CyberArk Vault
You can configure CyberArk Enterprise Password Vault (EPV) and Privileged Threat Analytics (PTA) to send syslog messages in CEF or LEEF format to Rapid7 SIEM (InsightIDR).
This integration allows you to:
- Perform in-depth analysis using multi-layer correlation between log data and alerts from PTA.
- Identify suspicious privileged user activity using behavioral analysis.
- Determine which incidents pose the greatest threat based on the score assigned to a particular threat.
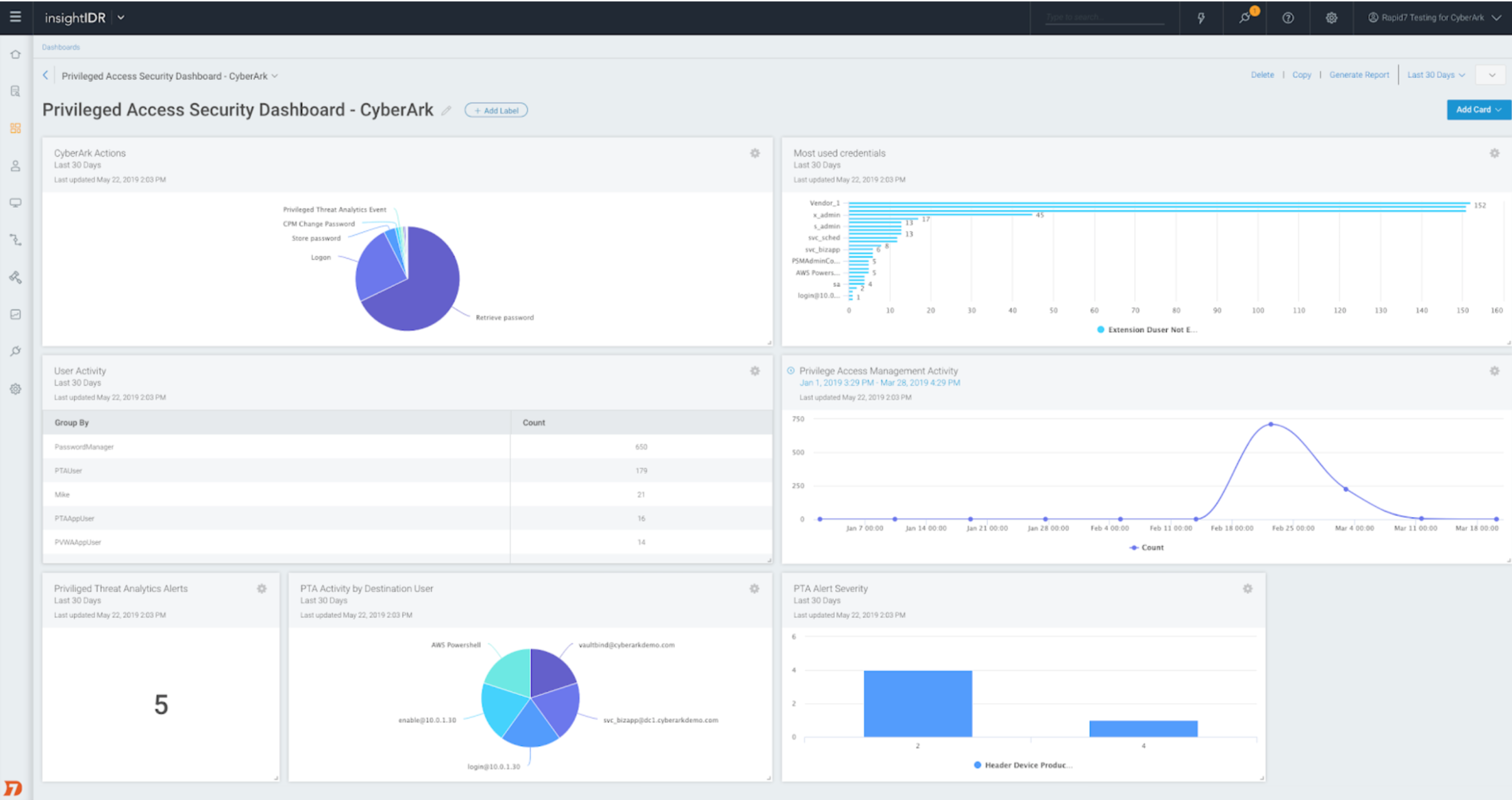
- View PTA alerts in your dashboards and reports, and in your broader SIEM (InsightIDR) detections and investigation workflow.
The guide is based on CyberArk EPV Version 9.95, CyberArk PTA Version 3.6
To start ingesting CyberArk events within SIEM (InsightIDR):
- Configure Privileged Threat Analytics
- Configure CyberArk PTA in SIEM (InsightIDR)
- Configure Enterprise Password Vault
- Configure CyberArk Vault within SIEM (InsightIDR)
Configure Privileged Threat Analytics
When PTA detects an event, it sends a syslog record to SIEM (InsightIDR) in real time, in CEF/LEEF format. The Syslog integration is controlled by syslog_outbound parameter in the PTA systemparm.properties file, located in /opt/tomcat/diamond-resources/local/. Once a PTA alert has been sent to SIEM (InsightIDR), it will appear in your dashboards, reports, and detections and investigation workflow.
To configure CyberArk PTA to send incidents to SIEM (InsightIDR):
- Log on to PTA as root.
- Open
/opt/tomcat/diamond-resources/local/systemparm.propertiesand add the following line:
syslog_outbound=[{"host": "<ip of SIEM (InsightIDR) Collector>", "port": <port of your choosing>, "format": "CEF", "protocol": "UDP", "siem":"SIEM (InsightIDR)"}] - To send records to SIEM (InsightIDR), do one of the following:
- If you are sending records in CEF format, add the following line:
syslog_outbound=[{"host": "<ip of SIEM (InsightIDR) Collector>", "port": <port of your choosing>, "format": "CEF", "protocol": "UDP", "siem":"SIEM (InsightIDR)"}]- If you are sending records in LEEF format, add the following line:
syslog_outbound=[{"host": "<ip of SIEM (InsightIDR) Collector>", "port": <port of your choosing>, "format": "LEEF", "protocol": "UDP", "siem":"SIEM (InsightIDR)"}]- Save the configuration file and close it.
- Restart PTA.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for CyberArk Vault in the event sources search bar.
- In the Product Type filter, select Third Party Alerts.
- Select the CyberArk Vault event source tile.
- Choose your collector and select CyberArk as your event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Choose Syslog as your data collection method.
- Enter the same port that you configured during the CyberArk PTA configuration and select UDP as your protocol.
- Click the Save button.
Configure Enterprise Password Vault
CyberArk EPV can send audit logs to SIEM (InsightIDR) through the Syslog protocol, giving you a complete, audit-ready view into privileged account activities from within SIEM (InsightIDR).
These audit logs include privileged users, accounts, and safes activities, which are reported by the Vault to SIEM (InsightIDR).
- Navigate to your CyberArk installation folders to locate the standard translator, which is located in
C:\Program Files (x86)\PrivateArk\Server\Syslogby default. - Copy the standard translator and rename it to
Rapid7.xsl. - In the same server installation folder (
C:\Program Files (x86)\PrivateArk\Server), openDBPARM.ini, and add the following lines:
[SYSLOG]
SyslogServerIP=\<ip of SIEM (InsightIDR) Collector>
SyslogServerProtocol=UDP
SyslogServerPort=\<port of your choosing>
SyslogMessageCodeFilter=295,308,7,24,31,428,361,372,373,359,436,412,411,300,302,294,427,57,416,385,386,471,472
SyslogTranslatorFile=Syslog\Rapid7.xsl
UseLegacySyslogFormat=no - Make any appropriate changes, then save the file and close it.
- Restart CyberArk Vault, and start the PrivateArk Server Service.
Configure CyberArk Vault within SIEM (InsightIDR)
- From your SIEM (InsightIDR) main dashboard, select Data Collection from the left hand menu.
- When the Data Collection page appears, click the Setup Event Source dropdown and choose **Add Event Source. **
- From the “Third Party Alerts” section, click the Custom Logs icon. The “Add Event Source” panel appears.
- Choose your collector and select CyberArk Vault as your event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Choose Syslog as your collection method.
- Enter the same port that you configured in
dbparm.inifor CyberArk Vault and select UDP as your protocol. - Click the Save button.
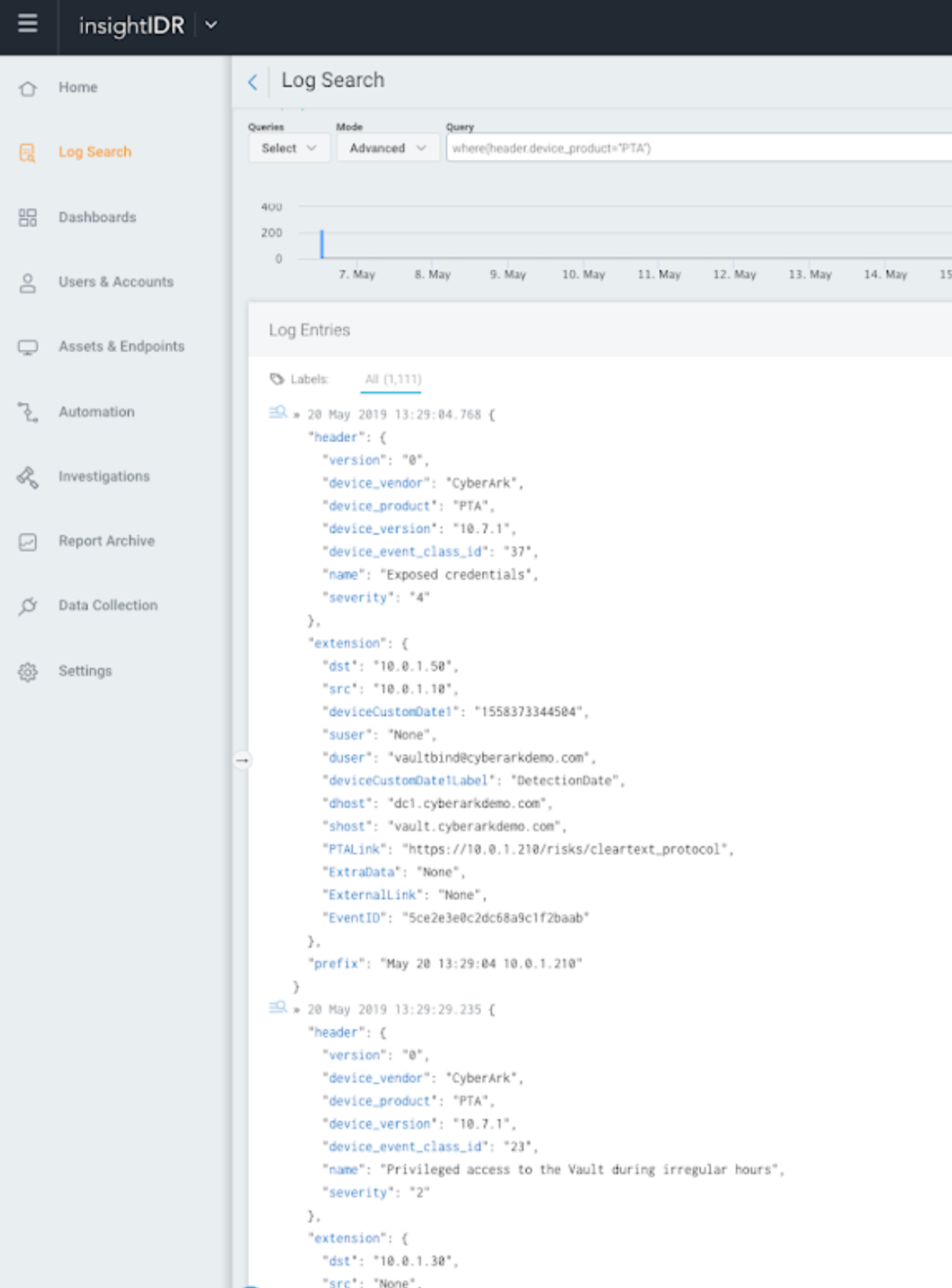
You can access events sent by CyberArk by going to Log Search, and selecting the Third Party Alert log set.
Once CyberArk data starts flowing into SIEM (InsightIDR), logs will be automatically structured for easy searching and visualization.
In SIEM (InsightIDR) Dashboards, you can easily visualize your privileged access security data.