- On the “Policy” page, click the Refresh icon at the top right of the page.
Create the IAM Role
To create the IAM role:
- From the left menu, select the Roles page.
- Click the Create Role button.
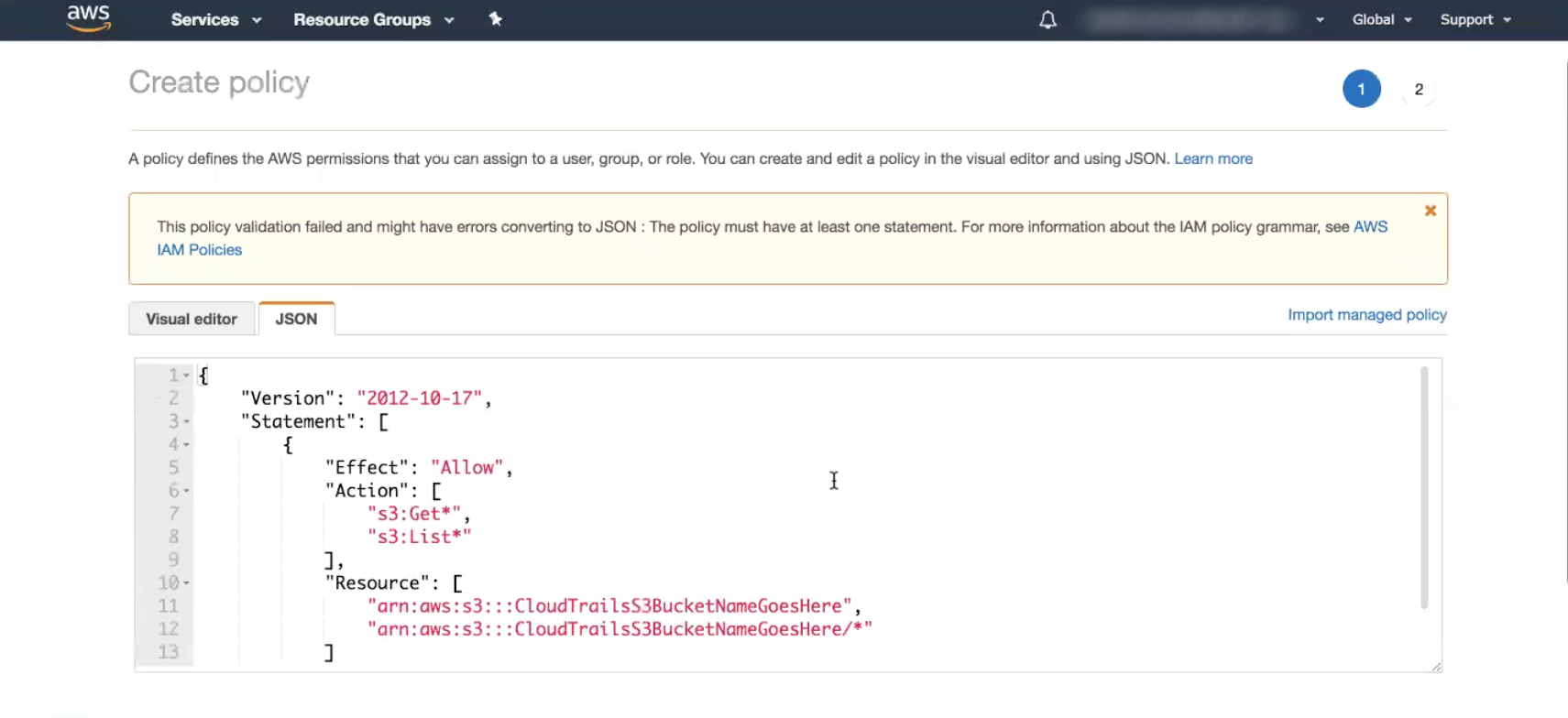
- In the “Select type of trusted entity” section, select the AWS Service option.
- In the “Choose the service that will use this role” section, select the EC2 option.
- Click the Next: Permissions button.
- In the search bar, enter the name of the policy you created in previous steps, and click the checkbox to the right of the policy.
- Click the Next: Tags button.
- Click the Next: Review button.
- In the “Name” field, enter a name for your IAM Role.
- Click the Create Role button.
- On the “Roles” page, click the Refresh icon at the top right of the page.
Read more about IAM roles here: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/iam-roles-for-amazon-ec2.html
Create an EC2 Instance
To create an EC2 Instance:
- In your AWS Console, select the Services tab at the top left of the page.
- Select the EC2 page under the “Compute” section.
- Click the Launch Instance button.
- On the “Choose an AMI” page, find the OS of the Collector you want to install the EC2 instance on and click the Select button.
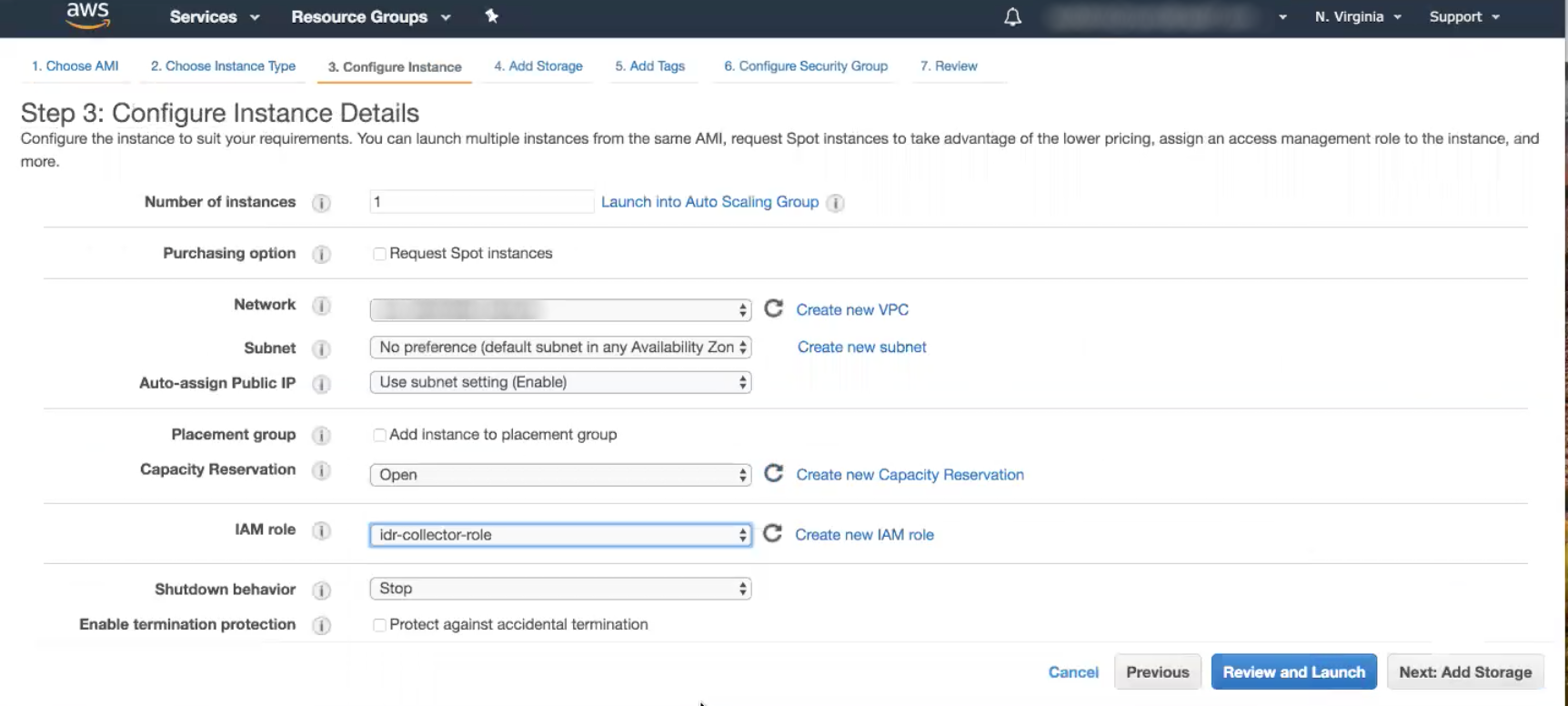
- Click the Next: Configure Instance Details button.
- In the “IAM Role” section, find and select the IAM Role you previously configured.
- Click the Review and Launch button.
- On the “Instance” page, you will see the details of the EC2 instance you just created. Copy the “IPv4 Public IP” address.
Install the Collector on the EC2 Instance
To install the Collector on your EC2 instance:
- Open the command prompt and SSH into your newly created EC2 instance using the copied IP address.
- Download the Collector installer file onto your machine and then copy the installer from the download location onto your EC2 instance with the
scpcommand. - Use the following commands to install the Collector on your EC2 instance, changing to match your OS and the AMI package OS type:
chmod +x InsightSetup-Linux64.sh
sudo ./InsightSetup-Linux64.sh- Follow the text prompts of the Installer.
For more information about this process, read the AWS EC2 documentation here: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/AccessingInstancesLinux.html
Manage AWS Event Sources
After you install the Collector onto your EC2 instance, any of your AWS-related event sources running on this Collector can use the permissions of the IAM Role.
To make these changes:
Update the IAM Role Permissions
- In your AWS Console, select Roles from the left navigation menu.
- Find the IAM Role that you created using the search bar.
- Click the arrow icon to expand the various options, and select the Edit Policy button.
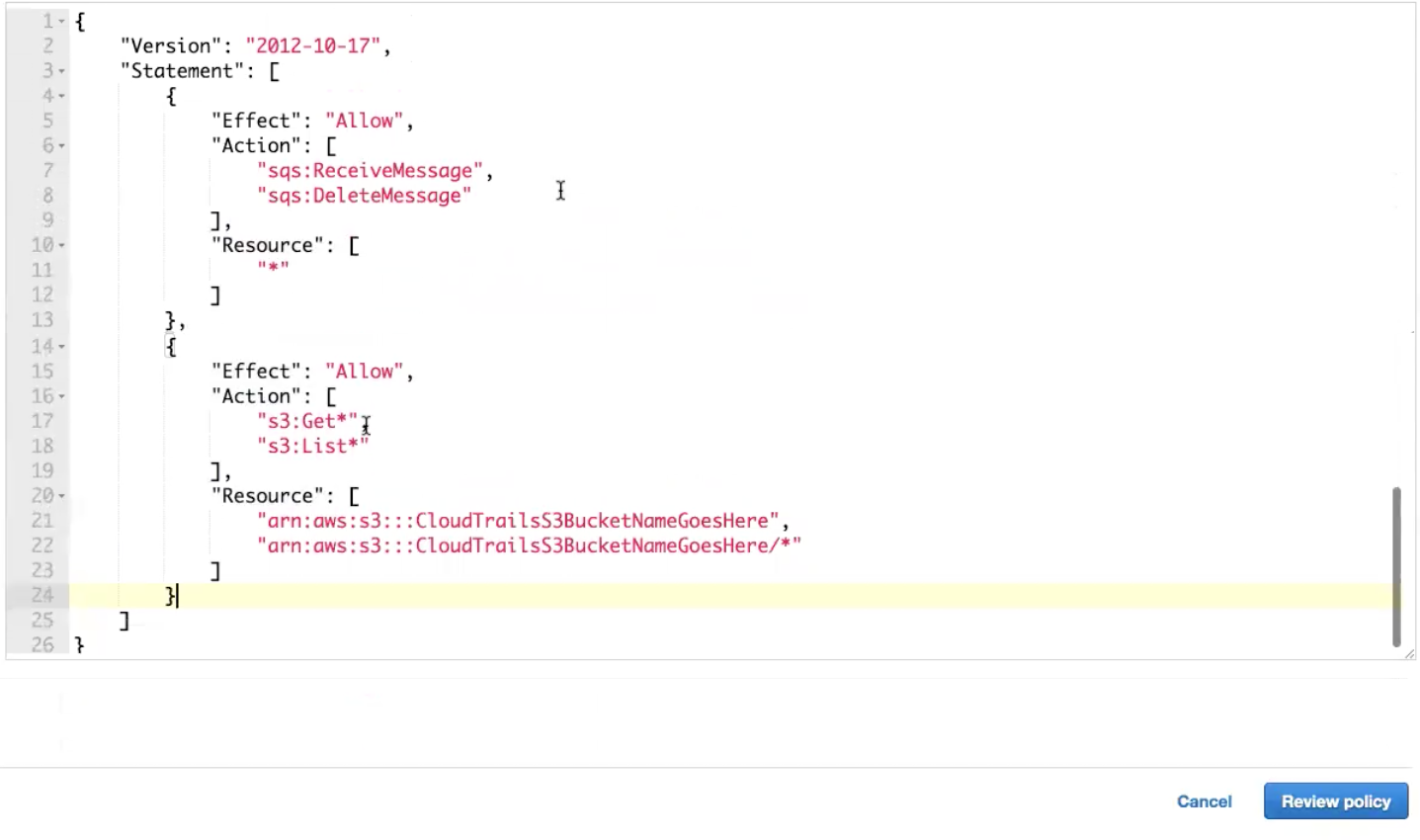
- Select the JSON tab.
- Add in the new JSON block as a new JSON statement and add in the appropriate information.
- Click the Review Policy button.
Add an AWS Related Event Source
You can configure the following AWS related event sources:
Then, complete the following to add an event source:
- From your SIEM (InsightIDR) dashboard, select Data Collection on the left hand menu
- At the top right of the page, select the dropdown that says “Setup Event Source” and then choose Add Event Source
- Select the appropriate icon for the AWS event source.
- AWS CloudTrail is a Cloud Service
- AWS GuardDuty is a Third Party Alert
- AWS SQS is a Custom Log collection method
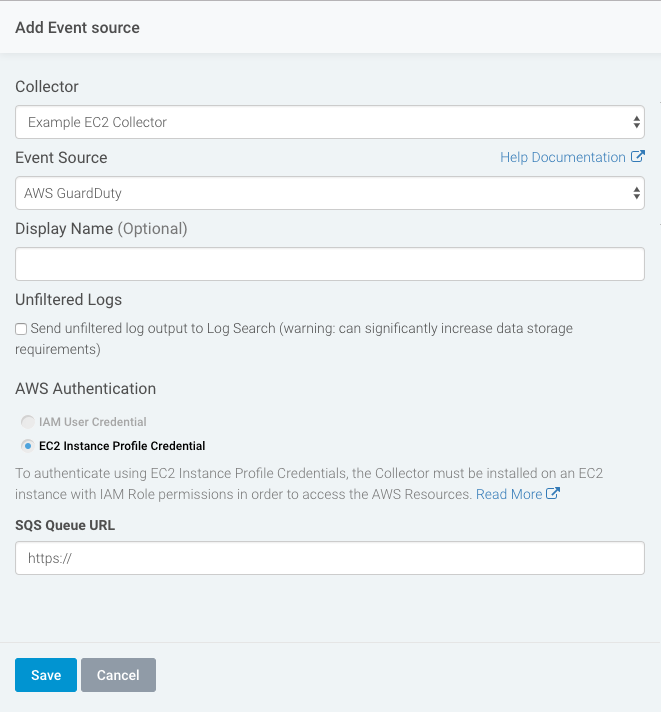
- Select the Collector you configured that is hosted in the EC2 instance.
- Select the AWS event source. It is optional to name this event source.
- If applicable, choose to send unfiltered logs.
- Under “AWS Authentication,” select the EC2 Instance Profile Credential option.
- Configure the remaining steps of the AWS event source.
- Click the Save button.
Update AWS Related Event Sources
If you have an existing AWS event source that is currently using an IAM Key, you can switch the event source to use the IAM Role instead.
To update any previously configured AWS event source:
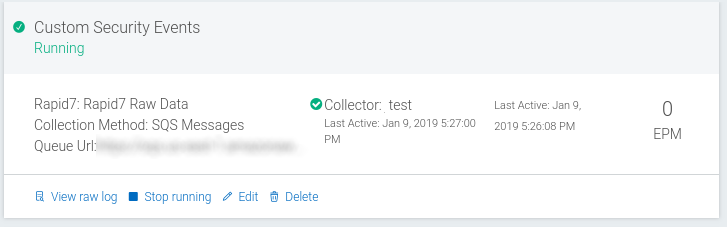
- Stop the event source in SIEM (InsightIDR). Go to Data Collection > Event Sources and find your event source. Click the Stop Running button.
- Create the Collector using the IAM Roles on an EC2 instance using the steps from earlier sections.
- Create a new event source on the new Collector with the same name. This allows the new event source to write new logs to the same log set, instead of creating a new log set in Log Search.
- Configure the new AWS event source with these changes:
- Choose the Collector installed on the EC2 instance. If you select this option without setting up an EC2 instance, you will see the following error message on your Collector: “can’t retrieve credential from the EC2 service.”
- Under “AWS Authentication,”select the EC2 Instance Credentials option.
- Update the rest of the event source settings with information from the original event source.
- Confirm that the new event source successfully writes new logs and runs without error.
- Delete the old event source from SIEM (InsightIDR). This will not remove the historical logs from SIEM (InsightIDR) log search.