The Credentials Page
The Credentials UI
The Credentials page is where you can manage credentials, bruteforce target hosts, or setup a workflow to reuse credentials against targets.
You can access the following sections from the Credentials dropdown:
Manage credentials
After navigating to “Credentials”, the manage screen is the first page you encounter. From here you can import credentials, add them manually, or remove them .
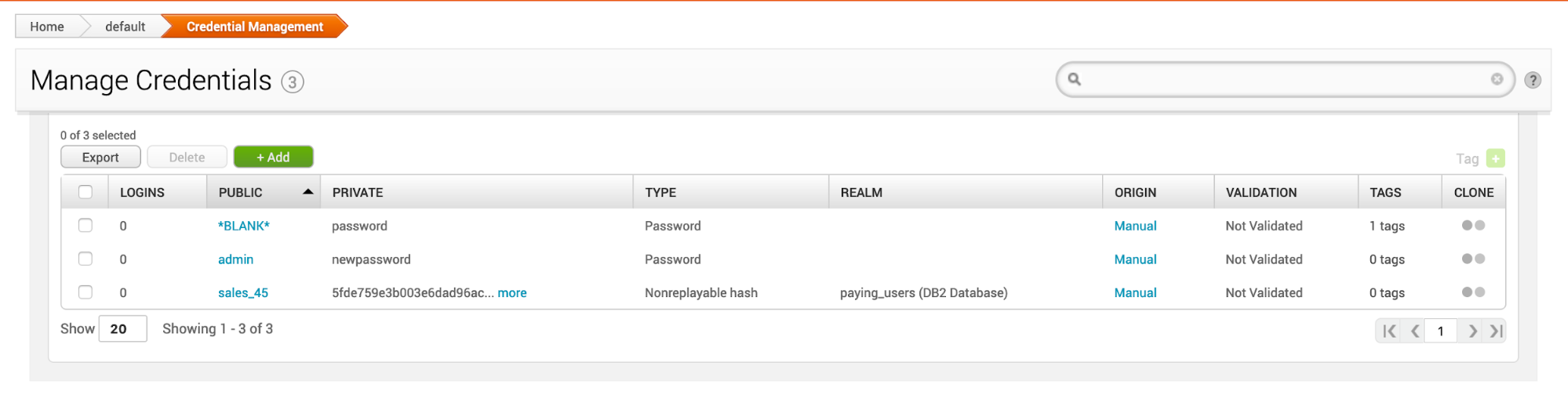
- Logins - The number of times the credentials were used to login successfully to a target.
- Public - The username that used to log in to a target.
- Private - The password that is used to authenticate to a target. It is usually a plaintext password, an SSH key, NTLM hash, or nonreplayable hash. Since the private key can be an SSH key or hash, the term ‘password’ is not broad enough to cover these private types.
- Type - The type of password. This can be a ssh key, NTLM hash, nonreplayable hash, or password.
- Realm - The functional grouping of database schemas to which the credential belongs. A realm type can be an Active Domain Directory, a Postgres database, a DB2 database, or an Oracle System Identifier (SID). A public, private, or credential pair can have a realm, but it is not mandatory. You can give each realm a custom name to identify it.
- Origin - Identifies how the credential was obtained or added to the project, such as through Bruteforce, manual entry, or an imported credentials list. An origin can be manual, import, session, service, or cracked password.
- Validation - Validates if the credentials were used to login successfully to a target.
- Tags - Organize hosts and data by using labels to group information.
- Clone - Makes a copy of the credential. When cloning, you can edit the information before saving.
Reuse credentials
The Credentials Reuse page allows you to reuse validated credentials against targets in brute force attacks by setting up workflows .
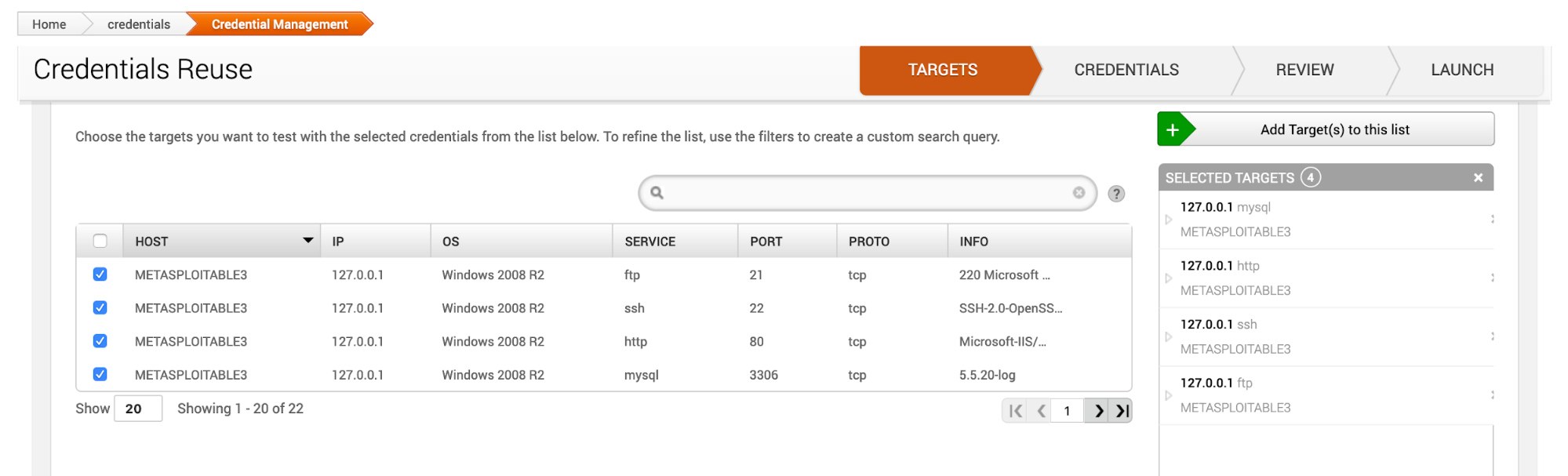
Targets
Add existing targets to the attack. The information is automatically populated from the hosts.
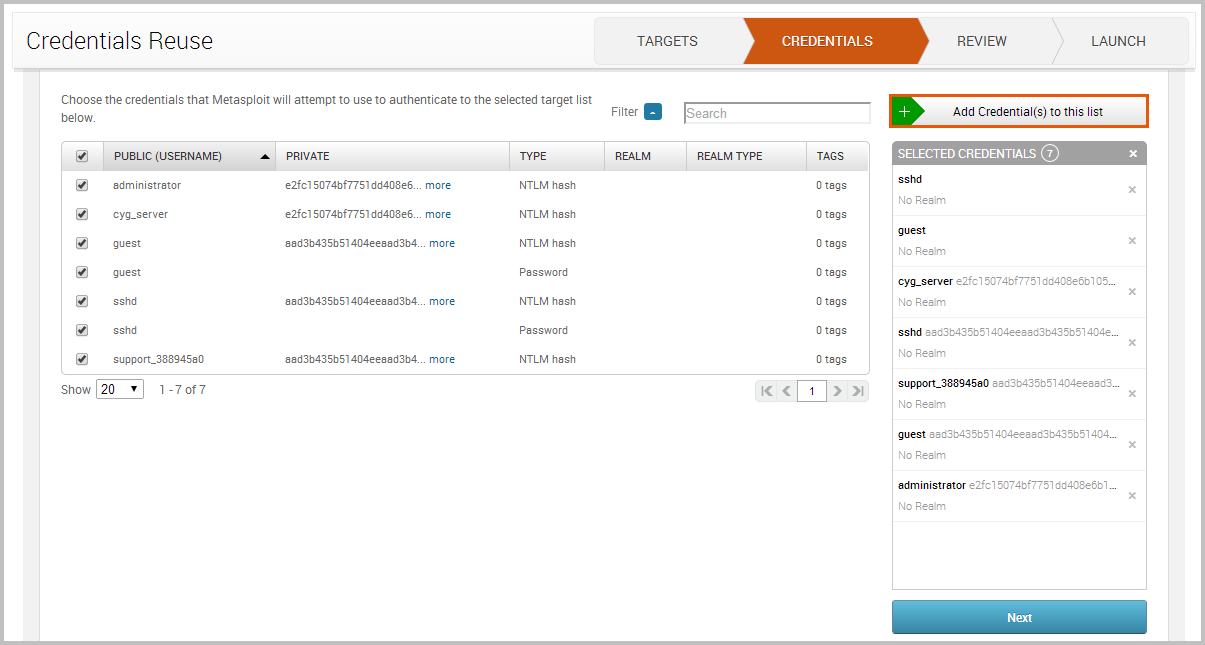
Credentials
Add existing credentials to be used against the target hosts. Credentials must be added from the Manage page.
Review
Review the settings and set brute force attack options.
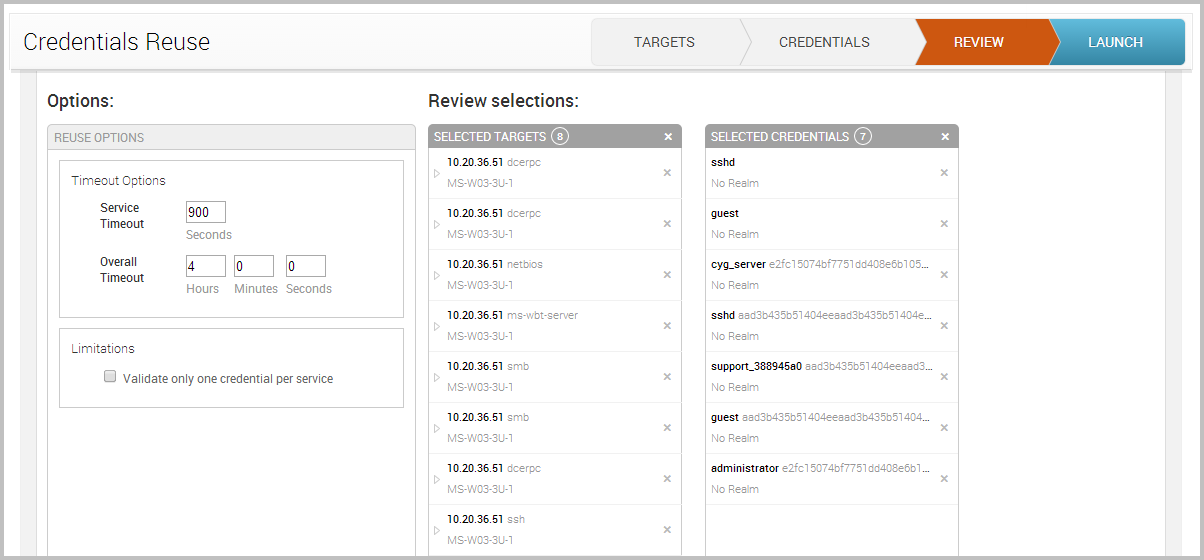
- Service Timeout - Sets the timeout, in seconds, for each target.
- Overall Timeout - Sets the timeout for the entire Credentials Reuse task.
- Validate one credential per service - Limits the number of credentials that are validated for a service on a host to one. Once a credential has been validated for a service, Credentials Reuse will stop testing with other credentials.
Launch
Launch will start the brute force attack using the credentials and configured hosts.
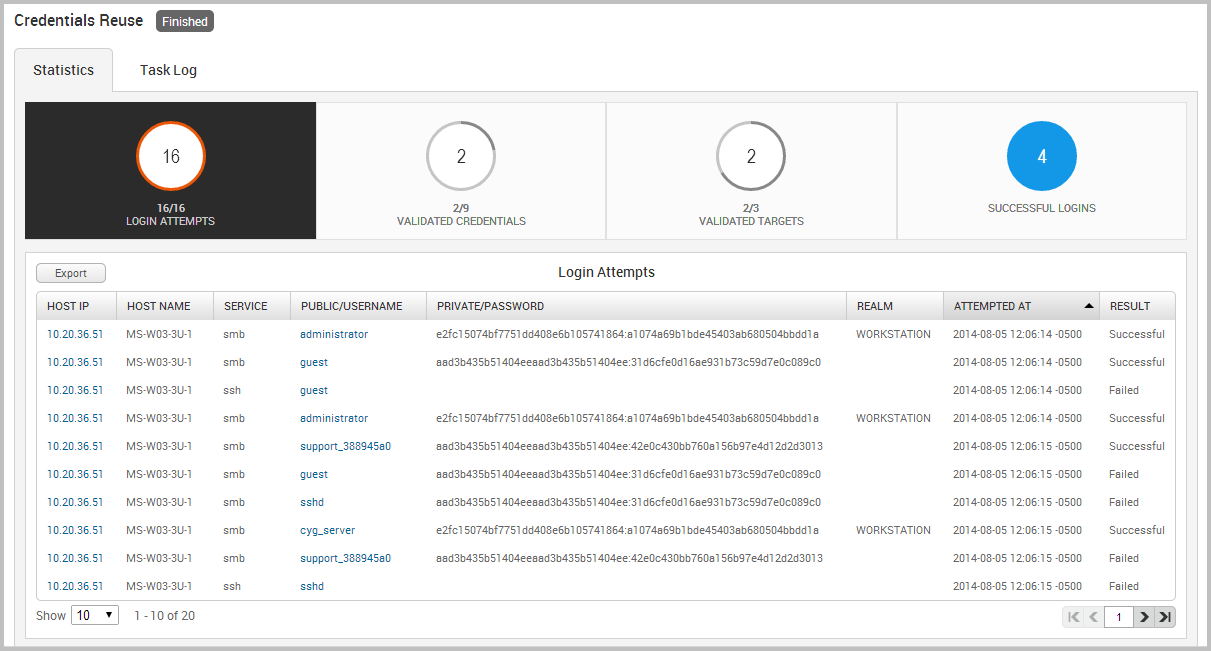
- Login attempts - The total number of login attempts that were made.
- Validated targets - The total number of targets that were validated.
- Successful logins - The total number of logins that were successful. This number is derived from the number of validated credentials and validated targets.
Bruteforce credentials
The Bruteforce page allows you to choose targets and credentials to open a session on a target host.
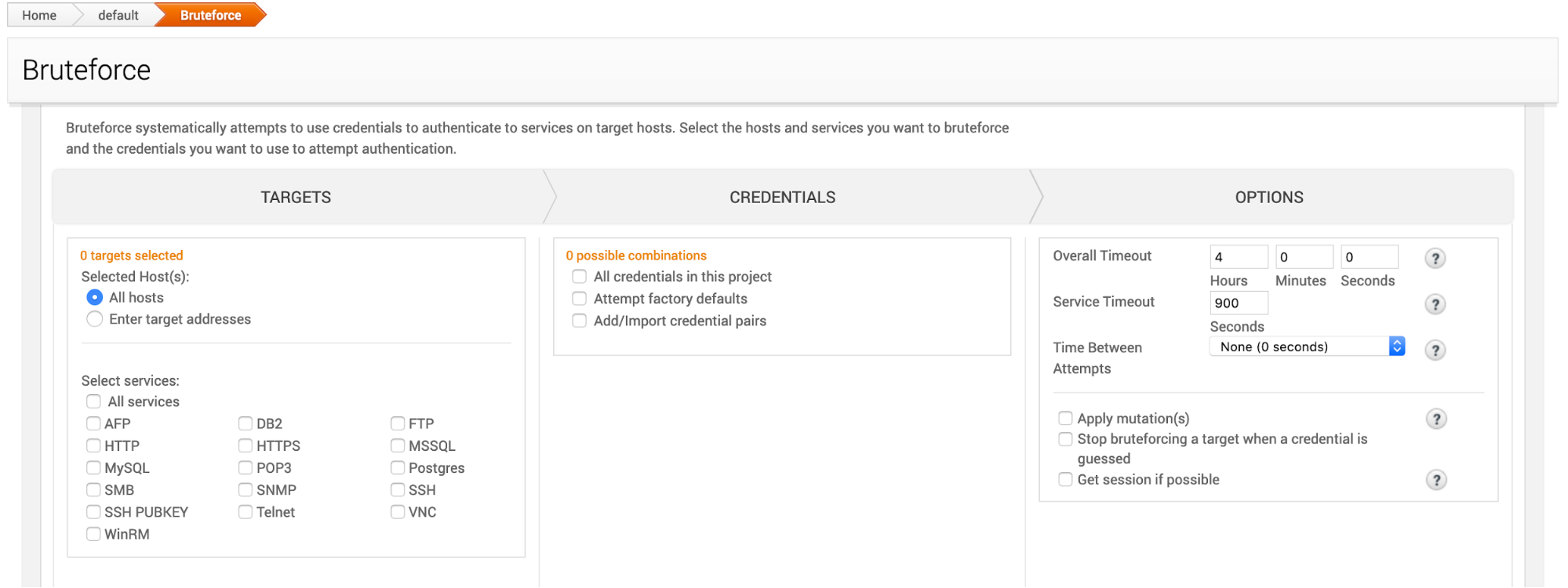
Bruteforce is broken into three sections:
Bruteforce Targets
Targets is where you will set the target host address and the services the target is running to attack
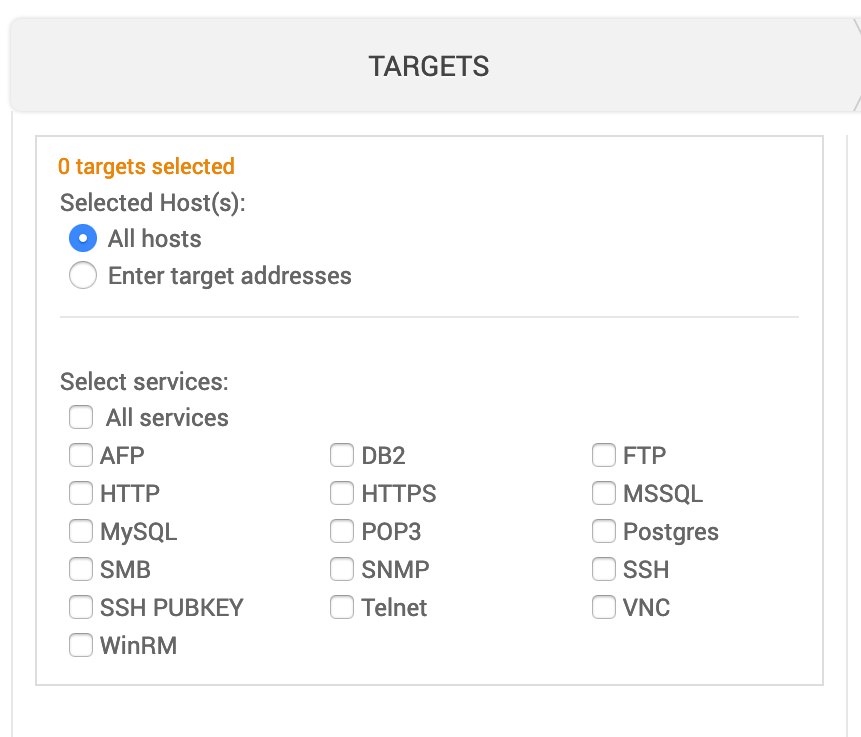
Selected Hosts
- All hosts - Select if you want to target all hosts in the project.
- Enter target addresses - Enter the address of the target. You can enter them as:
- Single address (192.168.1.1)
- Range (192.168.1.1-192.168.1.100)
- CIDR notation (192.168.1.0/24)
- Wildcard (192.168.1.*)
Selected Services
You can select all services or pick the ones to target. At least one must be selected.
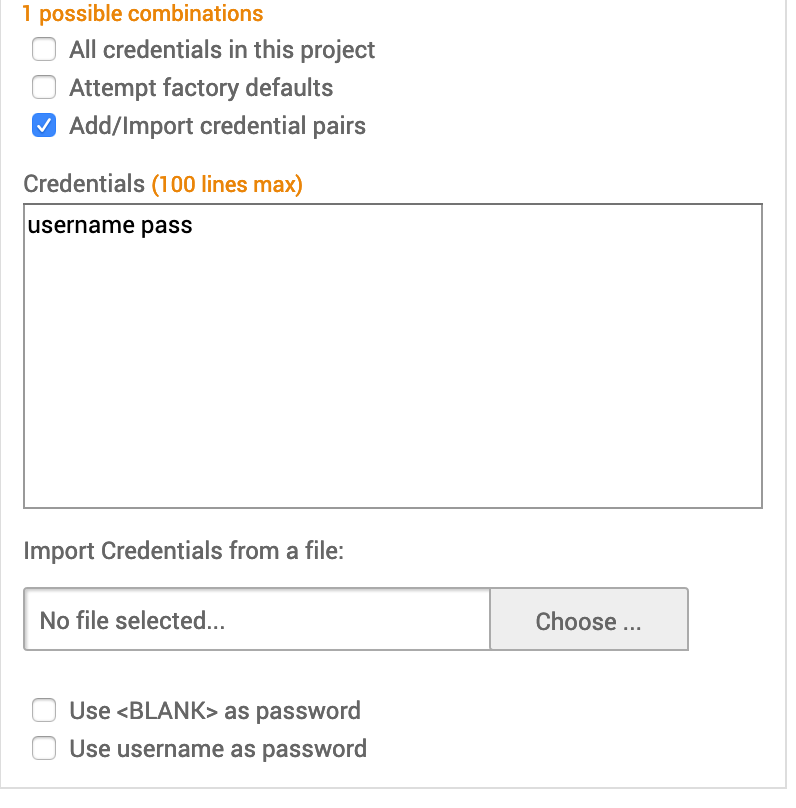
Bruteforce Credentials
Select the credentials to be used in the attack.
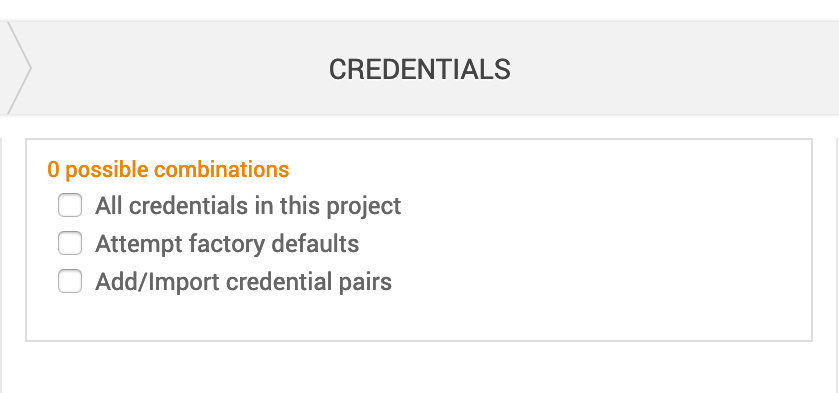
- Possible Combinations - This number will increase or decrease depending on the number of credentials being tested as you set options. The more combinations, the longer the attack will take.
- All credentials in this project - Any credentials saved in the project under Manage Credentials will be attempted.
- Attempt factory defaults - Default credentials are username and password pairs that are shipped with an operating system, database, or software.
- Add/Import credentials pairs - This option will open more configuration options.
- Credentials - Enter up to 100 username and password pairs
- Import credentials using a text file.
- Use <BLANK> as password - Generate a blank username for each password in the list. For example, if the password list contains a credential pair like ‘admin’/‘admin’, Bruteforce will also try admin/‘<BLANK>’.
- Use username as password - Check if you want to use a username as a password. For example, if the password list contains a credential pair like ‘user’/‘pass’, the bruteforce attack will also try ‘user’/‘user’.
Bruteforce Options
Set the configuration for a bruteforce attack.
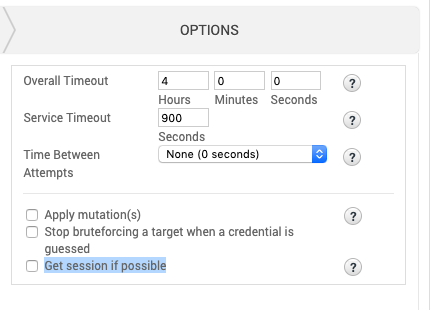
- Overall Timeout - Set how long the attack will run before stopping for the whole attack.
- Service Timeout - Set how long the attack will run for each target before stopping.
- Time Between Attempts - Set the time between each attempted.
- Apply mutation(s) - Apply mutations rules to a password. Mutations can be used to create permutations of a password, which enables you to build a larger wordlist based on a small set of passwords
- Stop bruteforcing a target when a credential is guessed - Stop bruteforcing on a target once a credential is guessed. It does not stop the entire attack if there are more targets.
- Get session if possible - Enable if you want Bruteforce to attempt to obtain a session when there is a successful login attempt to MSSQL, MySQL, PostgreSQL, SMB, SSH, telnet, WinRM, and HTTP.