Aug 03, 2018
Release 18.5, our first release of the Summer, introduces a variety of additional cloud support across Google Cloud Platform and Amazon Web Services, enhanced visualizations and cloud coverage reporting, cost visibility/governance, Kubernetes support, Insight exemptions, dozens of bug and performance improvements and more. Customers running older versions are strongly encouraged to upgrade to take advantage of the new features and functionality.
To see comparisons of what has changed in 18.5, please see What’s New. Upgrade Prerequisites
Important
Before upgrading your DivvyCloud installation, please take a moment to view our Administrator and Developer Notes at the bottom of this page or contact support@divvycloud.com for questions.
Release Highlights
Additional Cloud Support/Enhancements
Kubernetes
- Add the ability to interconnect a Kubernetes cluster into the tool
- Support Nodes
- Support for Pods
- Support for Containers
- Support for Services
- Support for Ingresses
- Support for Deployments
- Support Node mapping to cloud instances.
Google Cloud Platform
- Find all projects via Organizations
- Auto-enable API option
- Support for API visibility
- Support for GKE (Google Kubernetes Engine)
- Support for Directory (Users/Groups)
- Support for IAM (Roles/Service Accounts)
- Support for Dataproc
- Support for Spanner
- Support for VPC Network Peers
- Support for BigTable
- Support for FileStore
Amazon Web Services
- Support for Kinesis/Firehose
- Support for Elastic Map Reduce (EMR)
- Support for CloudSearch
- Support for VPC NAT Gateways
- Support for Linux Workspaces
- Support for storage/filtering of VPCs with multiple IPv4 CIDR blocks
- Region/domain name are included with ACM SSL Certificates
- Root account information is now surfaced within service users
Insight Exemptions
Insight exemptions have historically been done using resource tags and adding one or more additional filters to exclude resources that contain the tag key(s). This approach is problematic when setting up dozens of Insights and is compounded by the limitation of cloud providers not supporting tags across all resource types. Further, by using tags, compliance auditors open the door to users working around guardrails by manipulating (intentionally or accidentally) the tag key(s) used by Insights to maintain exemptions.
This new feature allows administrators to leverage Resource Groups as a means of facilitating resource exemptions in a more accessible, scalable, and secure manner.
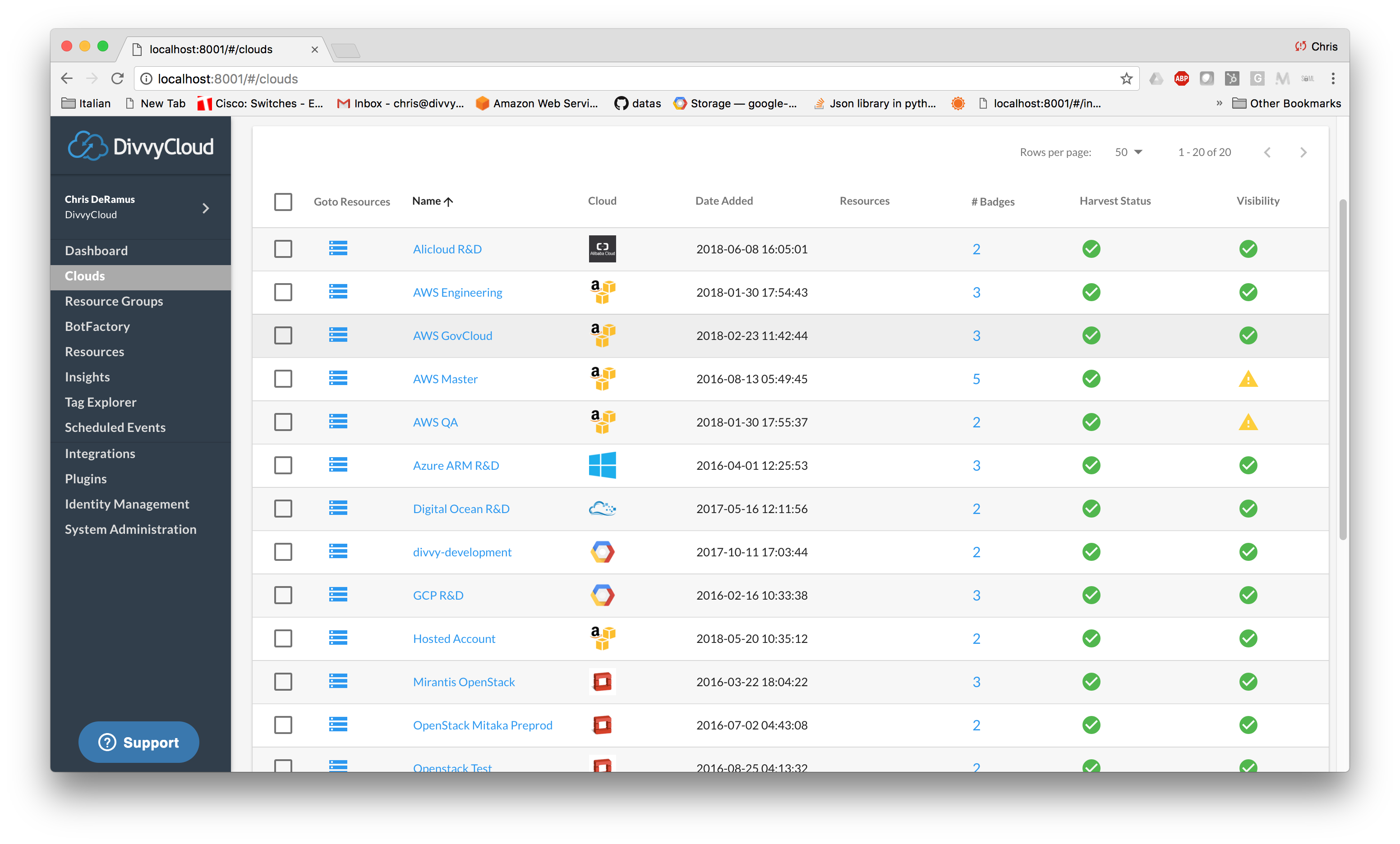
Cloud Visibility View
Harvest status and resource visibility status are now broken into separate columns to avoid confusion. Harvest status is now isolated to three values: Running, Paused, Impaired. Invalid/missing permissions that can impact resource visibility into the cloud are now viewed in a separate column. The rightmost column in the screenshot below illustrates this callout.
Associate Badges With Packs
Oftentimes, pack authors want to associate scope with an Insight pack. This enhancement allows the author to associate one or more badges with a Insight Pack which will define the cloud scope and sync scope going forward with badges. As an example, perhaps the author wants to focus on NIST 800-53 compliance, but only want to analyze it against production accounts. Adding the badge environment:production allows the pack to 1) examine only production accounts and 2) automatically include production accounts as they are added in the future.
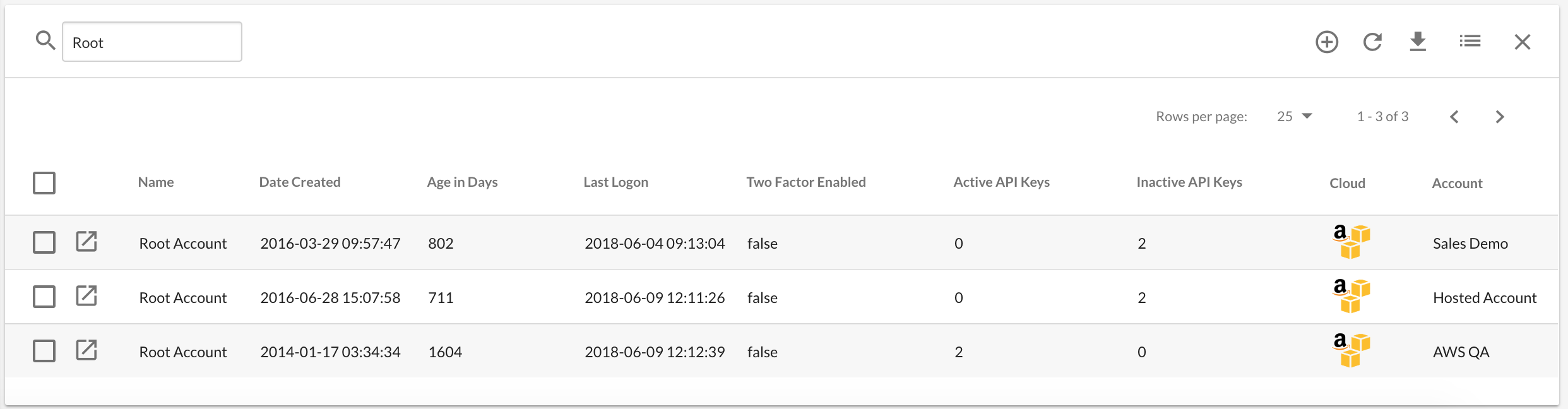
Root Account Information
Securing your root credentials is a vital piece of Cloud security and compliance. Now with the addition of the root account, administrators can quickly get visibility across all of their root accounts including the last time that the account was used, if it has two-factor, and the count of active/inactive API credentials.
Include Tags When Browsing Resources
When managing resources or browsing the results of Insights, customers can now include up to five tags within the resource listing. This enriches the view and provides additional metadata about targeted resources. As an example, when Instances exposing SSH are identified you can include the Owner tag to track down who owns the resource. This data is also included when exporting the results as a CSV report.

Tag Explorer - Saved Configurations
Tag Explorer has been a powerful tool for filtering and analyzing lots of resources with given tag keys. With this release, users can now save their tag configurations for future use or sharing with other users. The previous Tag Explorer page has been reworked into a detail view and another page with “Saved Configurations” was added to display the complete list of all saved configurations.
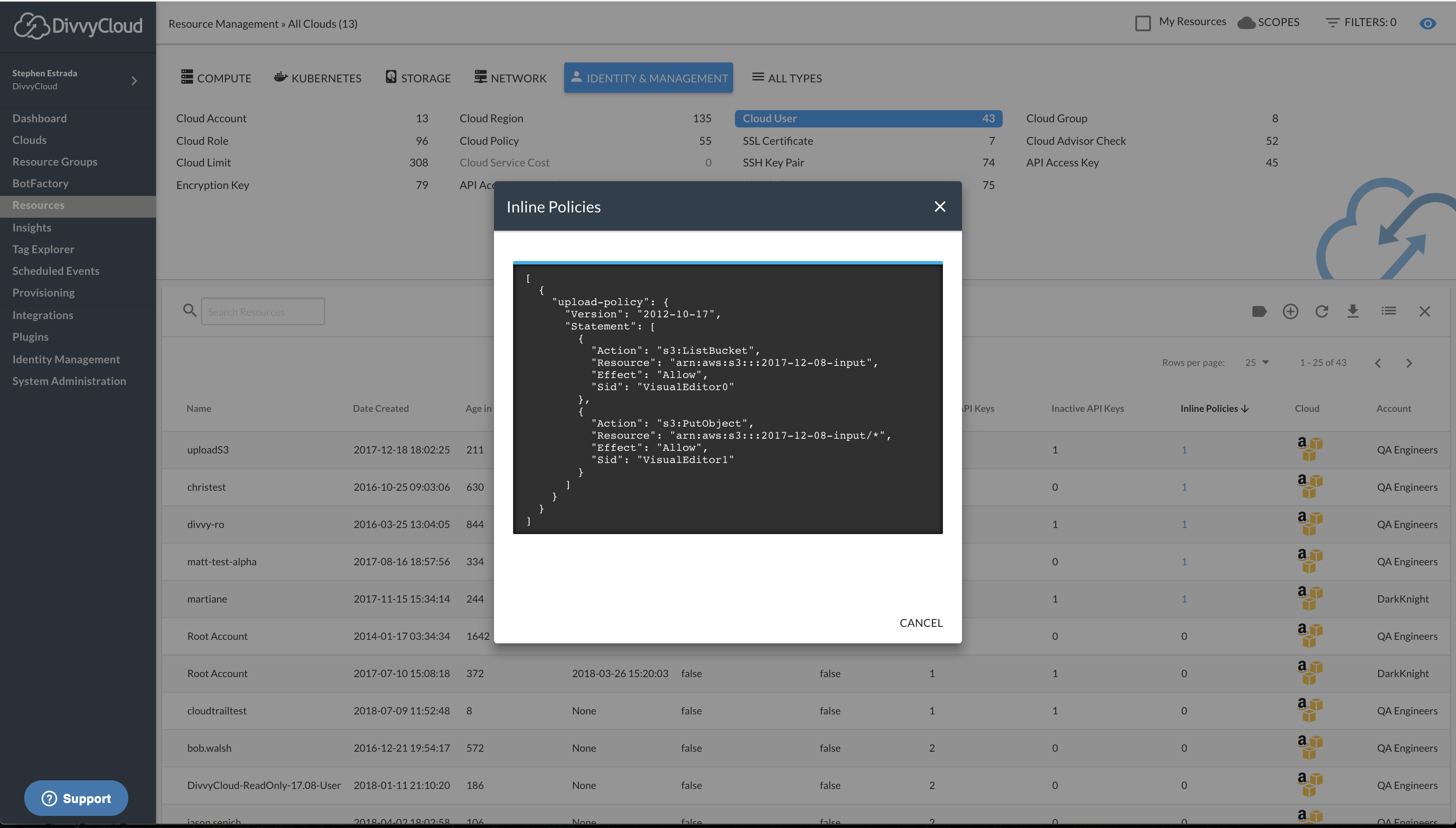
AWS Inline Policy Support
AWS inline policies are now viewable through the DivvyCloud tool. This includes support for Groups, Roles and Users.
General Enhancements
- AWS accounts impaired due to the inability to assume role are monitored and surfaced in the tool
- Improved display of JSON when updating IAM Policies
- When viewing instances, the network/VPC ID is now included in the view
- Added tag query support to Shared File Systems
- Added tag query support to Public IPs
- Added a flag to the bot overview when the bot runs on a schedule
- Added ‘event.bot_id’ and ‘event.bot_name’ parameters for fields that support Jinja templating
- When editing badges for clouds and organizations, the name of the cloud or organization is displayed in the title bar of the dialog box
- API keys are shown as a dependency when viewing detailed information for Service Users
- Bot actions “Send Bulk Email” and “Send Email Summary With CSV” support the ability to skip previously identified resources/duplicates
- Added ability to delete custom insights from SOURCE: ALL view
- Added ability to create Organization Admins for non-local accounts
- New API endpoint to export resource data in JSON format
- Added ability for domain admins to force a refresh of their license
- Severities for Insights now displayed as English words instead of numbers
- Adding cloud accounts displays a confirmation dialog if system recognizes a duplicate account identifier on submit
- Toggling scopes within the Resources section of the tool remains sticky
- Bots created from Insights synchronize themselves with their parent insights
- Healthy and Paused Harvest Status and Visibility on the Clouds page no longer produce a popup
- Clouds Accounts tab has been upgraded to Clouds Summary tab, which displays common instance type counts and provider distribution
- Added GCP-specific values for Shared File System Lifecycle State and Performance Mode
- Support LDAPS with self signed certificate
- Add pagination support for AWS IAM SSL Certificates to support accounts with more than 100 certificates New/Improved Actions
Enable Global Encryption for Storage Containers
Users may apply global encryption (server side encryption) via a UI action or a Bot. Users can enable encryption for the bucket with either AES256 or aws:kms. If using aws:kms, you will need a kms master key id to complete the action. Make sure you have the correct key id because Amazon does not validate keys. This action will create a new encryption configuration or replace an existing one if one already exists.
Disable Global Encryption for Storage Containers
Users may disable global encryption (server side encryption) via a UI action or a Bot.
Remove Public Permissions from an Image
Private images may allow for public permissions. This UI and bot action will remove these permissions from an image so it is no longer accessible publicly.
Send Slack Message
This action now supports Jinja2 templating in the Channel field, allowing more options for dynamically setting the recipient. New Filters
Instance With Disabled Source/Destination Checking
The Source/Destination Check attribute controls whether source/destination checking is enabled on the instance. Disabling this attribute enables an instance to handle network traffic that isn’t specifically destined for the instance. For example, instances running services such as network address translation, routing, or a firewall should set this value to disabled. The default value for cloud providers is enabled.
Network With Multiple CIDR Blocks
Easily identify networks with multiple IPv4 CIDR block associations.
Enable Web Identity Federation
Dynamo DB tables can optionally have an IAM policy attached to them which can be used to enable web identity federation providers such as Facebook, Google, etc. This filter identifies distributed tables that have web federation enabled and gives the user the option to select which provider they would like to filter on.
Disable Web Identity Federation
Dynamo DB tables can optionally have an IAM policy attached to them which can be used to enable web identity federation providers such as Facebook, Google, etc. This filter identifies distributed tables that have web federation disabled.
Instance Exposing Any Ports
Identify compute instances which have at least one security group with any ingress rules which allow access from any address on Internet (0.0.0.0/0).
Resource Is Exposed To Public
This is a complement filter that calls through to a variety of other filters based on the supported resource types. Using this filter allows end-users to effortlessly identify exposed resources across a number of categories with one filter.
Data Stream Shards Greater Than
Identify Kinesis streams with number of shards greater than the provided value.
Data Stream Shards Less Than
Identify Kinesis streams with number of shards less than the provided value.
Data Stream Retention Period Greater Than
Identify Kinesis streams with number of retention days greater than the provided value.
Data Stream Retention Period Less Than
Identify Kinesis streams with number of retention days less than the provided value.
Data Stream Is Not Encrypted
Identify Kinesis streams without server-side encryption.
Data Stream Encrypted With Key
Identify all Kinesis streams encrypted with one of the specified encryption key(s).
Subnets With Internet Access
Identify network subnets which have an associated route table that routes 0.0.0.0/0 to an gateway device and can therefore reach the Internet.
Route Table Not Associated With Virtual Gateway
Identify route tables which are not associated with a virtual gateway.
Route Table Associated With Virtual Gateway
Identify route tables which are associated with a virtual gateway.
Network Flow Log Destination
Identify Cloudwatch Logs vs S3 destinations. On August 8th, 2018, Amazon released updated VPC Flow Logs to allow customers to deliver logs directly to an S3 bucket.
Network Flow Log Not Logging To Bucket
Identify Nework Flow Log is logging to the user-defined bucket name.
Bug Fixes
- Fixed a Bot scheduling bug that affected Bots on a weekly schedule
- Fix for AWS Kinesis & Firehose tag update breaking when batching 10+ tags.
- Fixed a bug where some resources which failed to harvest due to invalid permissions failed to show on Clouds listing.
- Fix for Dashboard & Scheduled Events displaying data for clouds that have been removed.
- Resolves an issue with DNS records that do not have a TTL set
- GCP: Add missing APIs to the listing
- Expand the VPC ID columns within network peers
- Fixed the filter “Identity Resource Contains Invalid Actions” to be able to identify a large number of inputs (reached max recursion depth)
- Resolves an issue with retrieving flow logs if they have been set to export to S3
- Fix for badge scoping on custom packs after removing all badges.
- Fix to silence the exception logs (for KMS)
- Fix an overzealous delete trigger on one of the tables for Resource Groups
- Fixed the filter “Instance Uses Simple Networking” that would improperly identify instances running in a VPC
- Fixed a bug that would prevent basic users from downloading a CSV report with custom cloud scopes
- Fixed a bug that would result in the JIRA integration attaching empty CSV files to tickets
- Fixed a bug that prevented Tag Explorer configurations from being saved in Firefox Quantum
- Fixed a bug that resulted in IAM resources not harvesting due to a root account that has never logged in
- Fixed a bug with the storage of empty inline policies for IAM resources
- Fixed a bug that resulted in VMware datastore resources not displaying in the resources section Developer/Administrator Notes
Important
For Amazon Web Service customers, the role/user policy associated with each connected account will need to be adjusted to include the permissions below. Without these permissions, visibility into the newly supported AWS services will not be possible.
The first permission allows DivvyCloud to harvest IAM details 400% faster, which helps you react to MFA, policy/permission, and group association changes in near real time.
"iam:GetAccountAuthorizationDetails",
"cloudsearch:DeleteDomain",
"cloudsearch:DescribeServiceAccessPolicies",
"cloudsearch:DescribeAvailabilityOptions",
"cloudsearch:DescribeDomains",
"cloudsearch:ListDomainNames",
"eks:DescribeCluster",
"eks:ListClusters",
"elasticmapreduce:DescribeCluster",
"elasticmapreduce:ListClusters",
"elasticmapreduce:ListInstances",
"firehose:DeleteDeliveryStream",
"firehose:DescribeDeliveryStream",
"firehose:ListDeliveryStreams",
"firehose:TagDeliveryStream",
"firehose:UntagDeliveryStream",
"kinesis:AddTagsToStream",
"kinesis:DeleteStream",
"kinesis:DescribeStream",
"kinesis:ListShards",
"kinesis:ListStreams",
"kinesis:ListTagsForStream",
"kinesis:RemoveTagsFromStream",For customers that are not running on RDS, you will need to update your permissions for the divvy user to include the flush permission. Please run the mysql query below:
GRANT RELOAD ON *.* TO 'divvy'@'<DivvyCloud.ip.range.here>' IDENTIFIED BY 'divvy';
The following API calls have had changes to the structure. If you use any of these, please take note of the changes.
v2/public/insights/list now accepts a query string parameter (detail=false)
to send more lightweight data about the Insight instead of the verbose
response that currently includes notes and other information. By default
detalied information is returned to maintain backwards compatibility. This
can be adjusted (e.g. https://hooli.divvycloud.com/v2/public/insights/list?detail=false).The following API call now includes the Insight count information in the response
v2/public/insights/<insight_id>/<source> [GET]The following API call now enforces a maximum limit of 1,000. If you are going to query the API for a larger resource set, we strongly encourage that you leverage the V3 API call which accepts the same structure, but returns a cursor that handles the pagination. This behavior is very similar to the token concept that AWS uses for their API. For an example of how this would work see our API calls documentation for examples and full details.
v2/public/resource/query [POST]