Troubleshooting Active Directory
This documentation covers troubleshooting scenarios and solutions for Active Directory. They can be divided into:
-
Active Directory event source displays an error state
-
Active Directory event source is running, but does not receive any events
How to check EPM and error states for Active Directory
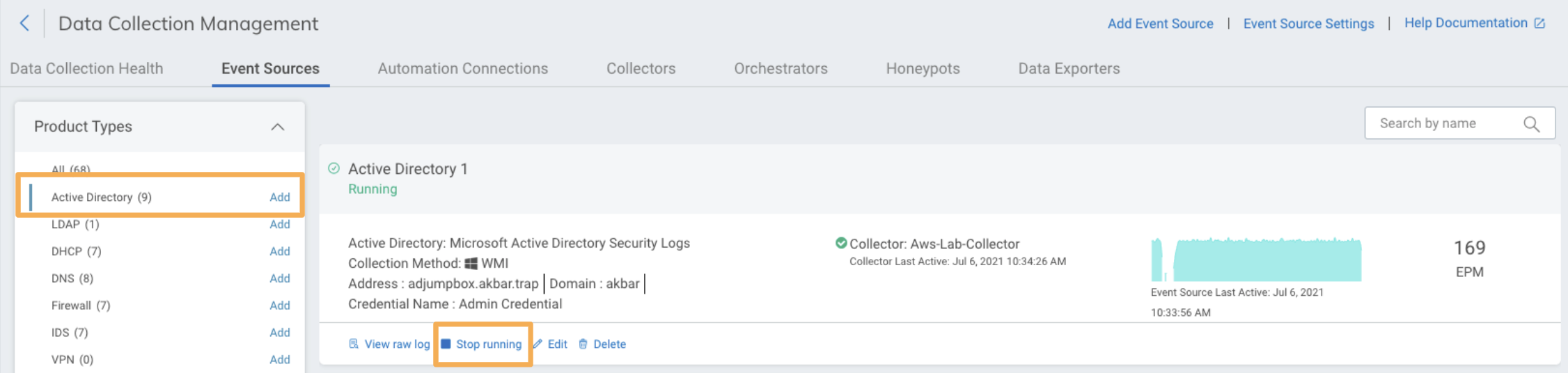
Once Active Directory is set up, you can check if it is receiving data. You can also check if it displays an error:
-
Go to Data Collection > Event Sources.
-
On the filter options to the left, click on Active Directory under Product type.
-
See the EPM (events per minute) number on the right for each Active Directory event source. If the EMP display 0 events, it means that Active Directory is not receiving events.
-
You can also check the status below the name of the event source: it can be ‘Running’ or display an error state.
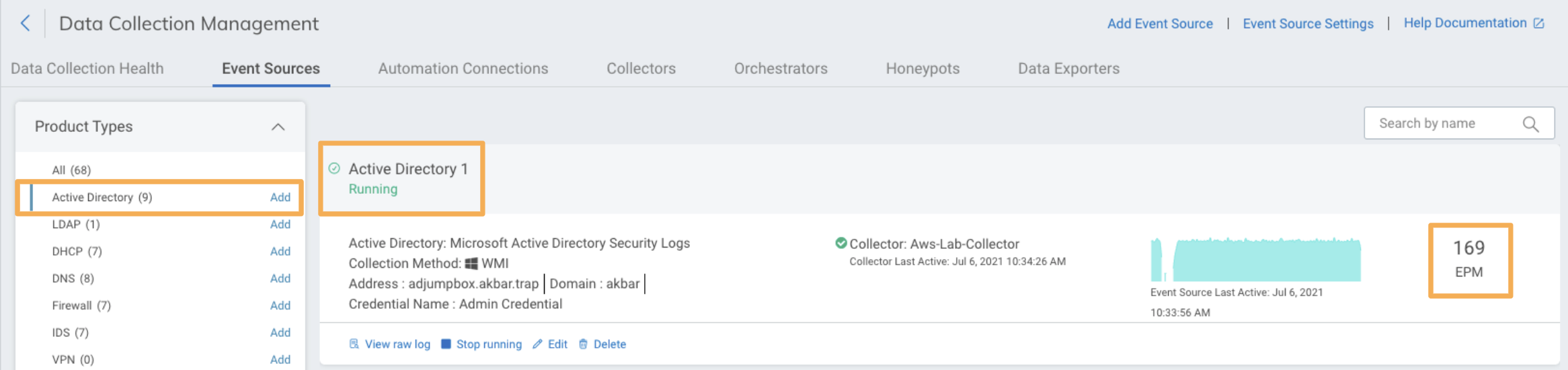
The image below shows an Active Directory event source correctly running, with no error state. As the EMP number shows, it is collecting events.
Active Directory event source displays an error state
If Active Directory displays an error state, you can review the scenarios below and take action.
Connection Refused Error
This error is the result of the Collector being unable to reach the domain controller designated in the Server field of the event source configuration. Make sure you are using a routable IP address or fully qualified hostname in this field. If the server name is correct, then use the following steps to troubleshoot.
- Confirm the IP address or fully qualified hostname matches a domain controller in your environment.
- Confirm the Collector is able to route to the domain controller.
- Confirm there are no routing rules preventing the Collector and domain controller from communicating over ports 135, 139, 445, TCP 49154 and TCP 49155.
Unable to Get Current Time Error
Message not found for errorCode: 0xFFFFFFFF
This is the result of the specified account successfully accessing the domain controller, but the DC may not have WMI enabled or configured properly. This may also show up as an exception code (e.g. 0x80041003). In this situation, troubleshoot to see if WMI access is available.
Test WMI Rights
- On the domain controller, run
wmimgmt. - Right click WMI Control (Local) > Properties > Security tab.
- Open root and highlight
cimv2. - Click Security and confirm the rights:
- Execute Methods
- Enable Account
- Remote Enable
- If a WMI browsing tool is available from the Collector, you should now be able to connect and browse
cimv2. - If you do not have a WMI browser, you can skip this testing step. Only obtain a WMI browser if further troubleshooting is needed.
Troubleshoot by Testing DCOM
- On the domain controller, run
dcomcnfg.exe. - Under Component Service, open Computers.
- Right click My Computer > Properties > COM Security tab.
- Under Launch and Activation Permissions, click Edit Limits.
- Confirm Remote Launch and Remote Activation are enabled.
Troubleshoot by Reviewing WMI logs
The WMI logs are extremely useful and detailed. They can be found under the Event Log, in Applications and Services Logs/Microsoft/Windows/WMI Activity.
If you continue to receive errors with the collector about not being able to read time or similar issues, it is likely a WMI permission issue. The collector logs combined with the WMI logs on the server make it pretty easy to pinpoint missing WMI permissions.
Active Directory Event Source is running, but has 0 EPM
Check the status of your Active Directory event source from Data Collection > Event Sources. If EPM displays 0 (meaning that you are getting no events) and the status of that event source is ‘Running’ (no error message is displayed to indicate that something is wrong), you can see review the following scenarios.
Service Account is not in the Domain Admins group
You need to set up a Service Account and add it to the Domain Admins group to use Active Directory.
It is a common mistake to use an account that does not have admin rights. This causes that the Domain admin account is not sufficiently provisioned to authenticate from the Collector to the Domain Controller.
If you prefer to set up Active Directory without a Service Account, you can review the Active Directory documentation for suitable alternative options.
Audit Policy
If you notice that you are not getting specific events from Active Directory, you should check your Audit Policy.
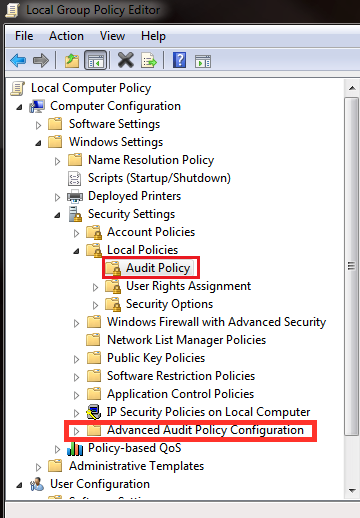
When configuring the Group Policy for Windows Logging, please note that implementing both the regular (legacy) Audit Policy settings and Advanced Audit Policy settings will cause unexpected outcomes due to conflicts between similar settings in the two groups of policy settings. In order to ensure Advanced Audit Policy settings override the regular Audit Policy settings:
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
- Enable the override policy, i.e., Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings.
Advanced Audit Policy Configurations are only compatible with Windows Vista or later. It is recommended to leverage the Advanced Audit Policy whenever possible because it has over 65 settings compared to the legacy having 8 and allows for more controls and additional visibility. It also unlocks several features including:
- Honey Files
- File Integrity Monitoring
- File Access Activity Monitoring
Note that the Advanced Audit Policy Configuration is located in a different section than Group Policy in Audit Policy.
Read about Active Directory and audit policy
The Active Directory documentation includes information about the monitored events, and also a section on how the audit policy is related to the possibility to send unparsed logs.
Duplication with the Rapid7 Agent (Insight Agent)
To collect the domain controller Security log events, use either the Active Directory event source or the Rapid7 Agent (Insight Agent). Using both may result in duplicate events being collected.
To check for duplication, go to Log Search. Select Asset Authentication under Log Sets.
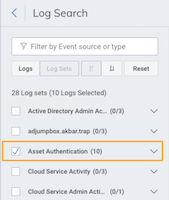
You can also use the Filter by Event source or type search option to look for Endpoint.
The Rapid7 Agent (Insight Agent) is one of the available options to get security logs from the domain controllers (all options are described in the documentation for Active Directory). Each one has different specifications and limitations. Read the specifications for each option and analyse which one you prefer.
If you prefer to collect the Domain Controller Security logs using Active Directory, then you should turn the option for Domain Controller Events to NO for the Rapid7 Agent (Insight Agent) here: Settings > Rapid7 Agent (Insight Agent) > Domain Controller Events.
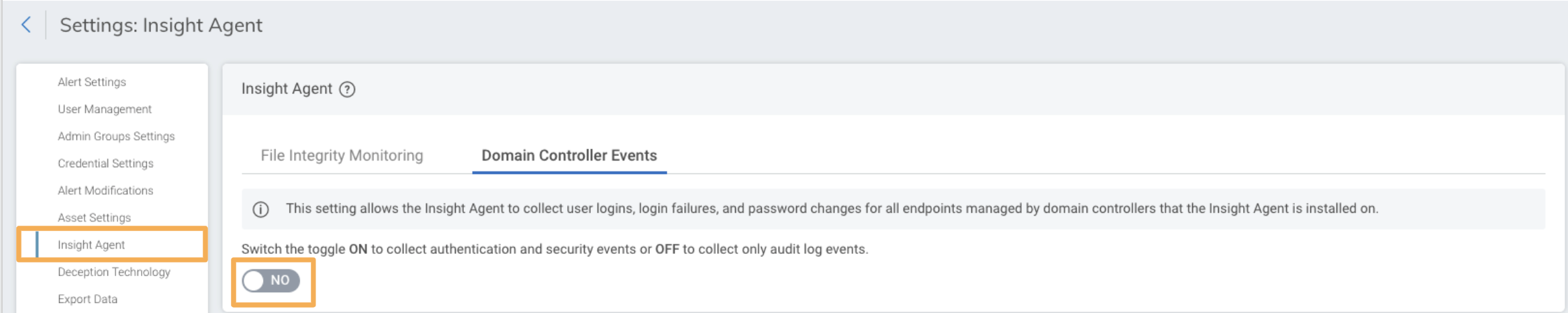
If you prefer to collect the Domain Controller Security logs using the Rapid7 Agent (Insight Agent), then then you should turn the option for Domain Controller Events to YES for the Rapid7 Agent (Insight Agent) here: Settings > Rapid7 Agent (Insight Agent) > Domain Controller Events.
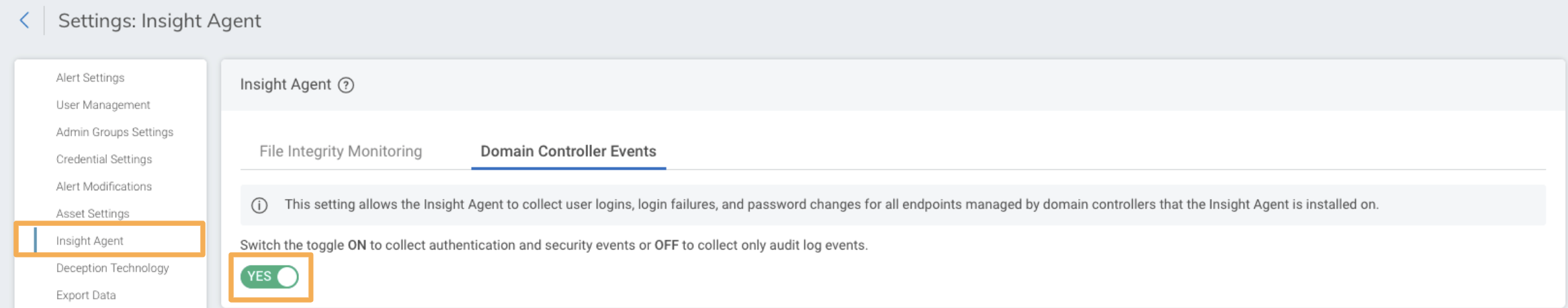
You should also pause the Active Directory event sources you have running using the Stop Running option here: Data Collection > Event Sources > Product type > Active Directory