File Access Activity Monitoring
File Access Activity Monitoring (FAAM) uses the native Microsoft Audit Detailed File Share auditing to write all 5145 events from a Windows system to the Security Log. When you enable this auditing on a Windows domain, the Rapid7 Agent (Insight Agent) collects every access event from your files and folders and sends them to SIEM (InsightIDR).
To set up File Access Activity Monitoring, you’ll need to:
At this time, File Access Activity Monitoring is only available on Windows systems and can only track access to files and folders when accessed from a Windows share.
Enable File Access Activity Auditing
You can enable FAAM on the domain level using the Group Policy Management editor or on a single machine using the Local Security Policy tool.
To enable File Access Activity Auditing:
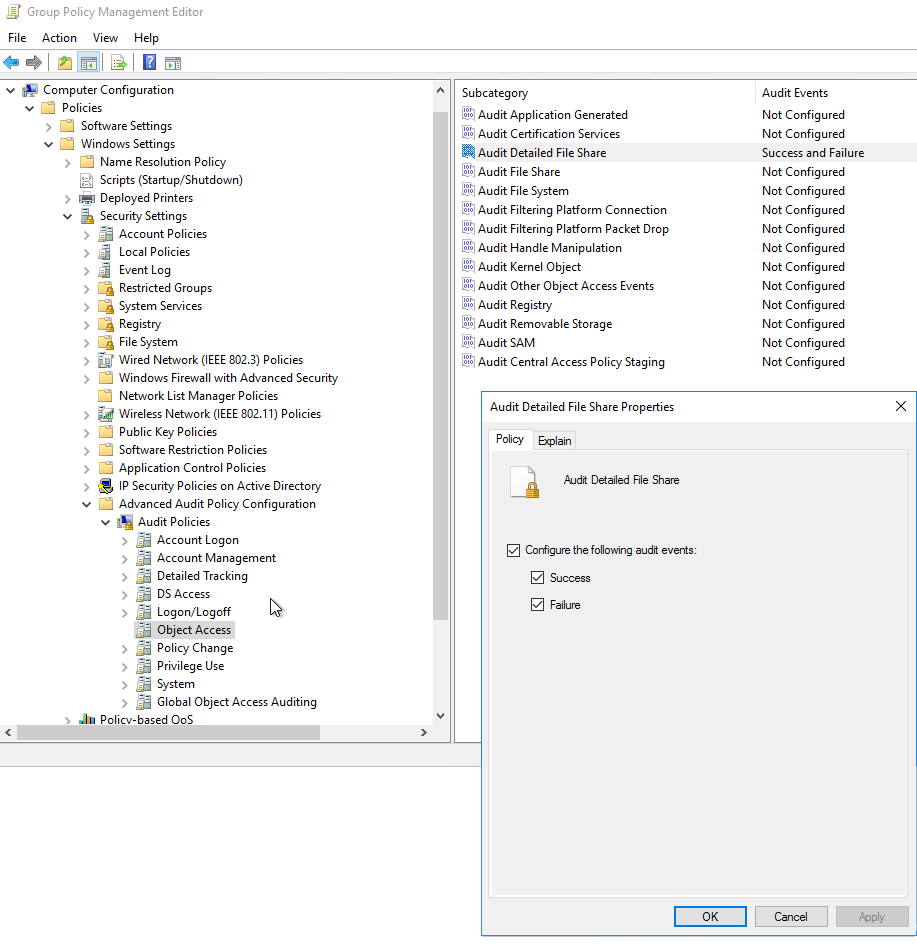
- Open the Group Policy Manager editor or Local Security Policy tool. Both tools will display the same options.
- Navigate to the following folder path: Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies.
- Select the Object Access policy. The “Subcategory” pane will appear on the right.
- Double-click Audit Detailed File Share to open and configure auditing.
- Under the “Policy Tab,” check one or both boxes to monitor Success or Failure events.
- Click OK to save your changes.
Verify FAAM Configuration
After you enable File Access Activity Auditing, the Rapid7 Agent (Insight Agent) will collect all of the events with event ID 5145 from the Windows Security Log. These events are created any time a file or folder is accessed from a network share. For more information on this event, see Microsoft documentation here: https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/event-5145 .
Logs will appear on the Log Search page five to ten minutes after an event occurs.
To verify this configuration is working:
- Trigger an event by accessing a file or folder on the Windows share.
- In SIEM (InsightIDR), go to the Log Search page and select the File Access Activity log set.
- Browse the logs to see the file access events.
The following is an example of a File Access Activity log:
02 Jan 2019 08:43:38.894{
"timestamp": "2019-01-02T14:42:37.850Z",
"user": "John Smith Admin",
"account": "jsmith_adm",
"user_domain": "example.com",
"source_asset": "yellow.example.com",
"source_address": "192.168.0.162",
"service": "Windows File Share",
"target_address": "red.example.com",
"file_path": "//Public/Documents/Important Notes.txt",
"file_name": "Important Notes.txt",
"file_extension": "txt",
"file_share": "Public",
"access_types": "ReadData",
"source_data": "{\"sourceName\":\"Microsoft-Windows-Security-Auditing\",\"insertionStrings\":[\"S-1-5-21-4177825978-4092304191-3872814866-1108\",\"jsmith_adm\",\"EXAMPLEDOMAIN\",\"0x280fe8dd\",\"File\",\"192.168.0.000\",\"58321\",\"\\\\\\\\*\\\\Public\",\"\\\\??\\\\C:\\\\FileShare\\\\Public\",\"Documents\\\\Important Notes.txt\",\"0x120089\",\"%%1538\\r\\n\\t\\t\\t\\t%%1541\\r\\n\\t\\t\\t\\t%%4416\\r\\n\\t\\t\\t\\t%%4419\\r\\n\\t\\t\\t\\t%%4423\\r\\n\\t\\t\\t\\t\",\"%%1538:\\t%%1804\\r\\n\\t\\t\\t\\t%%1541:\\t%%1801\\tD:(A;;0x1301bf;;;WD)\\r\\n\\t\\t\\t\\t%%4416:\\t%%1801\\tD:(A;;0x1301bf;;;WD)\\r\\n\\t\\t\\t\\t%%4419:\\t%%1801\\tD:(A;;0x1301bf;;;WD)\\r\\n\\t\\t\\t\\t%%4423:\\t%%1801\\tD:(A;;0x1301bf;;;WD)\\r\\n\\t\\t\\t\\t\"],\"eventCode\":5145,\"computerName\":\"red.example.com\",\"sid\":\"\",\"isDomainController\":false}"Differences Between FIM and FAAM
Configuring File Access Activity Monitoring is not the same as configuring File Integrity Monitoring (FIM). While FIM has a similar configuration process using the native Microsoft auditing tools, that is the only similarity they share.
The following table shows the differences between FIM and FAAM:
| File Integrity Monitoring (FIM) | File Access Activity Monitoring (FAAM) | Events Monitored | Log Set Name | ||
|---|---|---|---|---|---|
| Individual File/Folder Audit | Yes | No | File Modification Activity | ||
| Microsoft Native Auditing | Yes | Yes | |||
| Event ID Collected | Event ID 4663 | Event ID 5145 | |||
| Events Monitored | Modify, create, and delete events only. | All access events | |||
| Log Set Name | File Modification Activity | File Access Activity |