Darktrace
Darktrace is a network traffic analyzing tool that delivers notification events to downstream systems. With Third Party Alert event sources in SIEM (InsightIDR), you can configure your Collector to capture these notification events and generate SIEM (InsightIDR) investigations around them.
To configure Darktrace as an event source, you’ll need to:
- Configure syslog forwarding in Darktrace.
- Configure the event source in SIEM (InsightIDR).
- Test the configuration.
Configure Syslog Forwarding in Darktrace
Before SIEM (InsightIDR) can start ingesting data from Darktrace, a Darktrace administrator with UI access must configure Darktrace to send syslog to the SIEM (InsightIDR) Collector.
To configure syslog forwarding in Darktrace:
- Log in to the Darktrace interface.
- Within the Threat Visualizer, navigate to Admin > System Config.
- From the left-hand menu, select Modules and choose Syslog from the available Workflow Integrations.
- In the configuration window, select the relevant form of Syslog - here, it’s Syslog JSON - and click New to open the configuration settings.
- Set the JSON Syslog Alerts field to true.
- In the JSON Syslog Server field, specify the IP address of the SIEM (InsightIDR) Collector.
- In the JSON Syslog Server Port field, specify a unique port over 1024 that you will use with the SIEM (InsightIDR) event source.
- Set the JSON Syslog TCP Alerts field to true.
Darktrace will automatically save your changes.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Darktrace in the event sources search bar.
- In the Product Type filter, select Third Party Alerts.
- Select the Darktrace event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Optionally, send unparsed logs.
- Enter the port you chose in the Darktrace interface.
- Select TCP as your protocol.
- Click the Save button.
Test the Configuration
After you configure the SIEM (InsightIDR) event source, you can send a test alert from Darktrace to SIEM (InsightIDR) to verify everything is working properly.
To send a test alert:
- Return to the Darktrace user interface.
- Expand the top left menu and select Admin. A second menu appears.
- Select the System Config page.
- In the Alerting section, click the Verify Alert Settings button.
You will see a message that reads “1 Alert Sent. IMAP settings valid.”
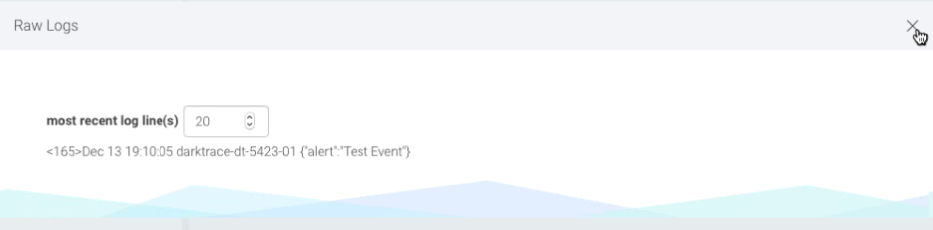
In SIEM (InsightIDR), your logs should look similar to the following:
How SIEM (InsightIDR) Determines Priority
In SIEM (InsightIDR), Darktrace events can generate alerts , which have a priority level. Depending on the detection rule configuration, the investigations created from these alerts will also inherit that priority level. The priority is determined using the Category, Score or Priority values.
A log’s Category can either be Informational or Suspicious. Alerts are never raised for Informational logs as they are less likely to represent a legitimate threat. We also do not raise alerts for any threats that contain information regarding Antigena Response because they can potentially raise numerous alerts, making the environment noisy. Learn more about these type of alerts here: https://bluekarmasecurity.net/partners/darktrace/ .
Alerts are always raised for Suspicious logs. If the Score field value is present we use it to determine the priority. The values range from 0 to 1 and are mapped like this:
- 0.8 to 1 is high priority.
- 0.5 to 0.79 is medium priority.
- 0 to 0.49 is low priority.
If the Score field value isn’t present, we use the Priority field value instead. The values range from 0 to 5 and are mapped like this:
- 3 to 5 is high priority.
- 1 to 3 is medium priority.
- 0 to 1 is low priority.