Cloud Security (InsightCloudSec)
Cloud Security (InsightCloudSec) (previously DivvyCloud) provides real-time analysis and automated remediation for cloud and container technologies, protecting them from misconfiguration, policy violations, threats, and IAM challenges. If you have a valid InsightCloudSec license, you can send cloud events to SIEM (InsightIDR) for analysis, investigations, reporting, and more.
To send InsightCloudSec data to SIEM (InsightIDR):
- Deploy and configure a collector.
- Set up an event source in SIEM (InsightIDR).
- Configure Cloud Security (InsightCloudSec).
- Verify the Configuration.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Rapid7 Cloud Security (InsightCloudSec) in the event sources search bar.
- In the Product Type filter, select Rapid7.
- Select the Rapid7 Cloud Security (InsightCloudSec) event source tile.
- Choose your Collector.
- In the Name Event Source field, name your event source.
- Specify a port. You will need to enter this port information in Cloud Security (InsightCloudSec).
- Click Save.
Configure Cloud Security (InsightCloudSec)
To send data to SIEM (InsightIDR), you must provide Cloud Security (InsightCloudSec) with the Collector IP and the port you specified when configuring the event source in SIEM (InsightIDR), and then trigger the pre-configured SIEM (InsightIDR) Bot action.
Set up an Integration
- From the Cloud Security (InsightCloudSec) left menu, select Administration > Integrations.
- On the Integrations page, locate the SIEM (InsightIDR) tile, and click Edit.
- In the Connector IP field, enter the Collector IP.
- In the Port field, enter the UDP port the Collector is listening on.
- You must ensure that all firewall and security group rules are in place within the cloud/network location where the Collector is hosted. This allows communication between the Cloud Security (InsightCloudSec) instance and the Collector.
- To submit and save the integration settings, click Save.
Trigger the Pre-Configured SIEM (InsightIDR) Bot
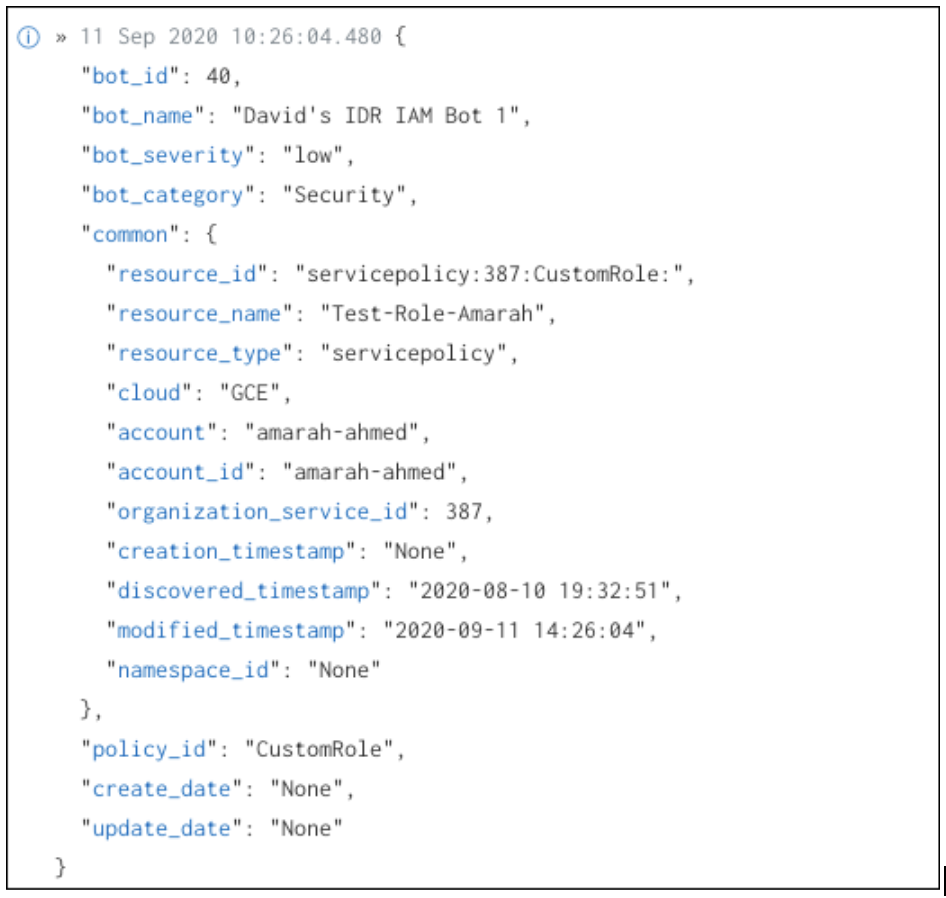
Cloud Security (InsightCloudSec) includes a default Bot action that exports a pre-formatted data block that includes the bot name, filter information, and resource information. Once you configure your Collector and a Custom Log event source, trigger the bot to send logs to SIEM (InsightIDR):
- Search for “IDR” to locate the SIEM (InsightIDR) Event bot action. This action allows SIEM (InsightIDR) to ingest Cloud Security (InsightCloudSec) data without any additional SIEM (InsightIDR) configuration.
- To test the bot, select the On Demand Scan option. This manually triggers the bot and sends data to SIEM (InsightIDR) based on pre-defined criteria. The data provides details on the resource that triggered the bot, including all configuration data for that resource.
- For additional information, see the Cloud Security (InsightCloudSec) Bot Factory documentation. To read more about the SIEM (InsightIDR) and Cloud Security (InsightCloudSec) integration, see https://docs.rapid7.com/insightcloudsec/insight-idr-integration/ .
Verify the Configuration
Complete the following steps to view your logs and ensure events are making it to the Collector:
- From the left menu, click Log Search and select Raw Logs.
- Next, perform a Log Search to make sure your events are coming through. Be sure to cross-reference your logs with existing malops. If there have not been any new malops in the last 24 hours, there will be no logs to view.
Sample Logs
This is an example of the SIEM (InsightIDR) bot action output: