Exploitable Vulnerabilities
You can connect Vulnerability Management (InsightVM) or Nexpose, Rapid7’s vulnerability management solutions, with SIEM (InsightIDR) to see all the exploitable vulnerabilities found in your environment. SIEM (InsightIDR) applies user context to vulnerabilities, showing you which users may be “clickbait.”
How to View Exploitable Vulnerabilities
On the Assets & Endpoints page, you will see a card that displays the top Exploitable Vulnerabilities on the right, along with the number of assets affected. At the bottom of the card, you can click More to see the top 100 vulnerabilities.
You can also click on the Exploitable Vulnerabilities metric on the “Assets & Endpoints” page to see a complete list.
The Top 100 Vulnerabilities displays information about the exact title, the threat source count, the type of vulnerability, and the number of users and assets affected. You can sort these columns by clicking on them.
How to view vulnerability details in Alerts
If you are using SIEM (InsightIDR) with Vulnerability Management (InsightVM), you can view vulnerability details in Alerts . As SIEM (InsightIDR) collects data from your environment, detection rules look for known threats, risks, and unusual actions. These detection rules can then trigger alerts, investigations, or other types of notifications when an event occurs that meets the detection rule logic.
In Alert Details, you can see a table of all known Vulnerability Management (InsightVM) Vulnerabilities related to the alert, helping you to understand the root cause of an alert, take appropriate action, and prioritize a vulnerability for remediation.
Correlation
Vulnerabilities are only displayed in Alerts if there is sufficient data available to correlate them with the asset associated with this alert.
Some event types are less likely to correlate with assets as an IP address is available in the event data. When asset correlation isn’t successful, associated vulnerabilities won’t appear in alerts. This is expected behavior.
Event types with low correlation accuracy include:
- Firewall events
- DnsQuery events
- NetworkFlow events
- AdvancedMalware events
- WebProxy events
- Process start events
- Sysmon events
- FileAccess events
The following contextual information is available in Vulnerability Management (InsightVM) Vulnerabilities in Alerts Details:
- CVE: The CVE (Common Vulnerabilities and Exposures) ID is provided and links to additional information.
- Risk Score: A risk score, based on the Vulnerability Management (InsightVM) Active Risk strategy . Active Risk is Rapid7’s recommended built-in strategy for assessing and analyzing vulnerability risk on a scale of 0-1000. Active Risk uses the latest CVSS score with intelligence from threat feeds like AttackerKB, Metasploit, ExploitDB, Project Lorelei, CISA KEV list, and other third-party dark web sources to provide security teams with a threat-aware vulnerability risk score and to help prioritize remediation for the most critical vulnerabilities.
- Exploits: States whether or not an exploit exists for this vulnerability.
- Last Assessed: The date that the vulnerability was first reported.
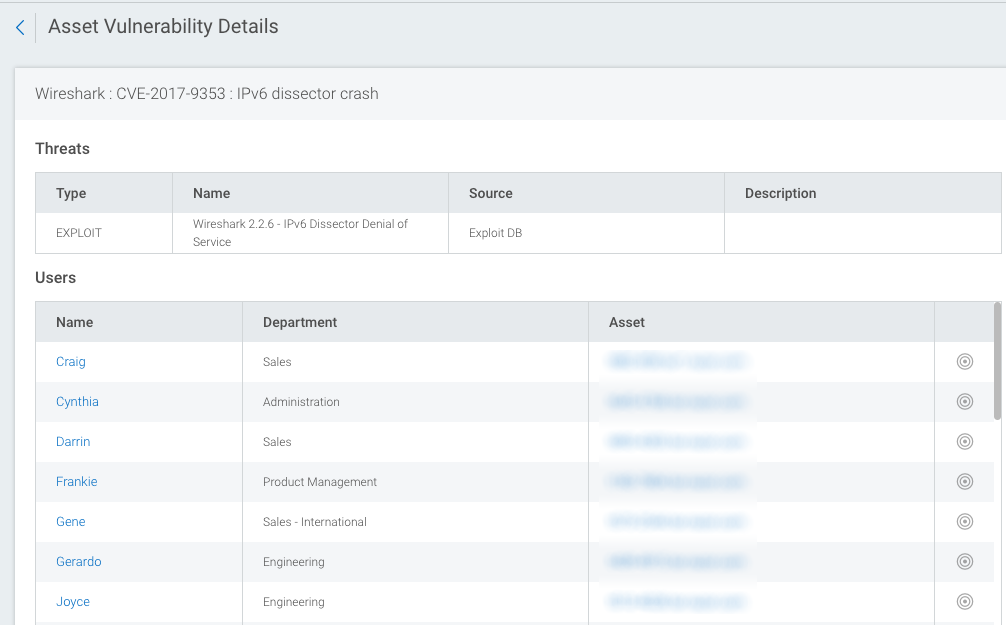
Asset Vulnerability Details
When you click on the title of the vulnerability, you will see a detailed page about it. It will display additional information about the type, name, source, and description of the vulnerability.
The Users table then displays the name of the user, their department, and their affected asset. You have the option of restrict their asset by clicking on the Target icon.
How to Connect Vulnerability Management (InsightVM) or Nexpose
Please see Nexpose/InsightVM Integration for instructions.