Trend Micro OfficeScan
Trend Micro OfficeScan is a security and virus scanning product that can further contextualize data about your users.
Before You Begin
Trend Micro OfficeScan cannot send syslog directly to SIEM (InsightIDR). However, there are two methods you can use for SIEM (InsightIDR) to read Trend Micro data:
- Configure NXLog to capture OfficeScan events
- Configure Trend Micro Control Manager to forward syslog
You must be a Trend Micro OfficeScan administrator in order to configure any changes within the appliance.
Configure NXLog to capture OfficeScan events
To use NXLog to capture the OfficeScan events:
- Configure the OfficeScan event source in SIEM (InsightIDR)
- Configure OfficeScan to log its events into the Windows Application log
- Install NXLog onto the OfficeScan server and configure NXLog to collect the OfficeScan events and forward them to SIEM (InsightIDR)
Configure SIEM (InsightIDR) to collect data from the event source
Unlike other event sources, you should configure the Trend Micro OfficeScan event source before you configure the appliance itself.
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Trend Micro OfficeScan in the event sources search bar.
- In the Product Type filter, select Virus Scan.
- Select the Trend Micro OfficeScan event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Configure your default domain and any Advanced Event Source Settings.
- Select a collection method and specify a port and a protocol. For the Trend Micro OfficeScan event source, it is recommended that you select Syslog - TCP. Choose to encrypt the event source and download the Rapid7 Certificate.
- Note that you need to Rapid7 Certificate when configuring nxlog on the Trend Micro OfficeScan server.
- Click the Save button.
Configure OfficeScan Events
First ensure that the Trend Micro OfficeScan server events are written into the Windows Application log before events can be sent anywhere else.
To write server events to the Windows application log:
- Sign in to your Trend Micro OfficeScan console as the root user.
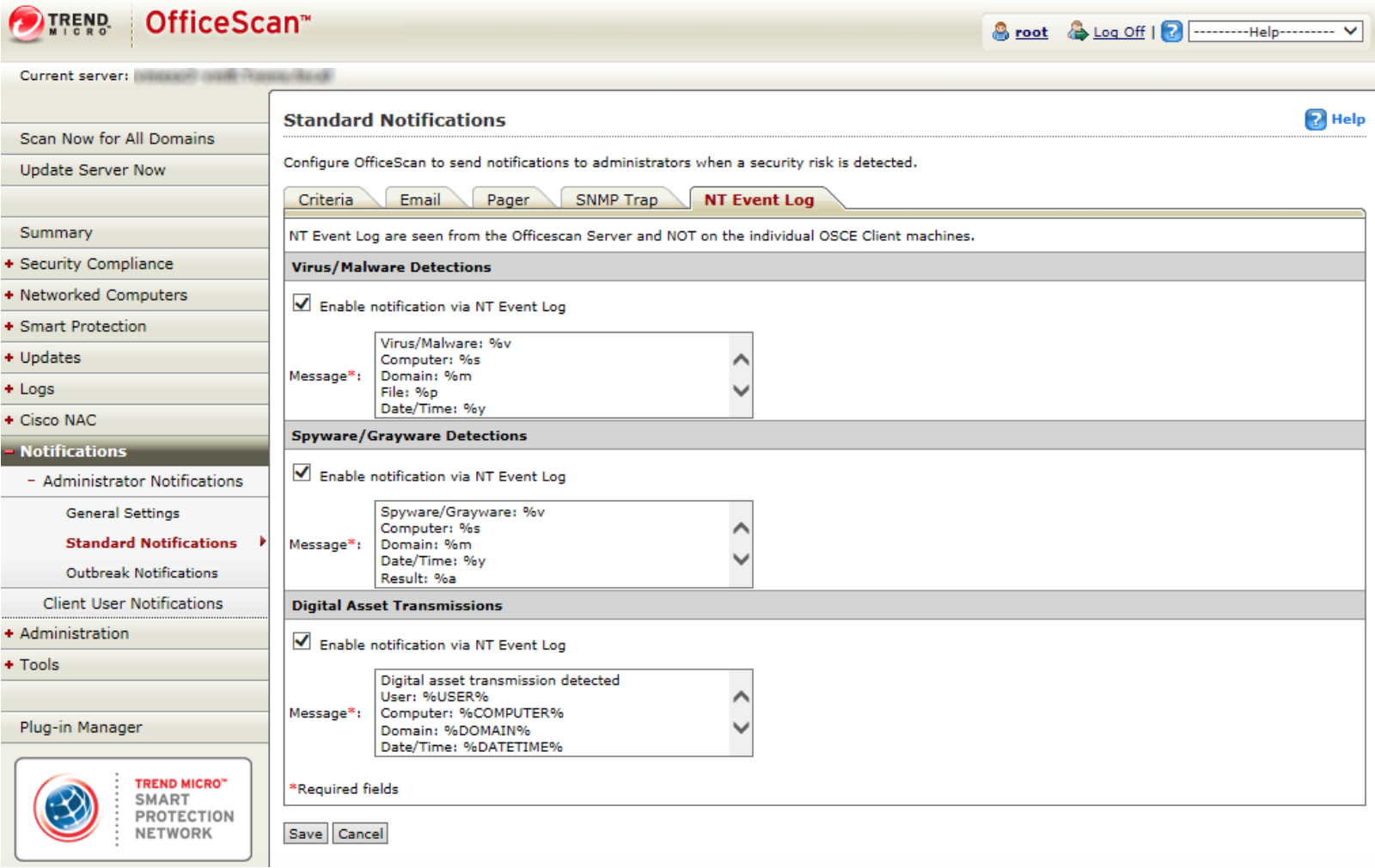
- On the left menu, select Notifications > Administrator Notifications > Standard Notifications.
- Select the NT Event Log tab on the right.
- In the “Spyware/Grayware Detections” section, check on the Enable notification via NT Event Log box.
- You can accept the default message, or modify the message using the following variables:
| Type | Variable | Description |
|---|---|---|
| Virus/Malware | %v | Virus/Malware name |
| Virus/Malware | %s | Endpoint with virus/malware |
| Virus/Malware | %i | IP address of the endpoint |
| Virus/Malware | %c | MAC address of the endpoint |
| Virus/Malware | %m | Domain of the endpoint |
| Virus/Malware | %p | Location of virus/malware |
| Virus/Malware | %y | Date and time of virus/malware detection |
| Virus/Malware | %e | Virus Scan Engine version |
| Virus/Malware | %r | Virus Pattern version |
| Virus/Malware | %a | Action performed on the security risk |
| Virus/Malware | %n | Name of the user logged on to the infected endpoint |
| Spyware/Grayware | %s | Endpoint with spyware/grayware |
| Spyware/Grayware | %i | IP address of the endpoint |
| Spyware/Grayware | %m | Domain of the endpoint |
| Spyware/Grayware | %y | Date and time of spyware/grayware detection |
| Spyware/Grayware | %n | Name of the user logged on to the endpoint at the time of detection |
| Spyware/Grayware | %T | Spyware/Grayware and scan result |
| Spyware/Grayware | %v | Spyware/Grayware name |
| Spyware/Grayware | %a | Action performed on the security risk |
- Click the Save button.
- Select the Criteria tab.
- In the “Spyware/Grayware Detections” section, select the Send notifications when spyware/grayware is detected radio button.
- Click the Save button.
You can read more information about Administrator Notifications from the following Trend Micro links:
- http://docs.trendmicro.com/en-us/enterprise/officescan-120-server-online-help/scanning-for-securit/security-risk-notifi/security-risk-notifi1/configuring-security.aspx
- http://docs.trendmicro.com/all/ent/officescan/v10.6/en-us/osce_10.6_olhsrv/ohelp/server/sriskadnotset.htm#XREF_37283_Administrator
Generate a Test Event
You can generate an event in OfficeScan to test whether or not events are being written into the Windows Application log as expected.
To do so, you can download a test malware file or string called “eicar” for this exact purpose. Follow the directions here: http://docs.trendmicro.com/all/ent/de/v1.5/en-us/de_1.5_olh/ctm_ag/ctm1_ag_ch8/t_test_eicar_file.htm
Configure NXLog
You can use NXLog to capture events from the OfficeScan server.
To do so:
- Install NXLog onto your Trend Micro OfficeScan server. Stop the NXLog service if it has started.
- Copy the Rapid7 Certificate to the location specified in the
nxlog.conffile, orC:\Program Files (x86)\nxlog\cert\Rapid7CA.pem - Replace the contents of the
nxlog.conffile with the following:
## See the nxlog reference manual about more configuration options
## It should be installed locally and is also available
## online at http://nxlog.org/nxlog-docs/en/nxlog-reference-manual.html
## Please set the ROOT to the folder your nxlog was installed into,
## otherwise it will not start.
#define ROOT C:\Program Files\nxlog
define ROOT C:\Program Files (x86)\nxlog
Moduledir %ROOT%\modules
CacheDir %ROOT%\data
Pidfile %ROOT%\data\nxlog.pid
SpoolDir %ROOT%\data
LogFile %ROOT%\data\nxlog.log
# Include fileop when rotating logs or while debugging
<Extension fileop>
Module xm_fileop
</Extension>
<Extension json>
Module xm_json
</Extension>
<Extension syslog>
Module xm_syslog
</Extension>
#This input module will read in TrendMicro events from the Windows Application log.
#First, configure TrendMicro OfficeScan to write its logs to the Application log.
#These events should go into the Application log on the TrendMicro OfficeScan server.
#The event codes for Trend are Event IDs 500, 600, 700, and 800. Check your application log
#and adjust this module to collect the events desired.
#Finally, the logs are forwarded to SIEM (InsightIDR) in Snare format. This is the format expected
#in the TrendMicro OfficeScan event source.
<Input eventlog>
Module im_msvistalog
ReadFromLast False
Query <QueryList> \
<Query Id="0"> \
<Select Path="Application">*</Select> \
</Query> \
</QueryList>
<Exec>
if ($EventID == 500 OR $EventID == 600 OR $EventID == 700 OR $EventID == 800) {$Message = replace($Message, "\t", " "); $Message = replace($Message, "\n", " "); \
$Message = replace($Message, "\r", " "); \
$raw_event = $Message; \
to_syslog_snare();} \
else drop();
</Exec>
</Input>
#This output module forwards the events to your SIEM (InsightIDR) collector using
#secure syslog. If you wish to use another output method, please see the nxlog documentation.
<Output ssl_tcp_out>
Module om_ssl
#Change this to the IP address of your Insight collector
Host 10.2.1.34
#Change this to the port the event source is configured to use
Port 5667
CAFile C:\Program Files (x86)\nxlog\cert\Rapid7CA.pem
#AllowUntrusted TRUE
</Output>
# If following other files, add to input path; i.e. eventlog, file1, file2 => ssl_tcp_out
<Route EventLog>
Path eventlog => ssl_tcp_out
</Route>- Edit the contents of the
nxlog.conffile to direct the Trend Micro OfficeScan events to the SIEM (InsightIDR) Collector. - Save the file and then start the NXLog service.
Verify the Configuration
To verify that this configuration works, look for events in SIEM (InsightIDR) that are in the following format:
2015-04-06 15:32:12 PVBTMAV.mycompany.com WARNING 500 NT AUTHORITY\SYSTEM Virus/Malware: Eicar_test_1 Computer: IT68 Domain: tor\Platte_city\ File: C:\Users\jsmith\Desktop\New Text Document.txt Date/Time: 4/6/2015 15:31:35 Result: Virus successfully detected, cannot perform the Clean action (Quarantine) Configure Trend Micro Control Manager
If you also have Trend Micro Control Manager, you can configure OfficeScan to forward its data to the Control Manager, which can then forward it to a syslog server. The following instructions are for Control Manager version 6.0.
To configure syslog forwarding:
- Sign in to the Control Manager console.
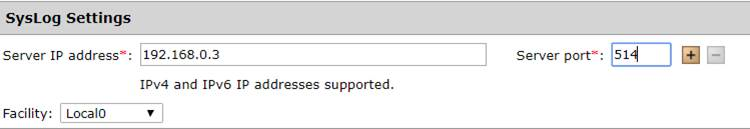
- From the top menu, select Administration > Event Center> General Event Settings.
- In the “SysLog Settings” box, enter the IP address of the SIEM (InsightIDR) collector and unique server port you want to receive OfficeScan data.
- Click the Save button.
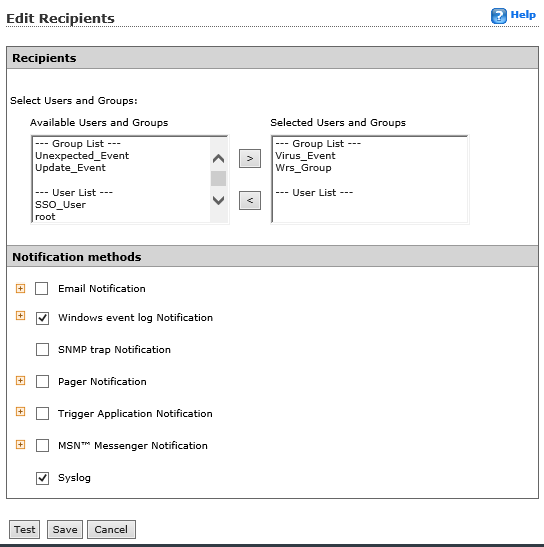
- From the top menu, select Administration > Event Center.
- Expand the Alert section and for each event, select the Recipients link.
- On the “Recipients” page, check on the boxes for Windows event log notification and Syslog.
- Click the Save button.
- Click the OK button to finish the configuration.
Not seeing log data?
SIEM (InsightIDR) only parses an event from your Virus Scan event source when a virus is found.