Google Apps
Google Apps are a set of cloud-based productivity applications. In order to collect data from Google apps, you must use a Google account that has Admin privileges. Rapid7 recommends that you use a private browsing window to set this event source up to ensure that you log onto the correct admin level account.
In order to read Google Apps logs, the collector needs to reach the Google server to pull the logs, and must be able to connect to https://www.googleapis.com
Privacy Policy
Rapid7’s SIEM (InsightIDR) product uses OAuth Authentication to retrieve administrator audit logs from the Google Apps HTTP API. When configuring the Google Apps event source, the only permission that SIEM (InsightIDR) requires in the authorization grant is admin.reports.audit.readonly.
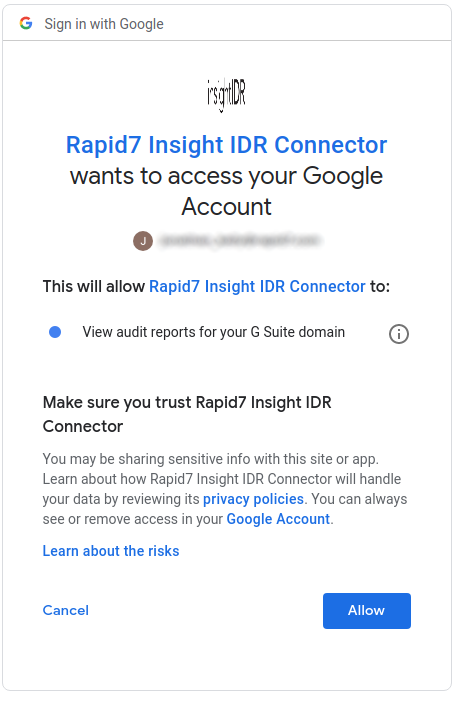
Once configured, Google Admins can see SIEM (InsightIDR) requests in the Google Admin interface.
SIEM (InsightIDR) uses encrypted Amazon Web Service S3 Buckets to store saved data. SIEM (InsightIDR) uses your audit logs to track and detect on potentially malicious admin activity, as well as to make logs available in Log Search for reporting and compliance.
Any data you share with Rapid7 is NOT shared externally and will only be used for internal purposes such as troubleshooting and new feature development. You can read more about Rapid7’s privacy policy here: https://www.rapid7.com/privacy-policy
Before You Begin
Google Apps is enabled via an OAuth credential. Read about requirements for this credential here: https://developers.google.com/admin-sdk/reports/v1/guides/prerequisites .
In order to configure this event source, you will need to be a Google Admin.
If you are logged into an account that does not have Admin privileges, the OAuth popup displays to use that logon instead, which won’t have the rights you need. Log out and log onto a Google account that has Admin privileges.
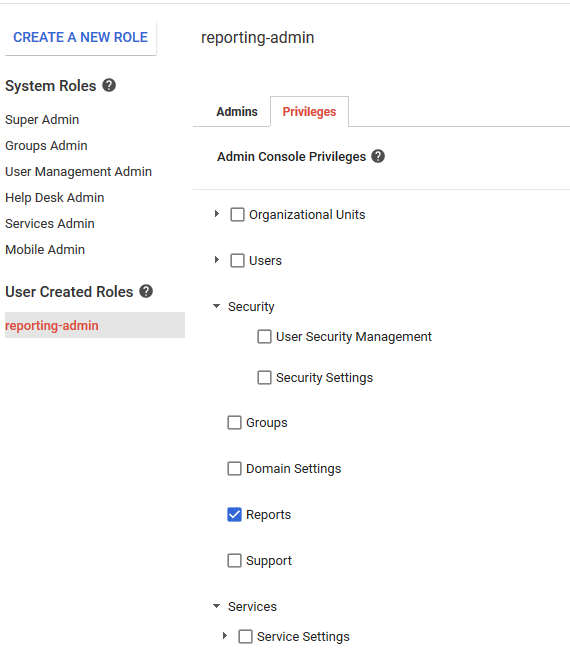
When you are configuring these permissions in the Google API, you only need to check off the Reports Privilege.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Google Apps in the event sources search bar.
- In the Product Type filter, select Cloud Service.
- Select the Google Apps event source tile.
- Select your collector and Google Apps from the event source dropdown.
- Name your event source.
- Optionally choose to send unparsed logs.
- Select your Account Attribution preference:
- Use short name attribution: The system first attempts to attribute data by email address, for example,
jsmith@myorg.example.com. If the first attempt is unsuccessful, attribution is attempted by short name, for example,jsmith. If the short name is unsuccessful, attribution is attempted by a user’s first and last name, for example,John Smith. - Use fully qualified domain name attribution: The system first attempts to attribute data by email address, for example,
jsmith@myorg.example.com. If the first attempt is unsuccessful, attribution is attempted by a user’s first and last name, for example,John Smith. This option is best if your environment has collisions with short names.
- Use short name attribution: The system first attempts to attribute data by email address, for example,
- Click Begin to set up OAUTH and start the authorization process.
- A new window or tab will open for you to perform an authorization grant with Google.
- Click Allow to enable audit reports for the G Suite Domain.
- Close the window/tab to return to SIEM (InsightIDR).
- Configure your default domain .
- Click Save.
SIEM (InsightIDR) also fetches a listing of all users via the users’ API.
Learn more
Google APIs use the OAuth 2.0 protocol for authentication and authorization. Google supports common OAuth 2.0 scenarios such as those for web server, installed, and client-side applications.
For more information, read this article: https://developers.google.com/identity/protocols/OAuth2 .