Microsoft Windows Defender Antivirus
Microsoft Windows Defender Antivirus is anti-malware software that protects against software threats. SIEM (InsightIDR) automatically collects Microsoft Windows Defender Antivirus events from deployed agents on Windows endpoints. By default, legacy UBA detection rules generate notable events for Windows Defender events. If you would like to configure these detection rules, navigate to Detection Rules > Legacy UBA Detection Rules, and locate the Virus Alert rule.
Microsoft System Center Endpoint Protection Events
If you are using Microsoft System Center Endpoint Protection (SCEP) and the events are written to the Windows Defender Antivirus operational log, then these events are collected in the same manner for Microsoft SCEP as for Windows Defender.
How it works
On all Windows endpoints where the Rapid7 Rapid7 Agent (Insight Agent) is installed, the agent collects the log entries from the Defender Antivirus operational Windows event log. You can view this event log on a Windows host with the Event Viewer under Applications and Services Logs > Microsoft > Windows > Microsoft Defender Antivirus > Operational.
You can read more about this Microsoft Windows event log at: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-antivirus/troubleshoot-microsoft-defender-antivirus#windows-defender-antivirus-event-ids .
If the Rapid7 Agent (Insight Agent) finds new events being written to this Windows event log, then the Rapid7 Agent (Insight Agent) will collect them and send them to SIEM (InsightIDR). There is no event source to add and no configuration required in SIEM (InsightIDR).
View your logs in SIEM (InsightIDR)
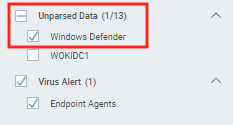
Windows Defender logs flow into different log sets depending on the event. Windows Defender events that are not recognized by the Rapid7 Agent (Insight Agent) are sent to the Unparsed Data log set. The Rapid7 Agent (Insight Agent) recognizes certain event codes and sends them to SIEM (InsightIDR) where they flow into the Virus Alert log set.
Event codes that flow into the Unparsed Data log set
1001, 1002, 1003, 1004, 1005, 1009, 1010, 1011, 1012, 1013, 1014, 1120, 1150, 1151, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2010, 2011, 2012, 2013, 2020, 2021, 2030, 2031, 2040, 2041, 2042, 3002, 3007, 5000, 5001, 5004, 5007, 5008, 5009, 5010, 5011, 5012, 5100, 5101
To view these events, click Log Search > Unparsed Data.
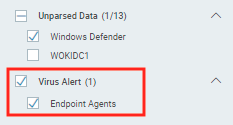
Event codes that flow into the Virus Alert log set
1006, 1007, 1008, 1015, 1116, 1117, 1118, 1119
To view these events, click Log Search > Virus Alert.
Example input log
{
"timestamp": "2020-07-02T18:07:00.006Z",
"asset": "xyz",
"user": "abc",
"source_address": "xyz",
"account": "system",
"risk": "TrojanDropper:VBS/Swrort.A",
"action": "No Action",
"file_path": "containerfile:_C:\\Windows\\SysWOW64\\config\\systemprofile\\AppData\\Local\\Microsoft\\Windows\\INetCache\\IE\\fHrHNHk8t[1].asp; file:_C:\\Windows\\SysWOW64\\config\\systemprofile\\AppData\\Local\\Microsoft\\Windows\\INetCache\\IE\\fHrHNHk8t[1].asp->(SCRIPT0001)",
"action_status": "Successful",
"error_code": "0x00000000",
"error_description": "The operation completed successfully. ",
"source_json": {
"sourceName": "Microsoft-Windows-Windows Defender",
"eventCode": 1117,
"computerName": "XYZ",
"sid": "S-1-5-18",
"isDomainController": false,
"eventData": {
"severityName": "Severe",
"unused2": null,
"sourceName": "%%818",
"executionId": "1",
"detectionUser": "NT AUTHORITY\\SYSTEM",
"typeId": "0",
"errorCode": "0x00000000",
"categoryName": "Trojan Dropper",
"signatureVersion": "AV: 1.319.590.0, AS: 1.319.590.0, NIS: 1.319.590.0",
"preExecutionStatus": "0",
"productVersion": "4.18.2006.10",
"unused4": null,
"actionId": "9",
"errorDescription": "The operation completed successfully. ",
"unused": null,
"unused5": null,
"state": "1",
"data": [],
"executionName": "%%813",
"additionalActionsString": "No additional actions required",
"actionName": "%%887",
"unused6": null,
"typeName": "%%822",
"detectionId": "{1E0D6418-A6A4-4214-B97D-68D25C126C89}",
"severityId": "5",
"detectionTime": "2020-06-22T19:36:50.493Z",
"threatId": "2147653574",
"originId": "1",
"productName": "%%827",
"remediationUser": null,
"threatName": "TrojanDropper:VBS/Swrort.A",
"statusCode": "1",
"postCleanStatus": "0",
"statusDescription": null,
"categoryId": "37",
"sourceId": "3",
"engineVersion": "AM: 1.1.17200.2, NIS: 1.1.17200.2",
"unused3": null,
"path": "containerfile:_C:\\Windows\\SysWOW64\\config\\systemprofile\\AppData\\Local\\Microsoft\\Windows\\INetCache\\IE\\fHrHNHk8t[1].asp; file:_C:\\Windows\\SysWOW64\\config\\systemprofile\\AppData\\Local\\Microsoft\\Windows\\INetCache\\IE\\fHrHNHk8t[1].asp->(SCRIPT0001)",
"processName": "processName",
"originName": "%%845",
"fwlink": "https://go.microsoft.com/fwlink/?linkid=37020&name=TrojanDropper:VBS/Swrort.A&threatid=2147653574&enterprise=0",
"additionalActionsId": "0"
},
"timeWritten": "2020-07-02T18:07:00.006792800Z"
}
}