LDAP
Microsoft Directory Only
The LDAP event source is supported only for Microsoft Active Directory. Other directory services are not supported for use with this event source.
Adding a Lightweight Directory Access Protocol (LDAP) server allows SIEM (InsightIDR) to track the users, admins, and security groups contained in the domain. LDAP automatically mirrors data across all LDAP servers; thus, even if you have multiple LDAP servers, you will only need to configure one LDAP event source, unless you have manually disabled the auto-mirror feature.
Click here if you are using Azure in your environment.
Before You Begin
You need to document or change several things in your environment in order to successfully configure the LDAP event source.
- Ensure you have an Active Directory account with read access to user and group objects in the domain.
- You may use the same account that you are using to collect Active Directory event sources.
- If you are not using a domain admin and instead using a domain user, please ensure that you have “Read all properties” enabled under its effective permissions. If you’d like more information, you can read more.
- If you are using an LDAP Server, make sure that Port 636 (LDAPS) is open between the Collector and the LDAP server.
- If you are just using LDAP, make sure to open port 389 between Collector and LDAP server.
- Change or keep the default LDAP polling period, depending on your environment needs. Refresh Rate is measured in hours, with the default rate of 24 hours.
- Configure the BaseDN if your organization has changed the default tree structure. If your organization has not changed the default tree configuration, disregard the Base DN field in the LDAP event source configuration.
If you do not know how to configure the Base DN, see instructions here.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for LDAP in the event sources search bar.
- In the Product Type filter, select LDAP.
- Select the LDAP event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- In the “Server” field, enter the IP address or fully qualified hostname of the LDAP server (usually a domain controller).
- In the “Refresh Rate” field, enter the refresh rate in hours.
- In the “User Domain” field, enter the AD Domain. (NetBIOS / pre-Windows 2000 domain name)
- Select your domain user credential for performing the LDAP query, or optionally create a new credential.
- In the “Password” field, enter the password to access LDAP.
- If applicable, enter the value for your Base Distinguished Name in the “BaseDN” field.
- If applicable, enter the name of the group that has admin privileges in the “Admin Group” field.
- Click Save.
Windows Domain Base DN
When you use the Base Distinguished Name from your Windows domain, it should reference the topmost point in the LDAP tree that contains user data. The SIEM (InsightIDR) Collector uses the credentials supplied for the LDAP event source to collect the user information.
However, because the Microsoft Active Directory contains many different variables, you may need to try several different variables as the Base DN when configuring the LDAP event source:
- Option 1: Leave the field blank. The Collector will attempt to find the Base DN on its own when making the query. For most domains, the Collector can find the correct referral point and find all users in the domain without specifying a Base DN.
- Option 2: Provide the Base DN. See How to add the Base DN for instructions.
- Option 3: Provide the OU of your Domain. However, only fill out the Base DN field with the OU if SIEM (InsightIDR) cannot find all of users in your domain using the Base DN.
Find and Configure the Base DN
The Base Distinguished Name should point to the topmost point in the LDAP tree where user data is contained. If your organization has changed the tree structure from the default, or if you are not sure, you must find and provide the value.
After you find the Base DN, you can configure it on your LDAP server to accurately capture your user count. To find the appropriate root node:
- Log into the LDAP server. This is often the controller for the Windows domain for which you are adding an LDAP event source.
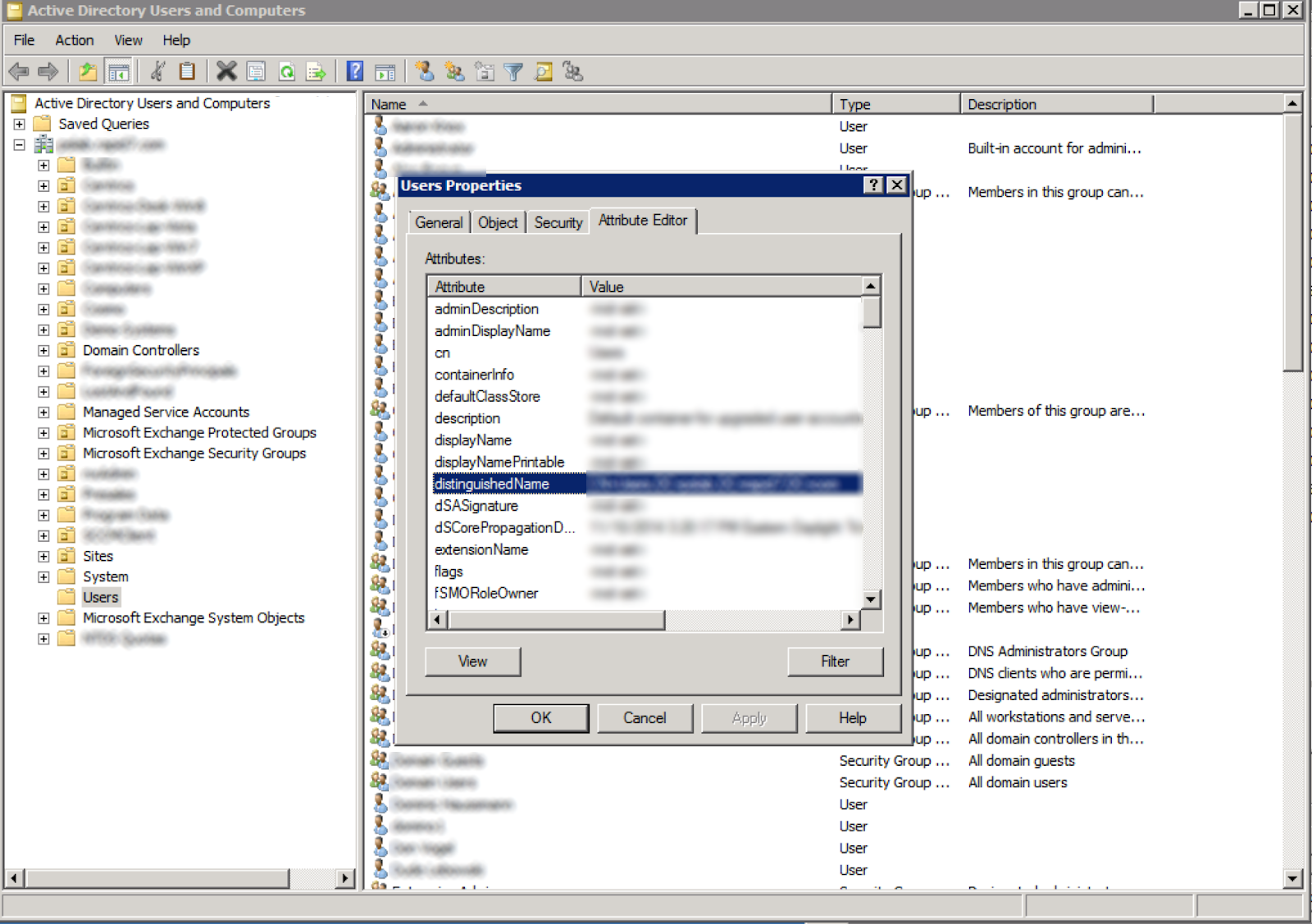
- Launch the Active Directory Users and Computers program.
- Right click on the node in the tree that corresponds to the LDAP Base DN of the domain.
Every Windows domain has one Base DN that will correspond to one of these locations:
- The distinguished name of the domain itself
- The first OU listed at top of the tree
- The first OU from the top that contains user objects
- The built-in Users OU
- Select the Properties tab.
- Select the Attribute Editor tab.
- Copy the “distinguishedName” value and paste it into the Base DN field of the LDAP event source configuration in SIEM (InsightIDR).
Azure and LDAP
Depending on the setup of Azure in your environment, you will need to configure the LDAP event-source in different ways.
Hybrid Cloud and On-prem
Configure LDAP as a normal event source for your on-prem instance, following the instructions above.
Replicated Domains If your domain is replicated into the cloud using Azure Active Directory, you do not need to configure an additional event source for the cloud domain.
Non-Replicated Domains If your domain is not replicated into the cloud with Azure Active Directory, you must setup an additional LDAP event source to cover your cloud domain. To do so, complete the following:
- Provision a VM to run an SIEM (InsightIDR) Collector within your Azure domain. You can also use this to retrieve the authentication activity for your domain.
- Install and register the collector in SIEM (InsightIDR).
- If hosting your own domain, configure the LDAP event source as normal to query from one of your domain controllers.
- If using the Azure AD Domain Services, configure LDAP for the managed domain controller.
LDAP for Managed Domain Controller
- Ensure that the VM running the collector is on the same subnet as the enabled Domain Services, or on a subnet with access to the Domain Services subnet.
- In the Azure portal, go to your “Azure AD Domain Service” resource. Under the “Manage” section, go to the Properties tab and find the IP Address on the Virtual Network.
- Take note of a user already existing in that domain. Or, add a new user to the same domain as the LDAP event source you will create.
- Note that this will force a password reset so that the domain controller can securely store a new password. See the Azure documentation for more information: https://docs.microsoft.com/en-us/azure/active-directory-domain-services/active-directory-ds-getting-started-password-sync
- Create an LDAP event source on that collector using the IP address specified in the Azure portal.
- Use the credentials of the user from step 3.
- Use the short name of the user without the domain suffix in the username field.
- For example, if the username was
jsmith@myorg.example.com, the short name would bejsmith
- For example, if the username was
- Click Save.
Note that the VM does not need to be joined to the domain in order to configure this event source.