AWS Managed Microsoft AD
AWS Managed Microsoft AD is the cloud based active directory service offered by Amazon Web Services. You can configure AWS Managed Microsoft AD to send LDAP data to SIEM (InsightIDR) for tracking and alerting purposes.
Before you begin
- Review and ensure that you meet the prerequisites for creating a Managed Microsoft AD AWS Directory: https://docs.aws.amazon.com/directoryservice/latest/admin-guide/setting_up.html
- When you configure AWS Managed Microsoft AD, make note of the following information, as you’ll need to reference it when enabling the event source in SIEM (InsightIDR):
- Domain Name
- DNS address
- Admin password
Configure AWS Managed Microsoft AD
Task 1: Create AWS Managed Microsoft AD Service
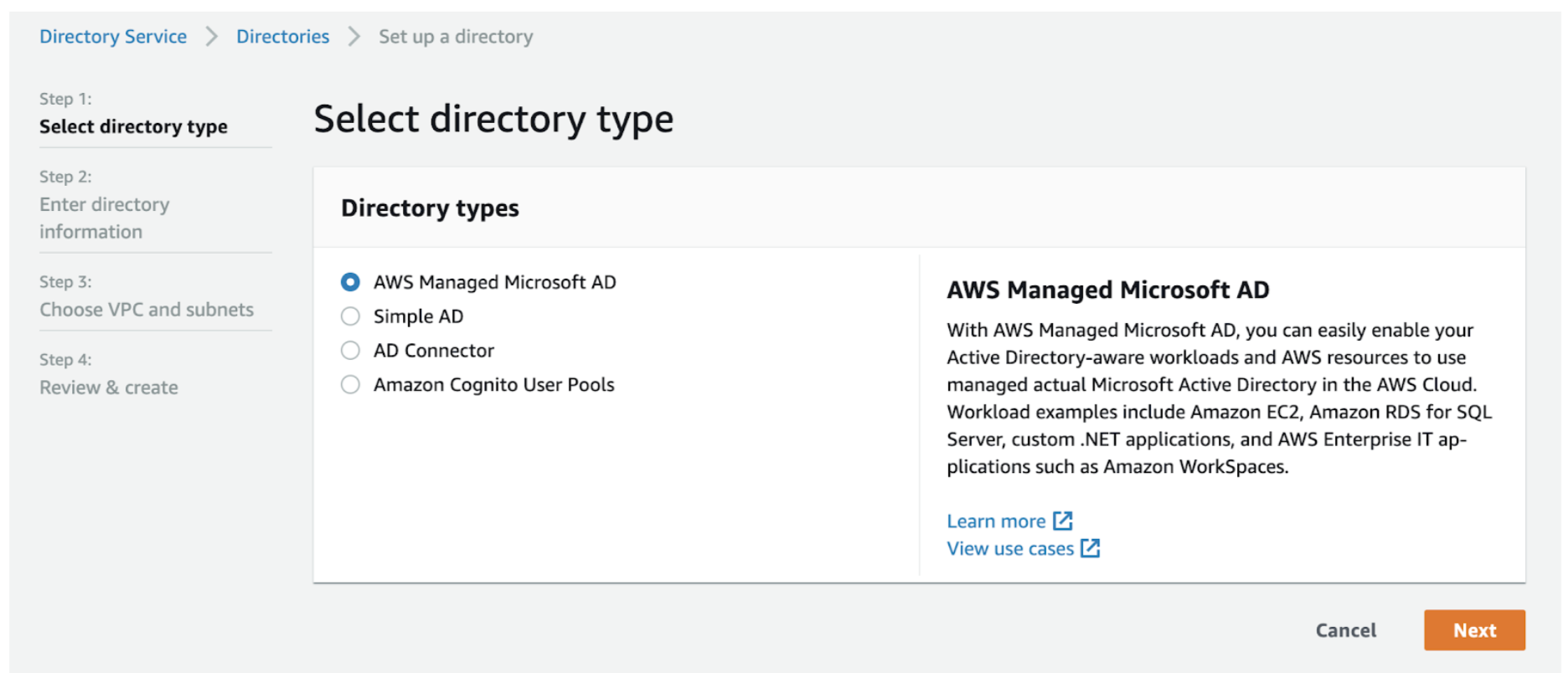
- In the AWS console, search for “Directory Service”, select AWS Managed Microsoft AD as your directory type, and click Next.
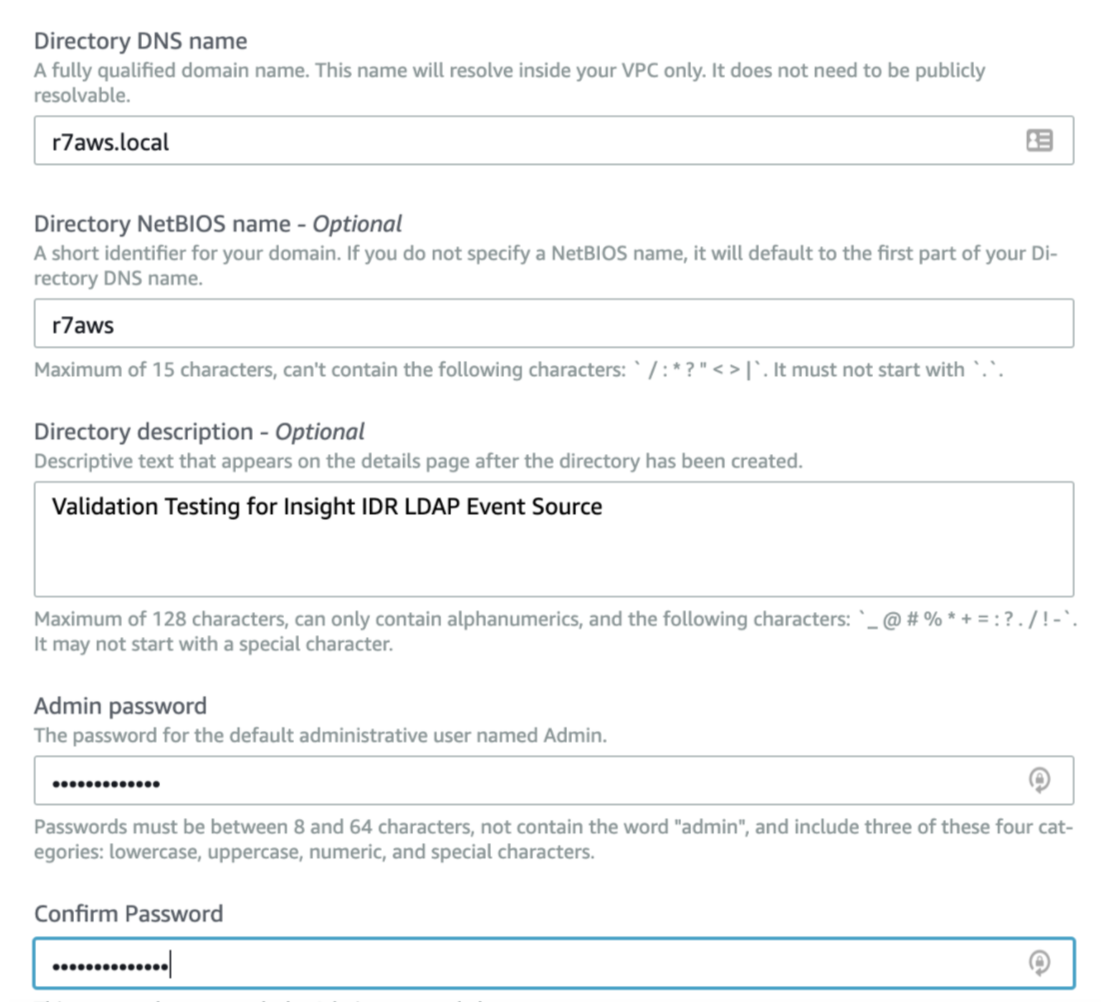
- Provide the domain name that will be used for the domain, and enter a password.
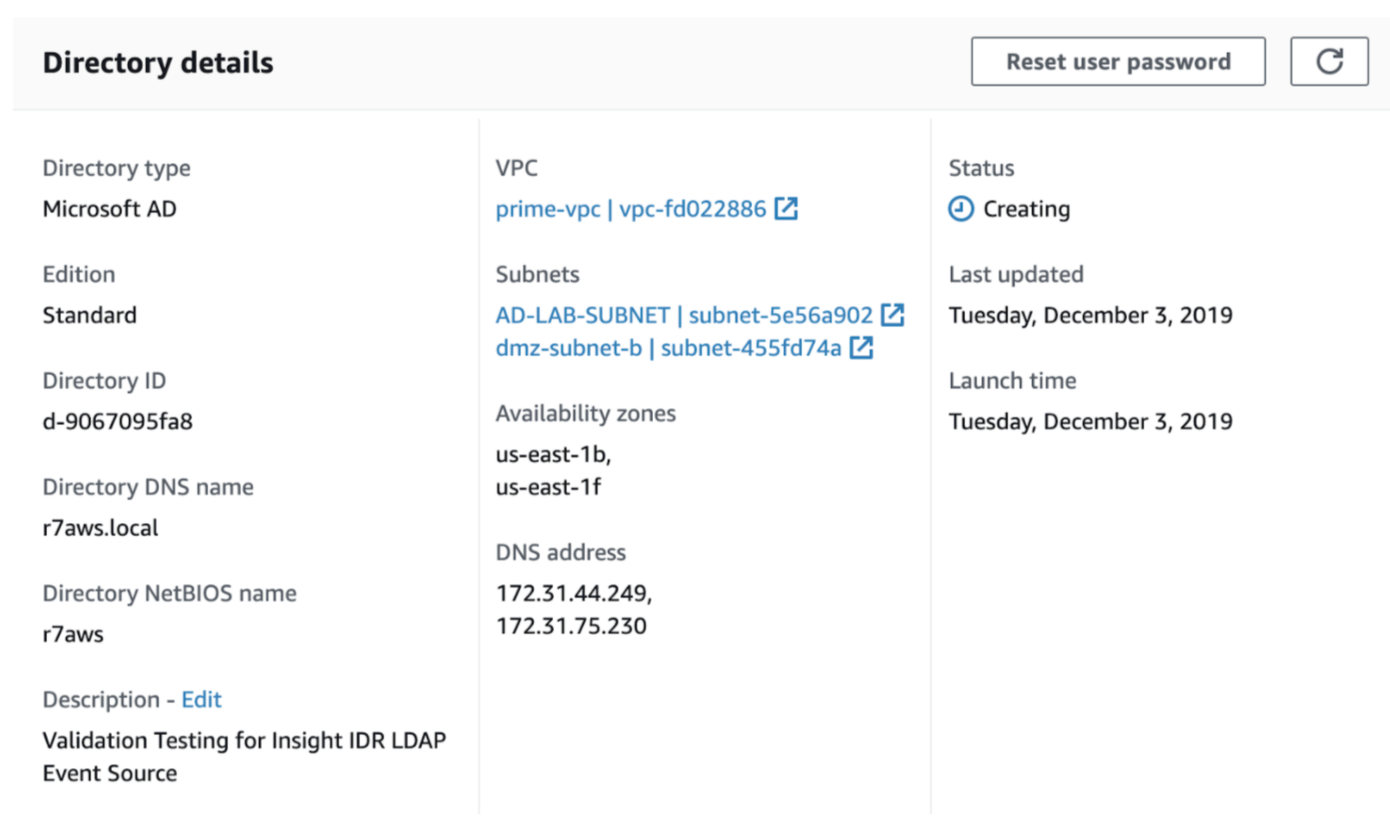
- In Directory Details, make note of the DNS addresses that will be used by SIEM (InsightIDR) to poll the LDAP data. You will need this information when setting up your event source in SIEM (InsightIDR).
Task 2: Configure DHCP Option Set
Configure the DHCP options set and assign it to the VPC in use. This allows any instances in that VPC to point to the specified domain and DNS servers to resolve their domain names.
- Open the Amazon VPC console and in the navigation pane, click Create DHCP Options Set.
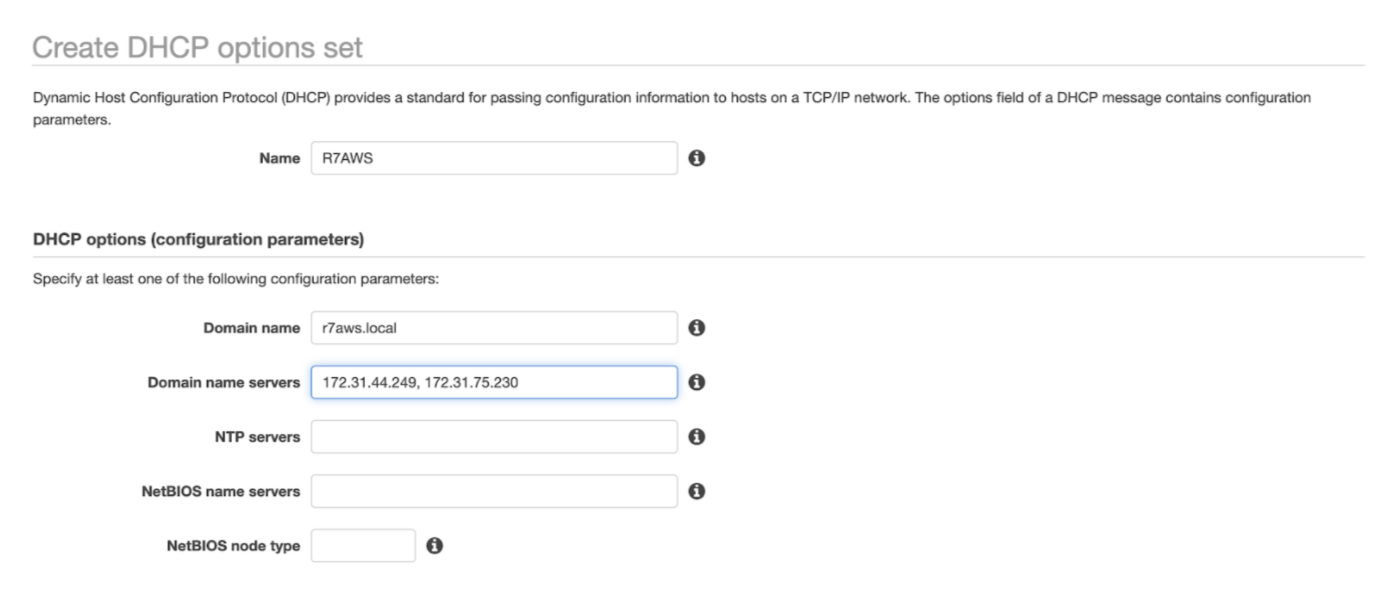
- Name your DHCP options set, and enter the Domain Name and Domain name servers.
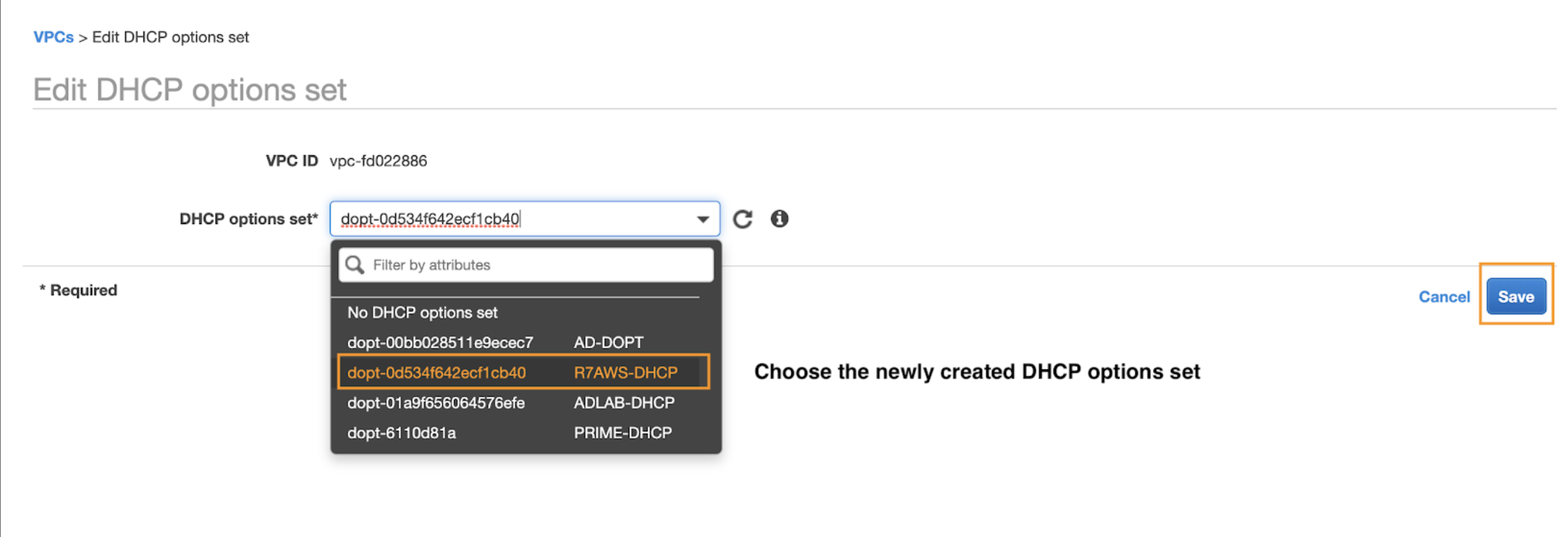
- Choose Create DHCP options set, select the newly added DHCP options set, and click Save.
Task 3: Deploy an instance to manage users and groups
After you set up a domain service, you can create a new instance to manage Users and Groups in AWS Managed Microsoft AD.
For instructions, see https://docs.aws.amazon.com/directoryservice/latest/admin-guide/ms_ad_manage_users_groups.html .
Task 4: (Optional) Run a test LDAP query from the new instance
Once you’ve completed the setup, we recommend that you test the connection using a tool approved by your organization. In this section, we’ll walk you through our test case.
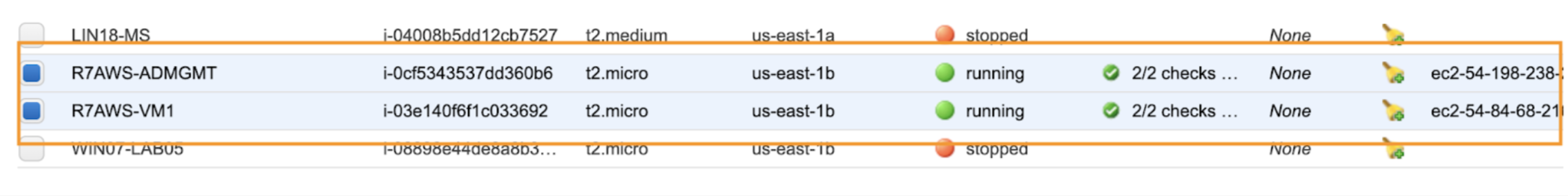
For the purposes of our example, we created a couple of EC2 instances, naming the first R7AWS-ADMGMT (used for managing AD users & groups), and the second instance named R7AWS-VM1. Both are joined to the newly created domain and as an additional step, we tested the LDAP connection from R7AWS-VM1.
We tested the connection using Idp.exe (which you can download HERE ), and the following results show a successful connection, and that the instance is polling the AD user account information.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for AWS Managed Microsoft AD in the event sources search bar.
- In the Product Type filter, select LDAP.
- Select the AWS Managed Microsoft AD event source tile.
- Choose your collector and select Microsoft Active Directory LDAP.
- Choose the timezone that matches the location of your event source logs.
- In the Server field, enter the DNS address you noted in step 3 of Create AWS Managed Directory Service.
- In the Refresh Rate field, enter the refresh rate in hours.
- In the User Domain field, enter the AD Domain.
- In the Credentials field, enter the domain credentials that you created.
- In the Password field, enter the password to access the LDAP server.
- (Optional) In the Base DN field, enter the value for your Base Distinguished Name.
- (Optional) Enter the name of the group that has admin privileges.
- Click Save.
Verify the configuration
Once you’ve added your event source, you should verify that SIEM (InsightIDR) is successfully pulling LDAP data.
To verify the configuration:
- In SIEM (InsightIDR), navigate to Data Collection and select the Event-Sources tab.
- Under Product Type, choose LDAP and click View raw log to confirm that LDAP queries are successfully running.
A successful LDAP poll:
{"physicalDeliveryOfficeName":"Home","whenCreated":"20191205012438.0Z","manager":"CN=bclinton,OU=Users,OU=r7aws,DC=r7aws,DC=local","sAMAccountName":"fflinstone","givenName":"Fred","distinguishedName":"CN=Fred Flinstone,OU=Users,OU=r7aws,DC=r7aws,DC=local","title":"Rock Miner","objectGUID":"MT/MCXDbkkObo7iaJQKmtQ==","sn":"Flintstone","department":"Mining Division","userAccountControl":"66048","userPrincipalName":"fflinstone@r7aws.local","pwdLastSet":"132199826781552103"}
{"physicalDeliveryOfficeName":"Del Rio","whenCreated":"20191205021039.0Z","manager":"CN=bclinton,OU=Users,OU=r7aws,DC=r7aws,DC=local","sAMAccountName":"cwhite","givenName":"Chuck","distinguishedName":"CN=Chuck White,OU=Users,OU=r7aws,DC=r7aws,DC=local","title":"Fuller Brush Salesman","objectGUID":"iCHgbaS6KU2ri9MwpQWItg==","sn":"White","department":"Sales Division","userAccountControl":"66048","userPrincipalName":"cwhite@r7aws.local","pwdLastSet":"132199854395196939"}