AWS Honeypots
You can use honeypots in SIEM (InsightIDR) as a deception technology to locate attackers moving around a network. In order to make use of honeypots in your AWS environment, you can use an Amazon Machine Image (AMI) honeypot provided by SIEM (InsightIDR). Using this AMI, you can deploy SIEM (InsightIDR) honeypots in your AWS EC2 instances in order to monitor your virtual private cloud (VPC) subnets.
With AWS honeypots, you can detect if an intruder is scanning your AWS environment from within, attempting to laterally move through your network. If the intruder happens upon this AWS Honeypot, SIEM (InsightIDR) will fire detections to notify you automatically.
Deployment Architecture
Because honeypots are traps used to identify unexpected network traffic and catch intruders during lateral movement or exploration, you should deploy a honeypot to each isolated network segment.
For standard environments, one honeypot per VPC is sufficient. However, to increase coverage, you can deploy honeypots to your individual subnets.
Honeypots cannot have a public IP address and must be able to connect to the Insight platform. Therefore, do not deploy the honeypot on public subnets.
You can configure an AWS Honeypot in two ways: through a Rapid7 provided CloudFormation Template, or by manually configuring a honeypot in your AWS console.
To add an AWS honeypot to your environment:
Create a Honeypot Token
Before you can create a honeypot in your AWS environment, you must first add an AWS Honeypot in SIEM (InsightIDR) in order to acquire a token. You can then use this token to register the honeypot in AWS to your SIEM (InsightIDR) account.
To create a token:
- Sign in to SIEM (InsightIDR).
- Select the Data Collection page from the left menu, and then click Setup Honeypot > Add AWS Honeypot.
- Name your honeypot something identifiable.
- Click the Add button to register the honeypot name.
- The registration token will appear. Click the Copy button to copy the token for later use in your AWS console.
_token.png)
Choose a Honeypot Setup
You can choose from the following setup options:
Deploy a honeypot in each subnet you’re interested in monitoring in your AWS environment.
Deploy the Rapid7 CloudFormation Template
If you want to deploy the AWS Honeypot in fewer steps, you can use the Rapid7 CloudFormation Template to configure most of the settings. In order to use the CloudFormation template, you must have the following permissions:
- Launch EC2 instances
- Create Security Groups
- Create IAM roles
- Create Lambdas
- Create CloudFormation stacks
You can access the CloudFormation Template wizard directly here: https://console.aws.amazon.com/cloudformation/home#/stacks/new?stackName=insightidr-honeypot-0&templateURL=https://s3.amazonaws.com/com.rapid7.razor.public/honeypot/aws/template.yaml
To use the Rapid7 CloudFormation Template:
- Sign in to your AWS Console.
- From the “Services” dropdown, click the CloudFormation page.
- In the top left corner, click the Create Stack button.
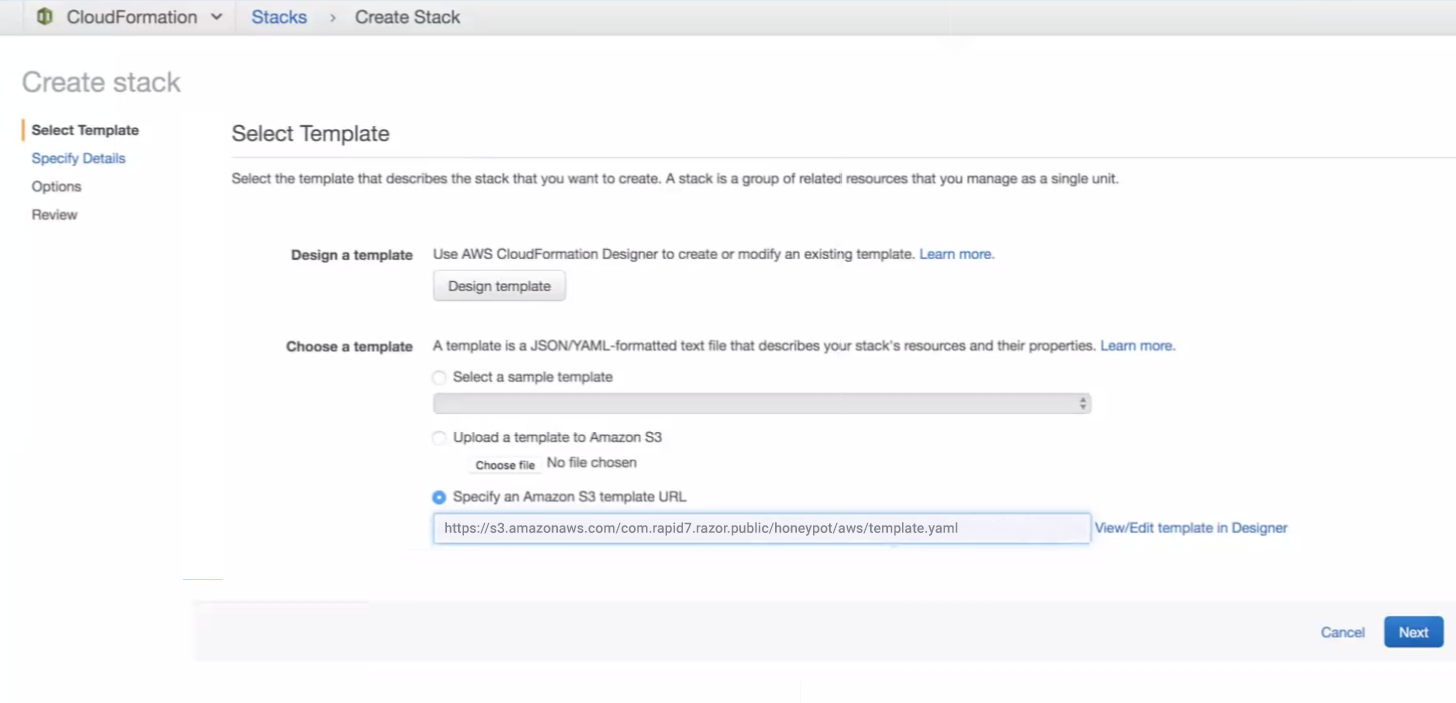
- On the “Select Template” page, select the Specify an Amazon S3 Template URL option at the bottom of the page.
- Paste in the following value:
https://s3.amazonaws.com/com.rapid7.razor.public/honeypot/aws/template.yaml
- Click the Next button.
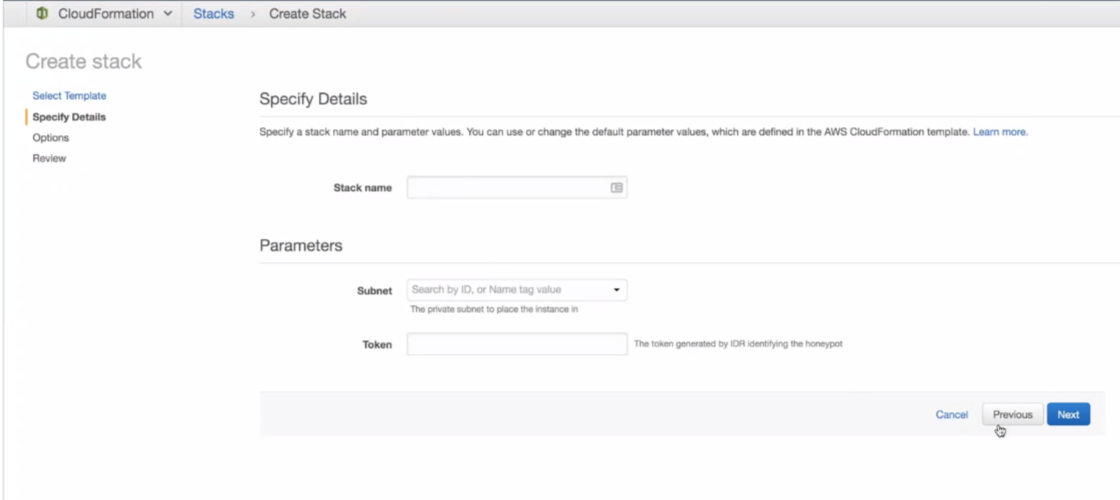
- On the “Specify Details” page, name your AWS Honeypot.
- From the “Subnet” dropdown, select the subnet on which to deploy the Honeypot.
For each subnet that you will deploy a honeypot, make sure that the subnet has a NAT instance or NAT gateway that allows EC2 instances in the subnet to communicate out to the public internet. This is needed for the Honeypot instance to communicate with the Rapid7 Insight platform. An internet gateway is not sufficient for this deployment.
- In the “Token” field, paste the Token you copied from the SIEM (InsightIDR) and click the Next button.
- On the “Options” page, you can change any details as desired. Click the Next button when ready.
- On the “Review” page, you can review the configuration choices so far.
- Check the Acknowledgement box at the bottom of the page and click the Create button.
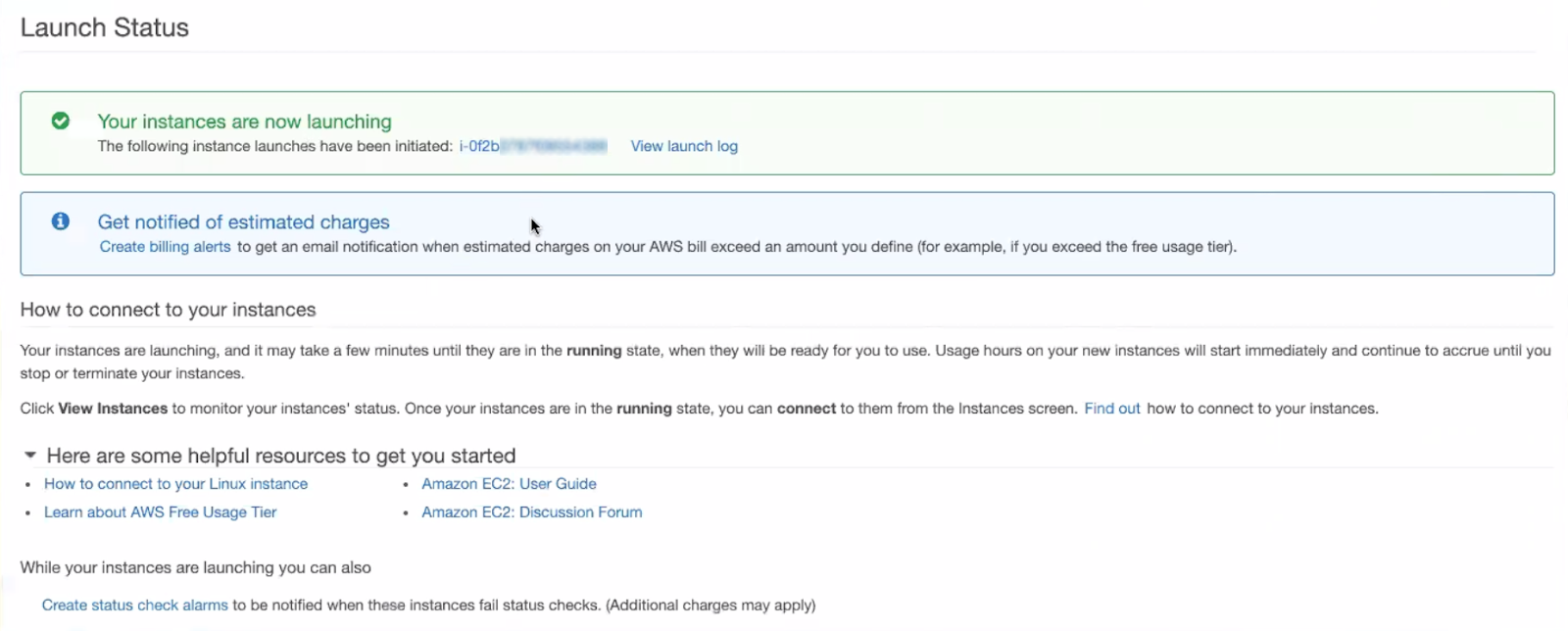
The “Launch Status” page will appear.
Manually Configure your AWS Environment
If you prefer to manually configure your AWS environment instead of using the Rapid7 CloudFormation template, ensure that you have permission to launch EC2 instances and create Security Groups within AWS.
To create a Honeypot in your AWS environment:
- Sign in to your AWS Management Console.
- From the “Services” dropdown, go to EC2 and click the Launch New Instance button.
- Alternatively, you can click “Running Instances” and choose an existing instance.
- On the “Choose an Amazon Machine Image” page, select the Community AMI tab and search for Rapid7-SIEM (InsightIDR)-AWS-Honeypot.
- You can also browse the the Rapid7 AMI list using this text file .
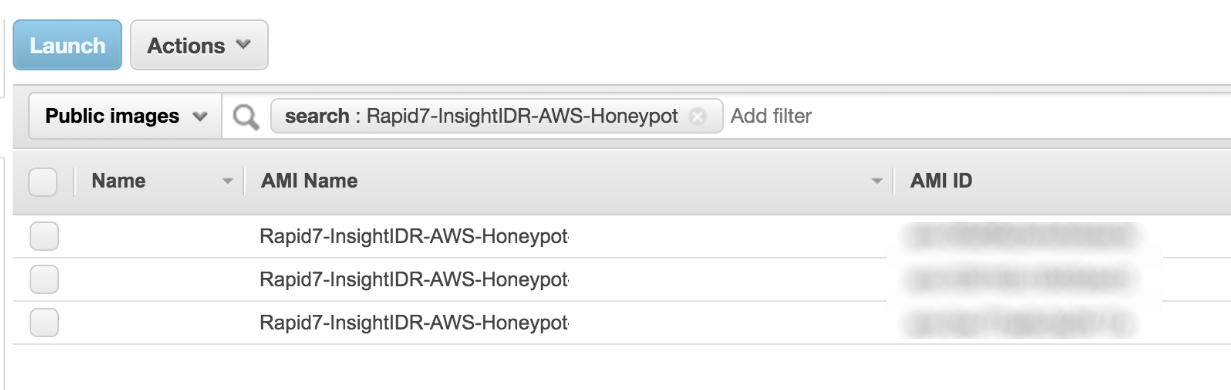
- Click the Select button depending on what kind of AMI you want to create.
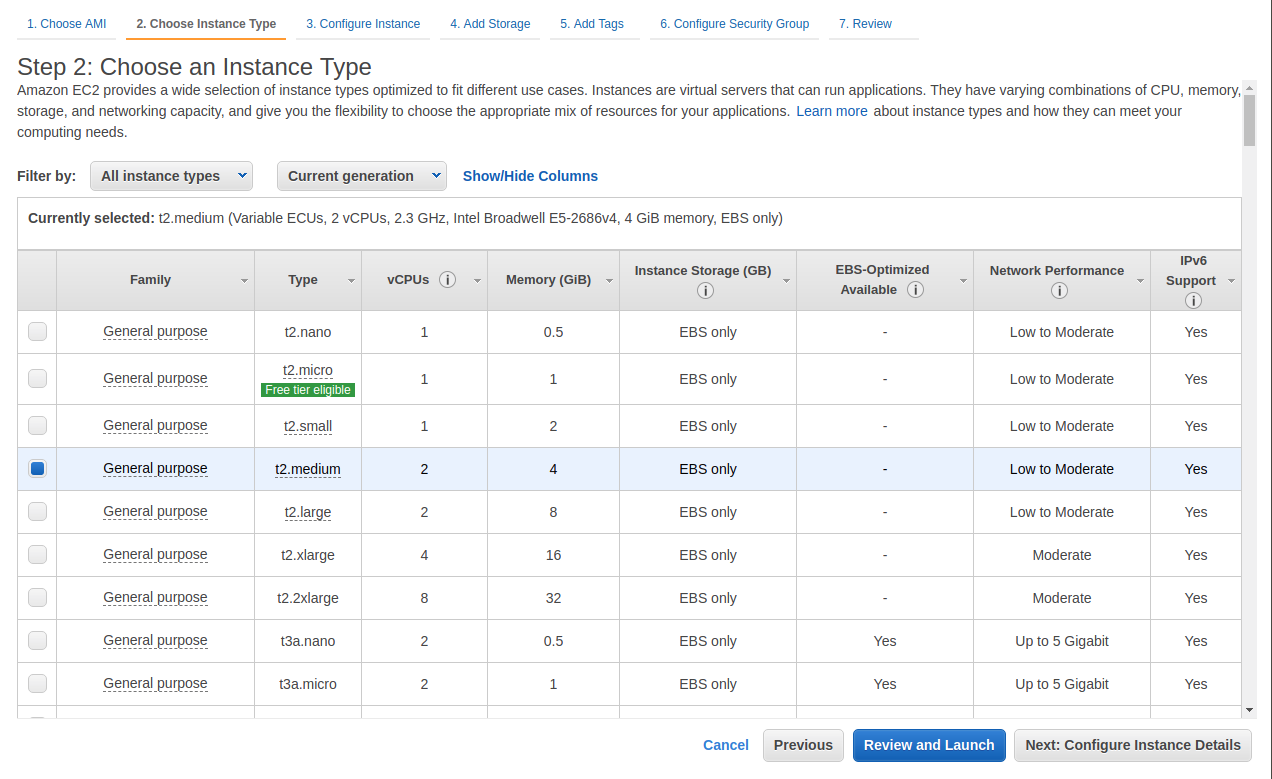
- On the “Instance Type” page, select the t2.medium option and click the Next button.
- On the “Configure Instance Details” page, expand the Network dropdown and choose the network you want the AWS Honeypot to monitor and listen to.
- Expand the Subnet dropdown and select which subnet you want the AWS honeypot available on.
For each subnet that you will deploy a honeypot, make sure that the subnet has a NAT instance or NAT gateway that allows EC2 instances in the subnet to communicate out to the public internet. This is needed for the Honeypot instance to communicate with the Rapid7 Insight platform. An internet gateway is not sufficient for this deployment.
- Expand the Auto Assign Public IP dropdown and choose the Disable option.
If you do not “Disable” this option, your Honeypot will fail to launch.
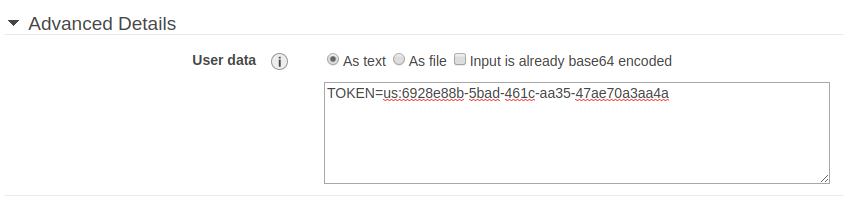
- Scroll down and expand the Advanced Details tab.
- In the “User Data” field, choose the As Text option, then enter
TOKEN=followed by the Token you copied from SIEM (InsightIDR). Click the Next button when finished.
- On the “Storage” page, choose any storage details you want, and click the Next button.
- On the “Tags” page, apply any tag details you want, and click the Next button.
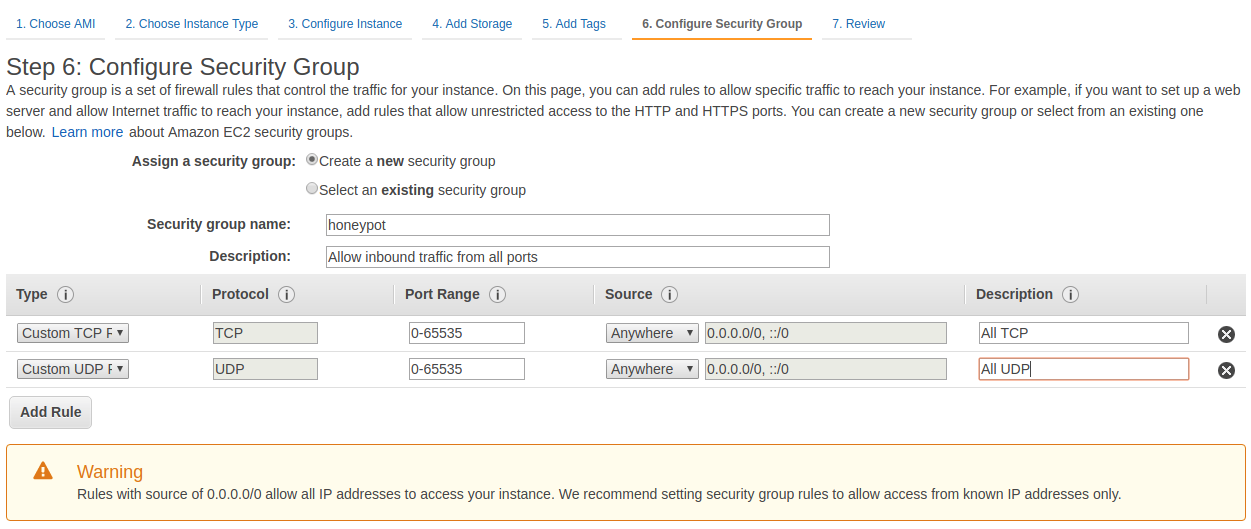
- On the “Configure Security Group” page, select the Create a new security group option. Provide a name and description for the security group that is identifiable.
- In the table at the bottom of the page, change the “Type” dropdown to the Custom TCP Rule option.
- In the “Port Range” field, enter “0-65535” as the range.
- In the “Source” field, select the Anywhere option from the dropdown. Provide a description if desired.
- Click the Add Rule and choose the Custom UDP Rule option.
- In the “Port Range” field, enter “0-65535” as the range.
- In the “Source” field, select the Anywhere option from the dropdown. Provide a description if desired.
- Click the Review and Launch button.
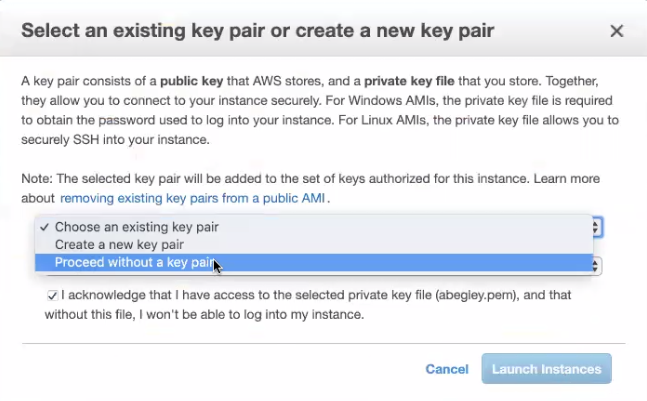
- On the “Review” page, look over the configuration details, and then click the Launch button. A new window will appear about Key Pairs.
- In the “Key Pair” dialog window, select the option to Proceed without a key pair and check the acknowledgment box.
- Click the Launch Instances button.
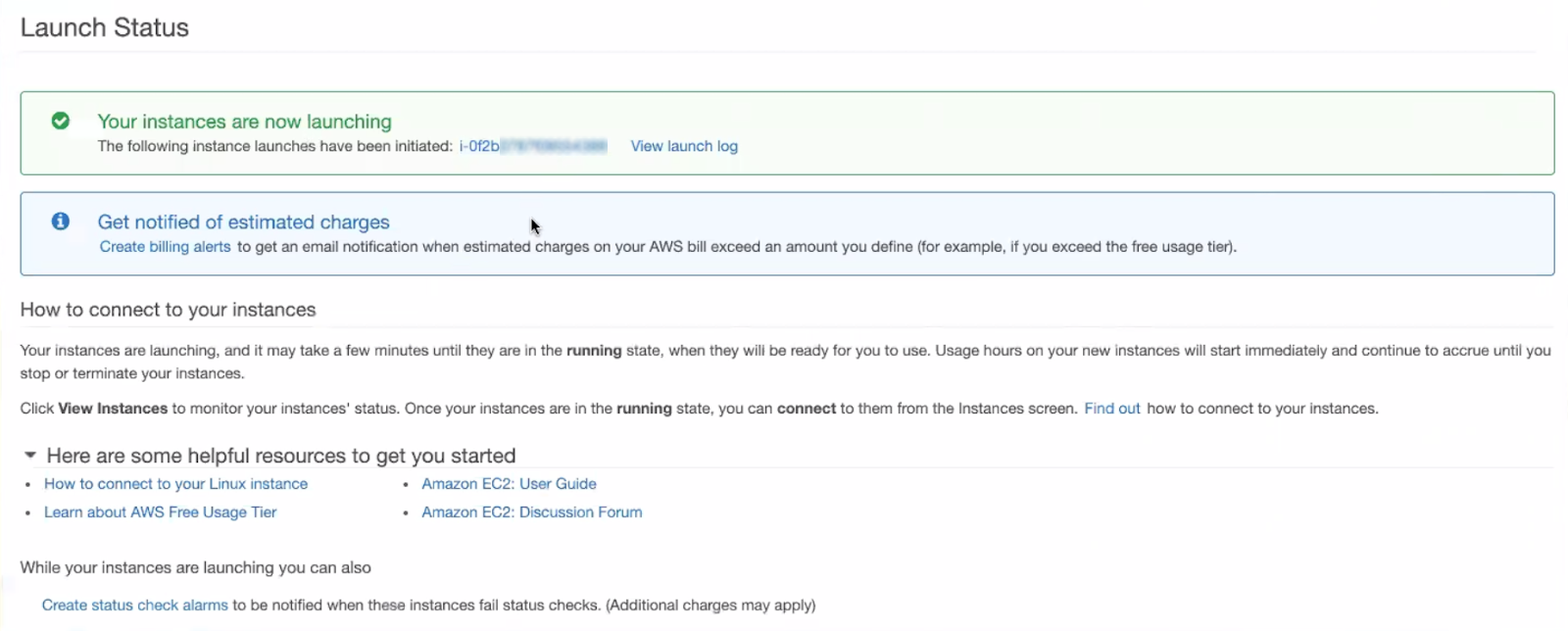
Review the Launch Status
Once you create and deploy your Honeypot, you will see the “Launch Status” page.
To review the launch status of your Honeypot:
- Click the provided link for your newly launched instance.
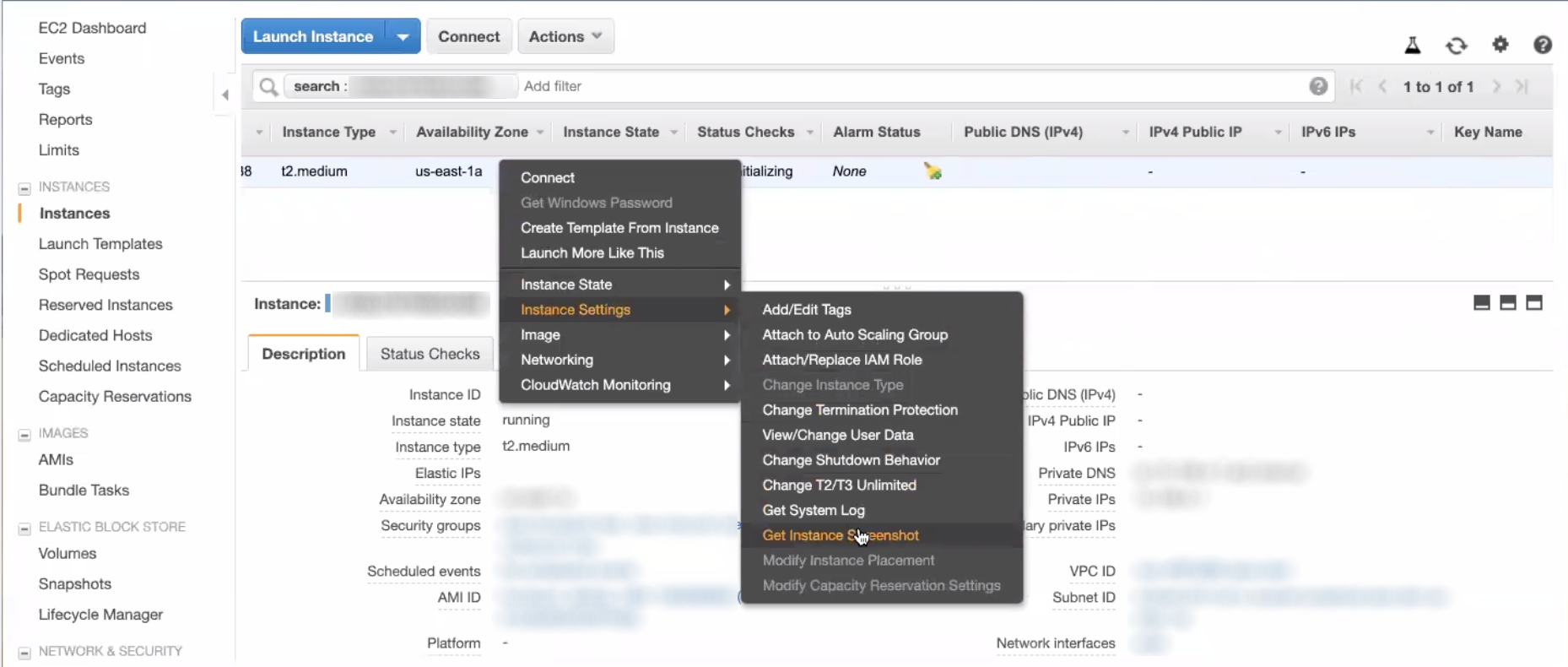
- When your instance is running, right click on the table for the properties option and select Instance Settings > Get System Log.
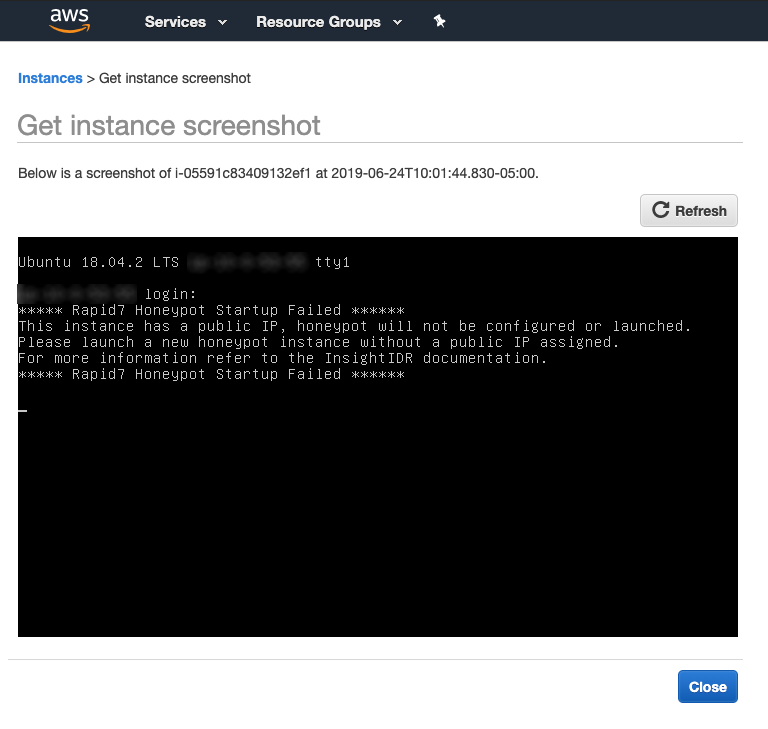
The “System Log” is where you can see the log of your new AWS Honeypot. AWS will populate the system log in about five to ten minutes - note that it may initially be black. You will see the SIEM (InsightIDR) Collector log on this AWS Honeypot, which signals that everything is working correctly.
Error Messages
You will see any error messages in the Instance Screenshot, such as issues reading the registration token, the launched instance having a public IP address assigned to it, or if the honeypot is unable to communicate over the internet to the Rapid7 Insight platform.
Trigger a Test Detection
After you have successfully created an AWS Honeypot using the token from SIEM (InsightIDR), check to see that the pairing was successful in the SIEM (InsightIDR) interface on the Honeypots tab of the “Data Collection” page.
Then, you can test the pairing by triggering a detection and creating an investigation.
Before you test, ensure that you can complete the test from a system that can reach the Honeypot on the AWS network.
Then, choose one of the following ways to test your AWS Honeypot:
- curl to attempt an http connection to the honeypot IP address
- basic nmap scan
- standard discovery scan
- vulnerability scan
- SSH via PuTTY
- Bruteforce
Within minutes, you should see a new investigation in SIEM (InsightIDR).