Filter your event source data
When configuring event sources that send unwanted log events or high volumes of noise, you can add a filter to eliminate specific events from being captured in SIEM (InsightIDR).
This feature is a support-enabled feature
Please contact Rapid7 support to work with our team to enable this functionality.
To add a filter:
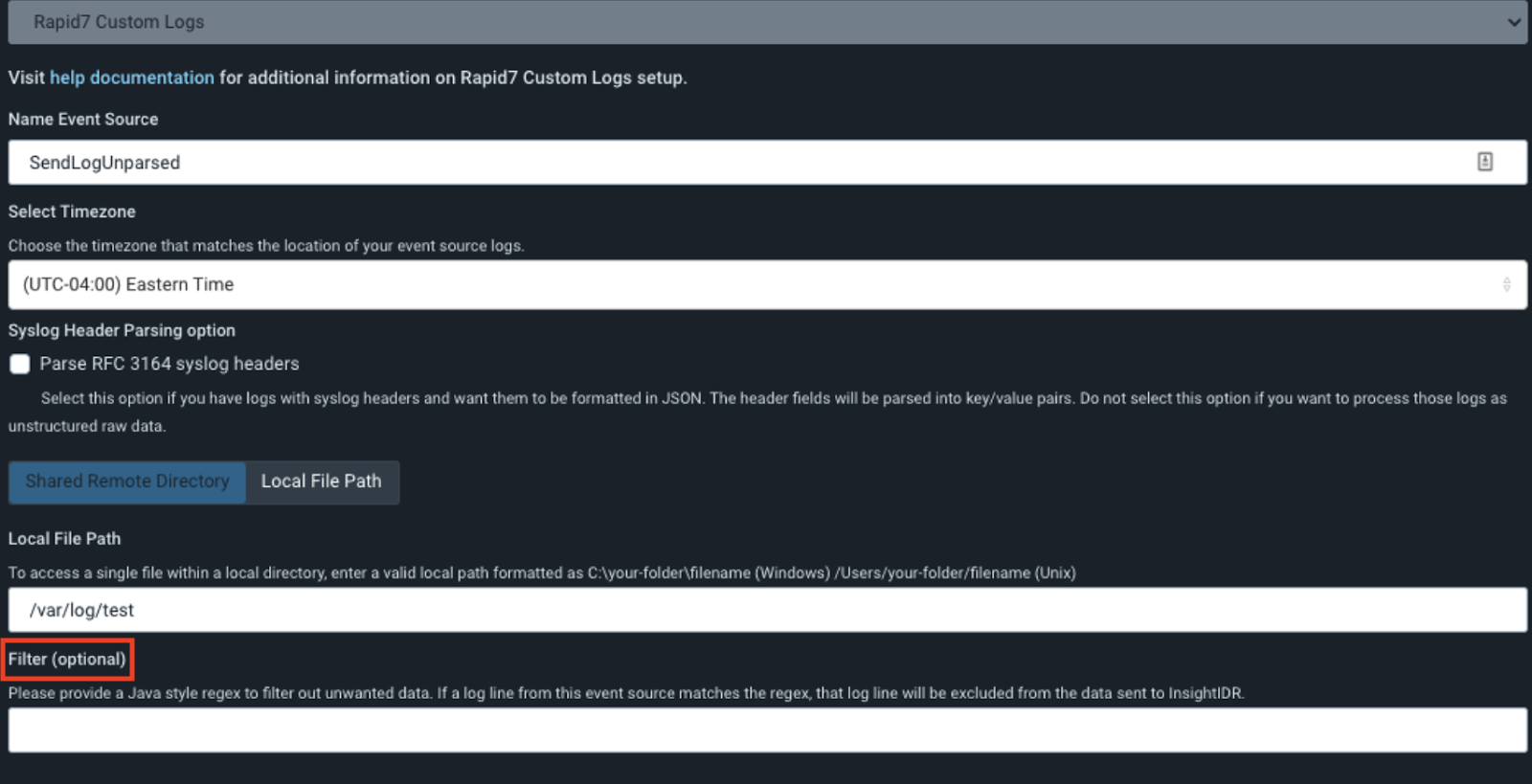
- From the Data Collection screen, add a new event source or edit an existing one.
- To add a new event source, click the Setup Event Source dropdown menu and select Add Event Source. Choose the event source you would like to add and follow the documentation to configure that event source.
- To edit an existing event source, click Edit event source.
- In the Filter section, enter a Java-style regex to filter out unwanted data. If a log entry from this event source matches the regex, that log entry will be excluded from the data sent to SIEM (InsightIDR).
- Click Save.
You cannot retrieve excluded events
If the event source filter is used to exclude log entries, that data cannot be retrieved. The Collector does not store dropped events locally or upload dropped events to the Command Platform (Insight Platform).
Use these best practices when creating your regex:
- You can use these regex character sets and operators to build out your query.
- The regex you enter needs to match the entire log entry; it cannot contain only a partial match. For example, if you would like to exclude this log entry:
Jul 31 03:46:01 ip-172-21-26-154 anacron[9629]: Job `cron.daily' terminated, you could write the regex as.*cron.daily.*. This regex is case sensitive and would exclude all log entries that contain the stringcron.daily. - In regex, the
.*before and after the string indicates that any character, zero or more times, can appear before or after the string. For example, using the same log above, you might want to eliminate all logs that containanacron[9629]:and were terminated. In this case, you could write the regex as:.*anacron\[\d+\]:.*terminated.*. - If you wish to only collect log events which match a particular pattern, you can use a lookahead regex, such as
.*^((?!anacron).)*$.*. This regex will match on every log entry which doesn’t containanacron, meaning the log events being collected must contain the stringanacron, otherwise they will be dropped. - You can validate and test your regex using regular expressions 101: https://regex101.com/ . This site allows you to drop sample log events as the target and write your regex pattern to match.
Use Log Search to ensure your regex does not match on wanted data
When writing your regex, you should ensure that wanted data is not matched on by mistake as this data will not be able to be retrieved. To test which events would not be collected if the event source filter was configured, you can enter your regex pattern into the Log Search query bar. Here, you can verify that you will only drop logs that you do not need.