Microsoft SQL Database Audit Logs
You can track database administrative activity via Microsoft SQL Server for log search and basic detection rules (formerly known as custom alerts) on Windows machines.
Before You Begin
In order to collect database audit logs, you must enable auditing of the SQL server logs. You can read more about auditing a database here: https://docs.microsoft.com/en-us/sql/relational-databases/security/auditing/sql-server-audit-database-engine .
Use an account that has access to the Windows Security or Application Log.
To accomplish this, add a service account to the local Event Log Readers group.
To enable auditing of the SQL server database:
- Open a command window to configure the audit object access setting.
- Run the following command as an administrator:
auditpol /set /subcategory:"application generated" /success:enable /failure:enable - Run the following command to grant the generate security audits permission to an account:
secpol.msc - Go to the Local Security Policy tool and open Security Settings > Local Policies > User Rights Assignment.
- In the results pane, double-click Generate security audits.
- On the “Local Security Setting” tab, click Add User or Group.
- In the “Select Users, Computers, or Groups” dialog box, enter the name of the account SQL Server is running as and click OK.
- Restart SQL Server to enable this setting.
- To create a server audit, open SQL Server Management Studio.
- In “Object Explorer,” expand the Security folder.
- Right-click the Audits folder and select New Audit.
- Fill in the fields and choose either Windows Application log or Windows Security log as the audit destination.
In order to audit the Windows Security log, you must have access to the Event Log Readers on your local machine.
- When you are finished, click OK.
- Right click the newly created Audit and select Enable Audit.
- To create a server audit specification, go to “Object Explorer” and click the plus sign to expand the “Security” folder.
- Right-click the Server Audit Specifications folder and select New Server Audit Specification.
- Enter a name, choose the server audit created above, and configure the audit action types you want to log.
- For example, you could log the following:
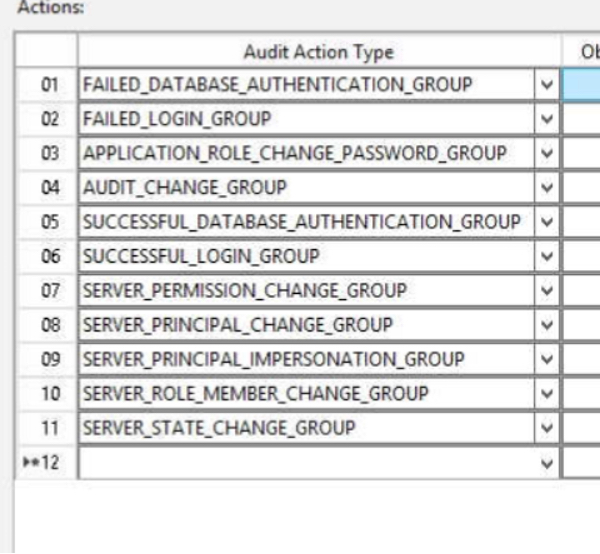
- When you are finished, click OK.
- Right click the newly created Audit Specification and select Enable Audit Specification.
Testing
After enabling SQL Server database auditing, follow these steps to verify that WMI and DCOM are functioning properly.
Test WMI Rights
- On the SQL server, run
wmimgmt. - Open root and highlight
cimv2. - Click Security and confirm the rights:
- Execute Methods
- Enable Account
- Remote Enable
- If a WMI browsing tool is available from the Collector, you should now be able to connect and browse
cimv2.
Test DCOM
- On the SQL server, run
dcomcnfg.exe. - Under Component Service, open Computers.
- Right click My Computer > Properties > COM Security tab.
- Under Launch and Activation Permissions, click Edit Limits.
- Confirm Remote Launch and Remote Activation are enabled.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Click Add Raw Data > Database Audit Logs.
- Alternatively, you can search for Microsoft SQL Server or filter by the Database Product Type, and then select the Microsoft SQL Server event source tile.
- Choose your collector. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- In the Server field, enter the IP address or the machine name of the server.
- In the User Domain field, enter the the domain of your credentials.
- Select existing credentials or create a new credential.
- In the Password field, enter the password for the SQL server.
- Click Save.
No Default Alerts
Database audit logs do not have alerts built-in by default. You must create your own alerts.