Feb 25, 2019
19.1.7 Release Notes
Divvy Software Release Notice - 19.1.7 Maintenance Release (04/25/2019)
- DV2019-1120: Fixed a bug that resulted in custom Insights with IDs larger than 281 from disappearing from Insight Packs. The Insight would still exist in the software, but would be removed from any custom pack once a day.
- DV2019-1155: Fixed a display issue that would result in AWS accounts from showing as having invalid credentials due to harvesting from ap-east-1 (Hong Kong) when it is not enabled.
19.1.6 Release Notes
Divvy Software Release Notice - 19.1.6 Maintenance Release (04/17/2019)
- DV2019-1050 Fixed an edge case that prevented the usage of Instance provisioning templates for AWS
- DV2019-1037 Fixed the dashboard graph that visualizes the top clouds by resource counts
- DV2019-1029 Prevent basic users and organization admins from viewing harvesting strategies
- DV2019-1033 Added missing resource tooltips for Network Interfaces and Public IP Addresses for Microsoft Azure and GCP
- DV2019-1024 Added a new filter
Instance Exposing Specific Portsthat allows users to identify compute instances with attached security groups that expose user defined ports/port ranges - DV2019-1059 Added a new Jinja2 template
get_untrusted_accounts()that can be used within Bot notification actions for resources that allow cross account access. - DV2019-1052 Expanded the platform monitoring script to include checks for cloud accounts configured for AWS Assume Role which have not had a recent credential refresh. When manifested this situation can result in the inability to harvest resources from the target AWS account, and the monitoring script will now include this in the report.
- DV2019-970 Surface the target AWS Role for each cloud account in the Clouds listing that is configured for AssumeRole operations
- DV2019-1049 Improved performance when using the
search_stringfilter via the programmatic API and added the ability to specify an optionaltarget_columnsparameter to search on specific columns
19.1.5 Release Notes
Divvy Software Release Notice - 19.1.5 Maintenance Release (04/09/2019)
- DV2019-966 Surface the Image Tag / Version for AWS ECR
- DV2019-964 Make the search case insensitive for “Identity Resource Contains Invalid Actions” filter
- DV2019-968 Surface the role associated with each cloud account for easier auditing 19.1.4 Release Notes
Divvy Software Release Notice - 19.1.4 Maintenance Release (04/03/2019)
- DV2019-972 Fixed an edge case that would prevent resource pagination via the API for the organization service resource type
- DV2019-958 Properly sort by Insight severity within the Insight Library
- DV2019-300 Improve the loading time of timeseries and gauge graph visualizations within the compliance pack overview screen
- DV2019-925 Add support for filtering on ALB/NLB logging destinations
- DV2019-844 Show the next run time for jobs in the Harvest Info screen and allow administrators to enqueue jobs for an immediate run
- DV2019-833 Extend the compliance data export capability to also support custom packs
19.1.3 Release Notes
Divvy Software Release Notice - 19.1.3 Maintenance Release (04/03/2019)
- DV2019-906 Bot action Stop/Start By Tag Value now supports case insensitivity
- DV2019-945 Improve performance when viewing the Insight Library and Dashboard Overview as a basic user 19.1.2 Release Notes
Divvy Software Release Notice - 19.1.2 Maintenance Release (03/27/2019)
- DV2019-872 Fixed the filter “Load Balancer With/Without SSL Listener” to now include classic ELBs with listeners that terminate SSL at the instance
- DV2019-871 Fixed an issue where the “Custom Insight Pack” counts were reflecting the incorrect total insights
- DV2019-868 Fixed an issue where the “Only Failed Insights” check box didn’t respect the cloud/resource group scope
- DV2019-867 Fixed an issue where the “Resource deletion hookpoints” were not consistently triggering for select resource types
- DV2019-675 Fixed an issue where the “Create Database Instance Snapshot” failed due to default snapshot name
- DV2019-813 Added support for “eu-north-1” as a region for “Harvesting Strategies”
- DV2019-758 Increased the refresh time for the “Resources” column (resource counts) to update quicker from 20 to 10 minutes. This is under the Resource Groups Page.
- DV2019-818 Removed support for Azure in the following filter “Instance with Ephemeral Root Device” which is used in the insight “Instance with Ephemeral Root Volume”
- DV2019-879 Fixed an issue where the Resource Tooltips were not working for Safari
- DV2019-323 Added ability to white-label the EDH overview image asset
- DV2019-862 Fixed an issue where the secrets were not being loaded properly for deployments that leverage AWS Secrets Manager to further secure their database credentials
19.1 Release Notes
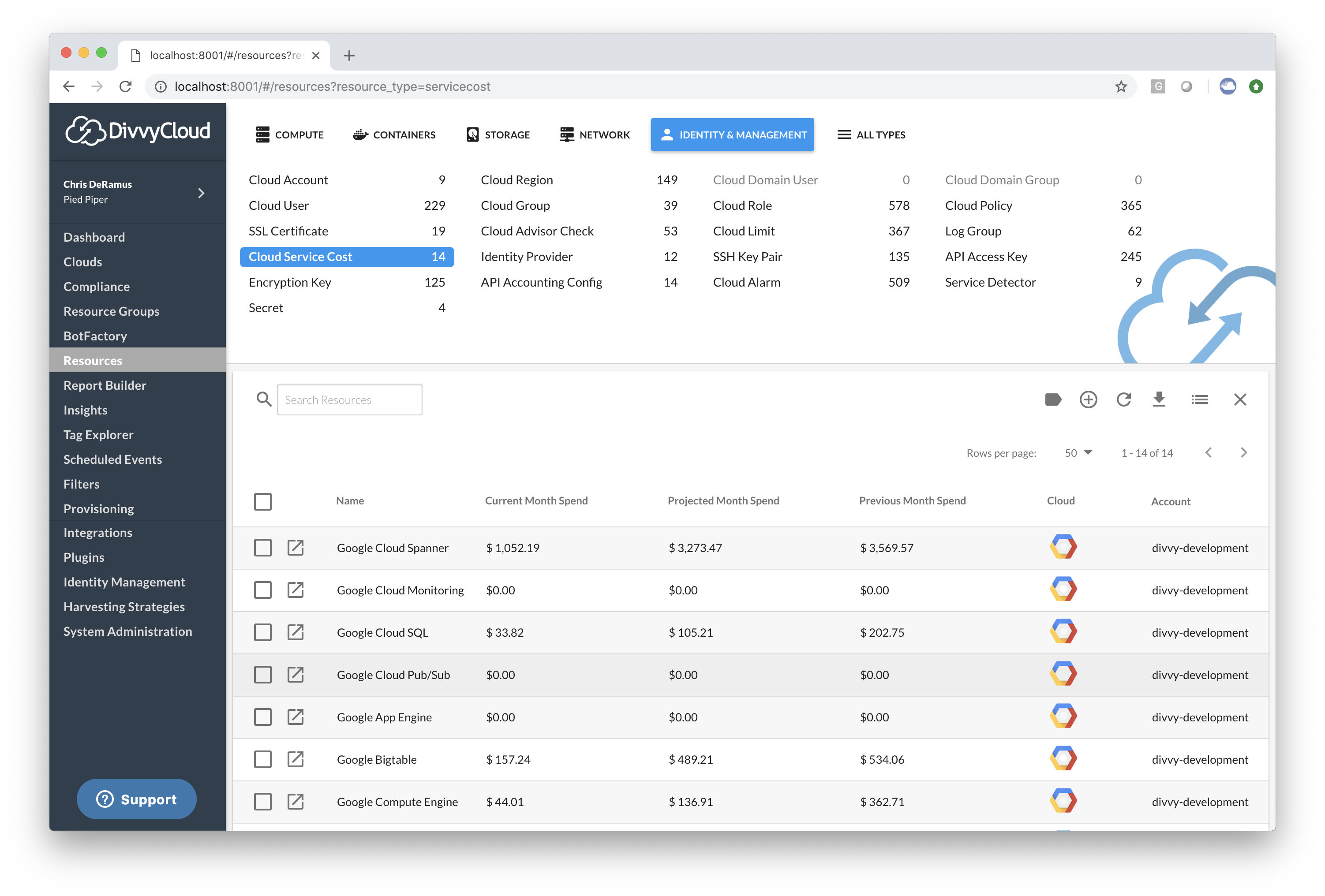
Google Cloud Platform Billing Visibility
Customers can now retrieve the billing information for their Google footprint by interconnecting DivvyCloud with the Billing bucket where the monthly billing data is stored. Once this data has been saved inside of the tool, we will harvest and surface billing information in the tool. This information can be accessed via Resources > Identity & Management > Cloud Service Cost. The image below illustrates what it looks like once loaded.
Worker Optimizations
We’ve made some massive improvements to our worker tier, the processes responsible for retrieving and processing data from the Cloud. In general, folks should likely see ~30-40% memory reduction across their worker fleet, and should be able to increase the number of workers on each system. Please reach out to support@divvycloud.com for instructions on how to best increase capacity based on your deployment model.
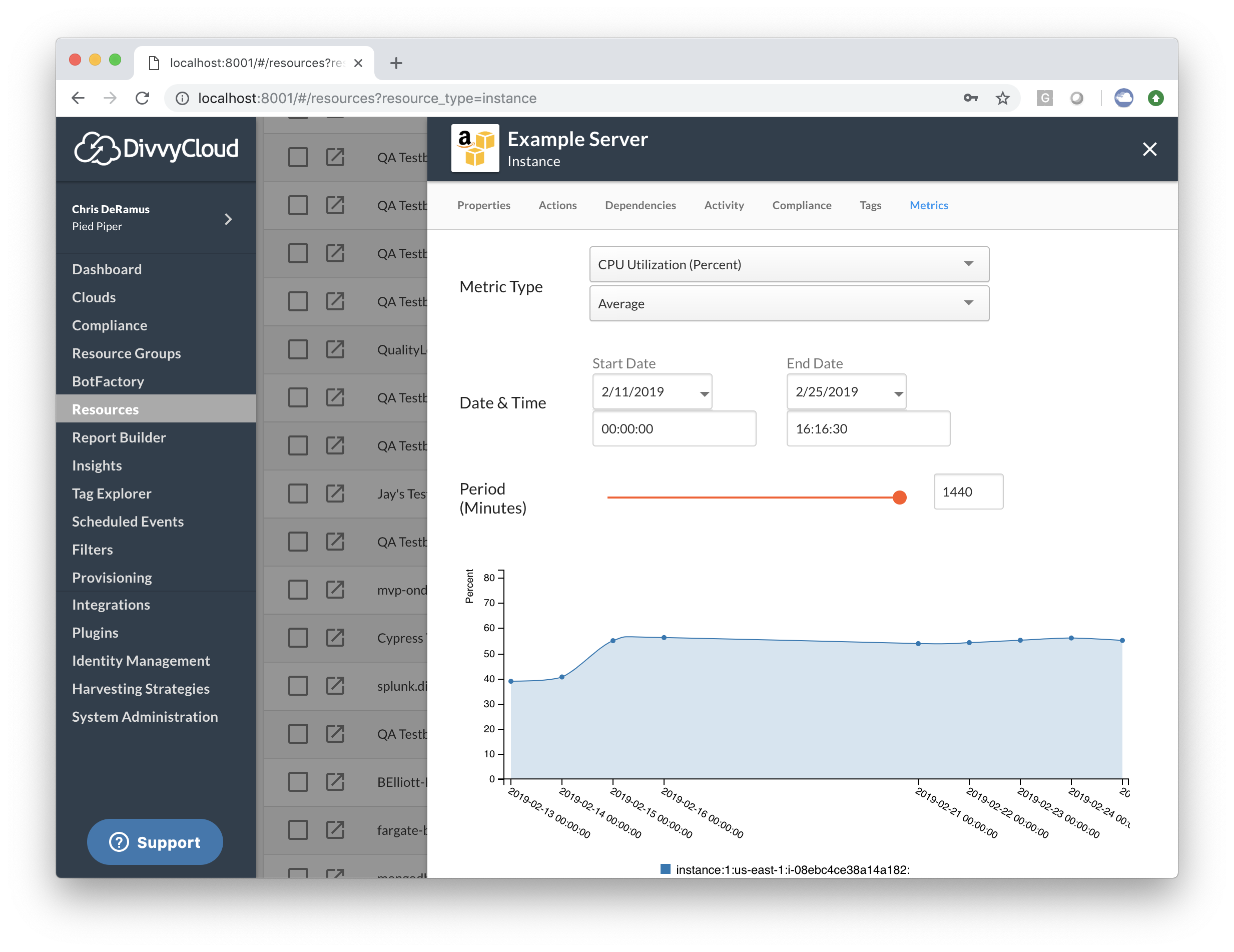
On-Demand Performance Visibility
For customers who are monitoring Amazon Web Service clouds within the tool, you now can pull AWS CloudWatch metrics for select resources. This can be accessed by clicking on the Metrics tab when inspecting the resource details of an AWS resource. We plan on expanding this feature to cover Google Cloud Platform and Microsoft Azure resources in the near future. The following resource types have this support:
- EC2 (Instances): CPUUtilization, NetworkIn, NetworkOut
- EBS (Volumes): VolumeReadBytes, VolumeWriteBytes, VolumeReadOps, VolumeWriteOps
- RDS (Database Instances): CPUUtilization, DatabaseConnections, FreeableMemory, FreeStorageSpace
- Redshift (Big Data Instances): CPUUtilization, DatabaseConnections, FreeableMemory, FreeStorageSpace
- Lambda (Serverless Functions): Invocations, Errors, Duration, ConcurrentExecutions
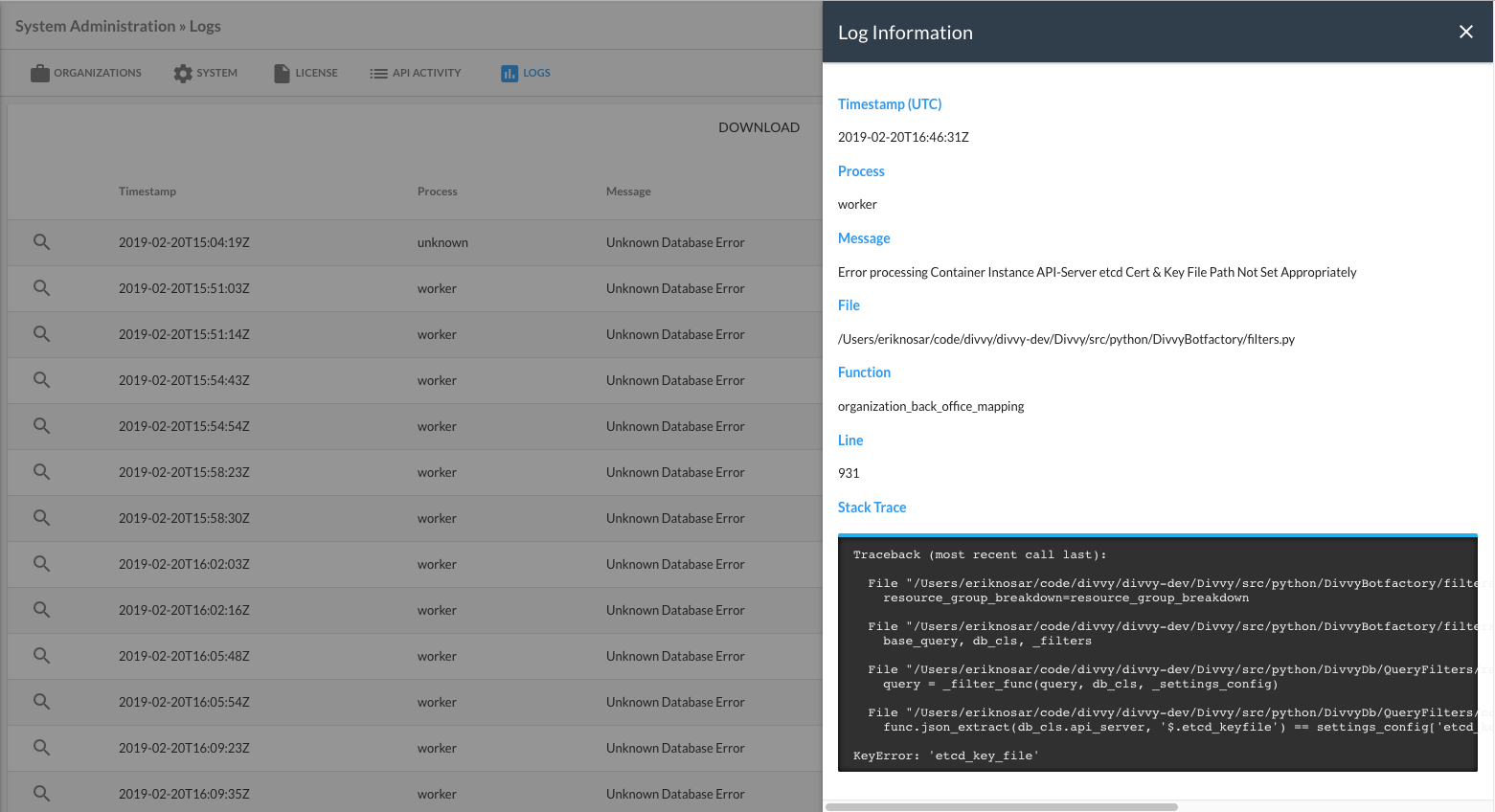
In-app Logging
Administrators can now access system logs from within the tool. When errors are observed outside of missing permissions problems, the information is included in the tool and stored for 48 hours. This data can be helpful when troubleshooting and helps mitigate the need to pull logs manually, which may require further access. To access this feature, click on System Administration > Logs. Note that this information has a slight delay on when it populates (every 3 minutes). Data is maintained for 24 hours.
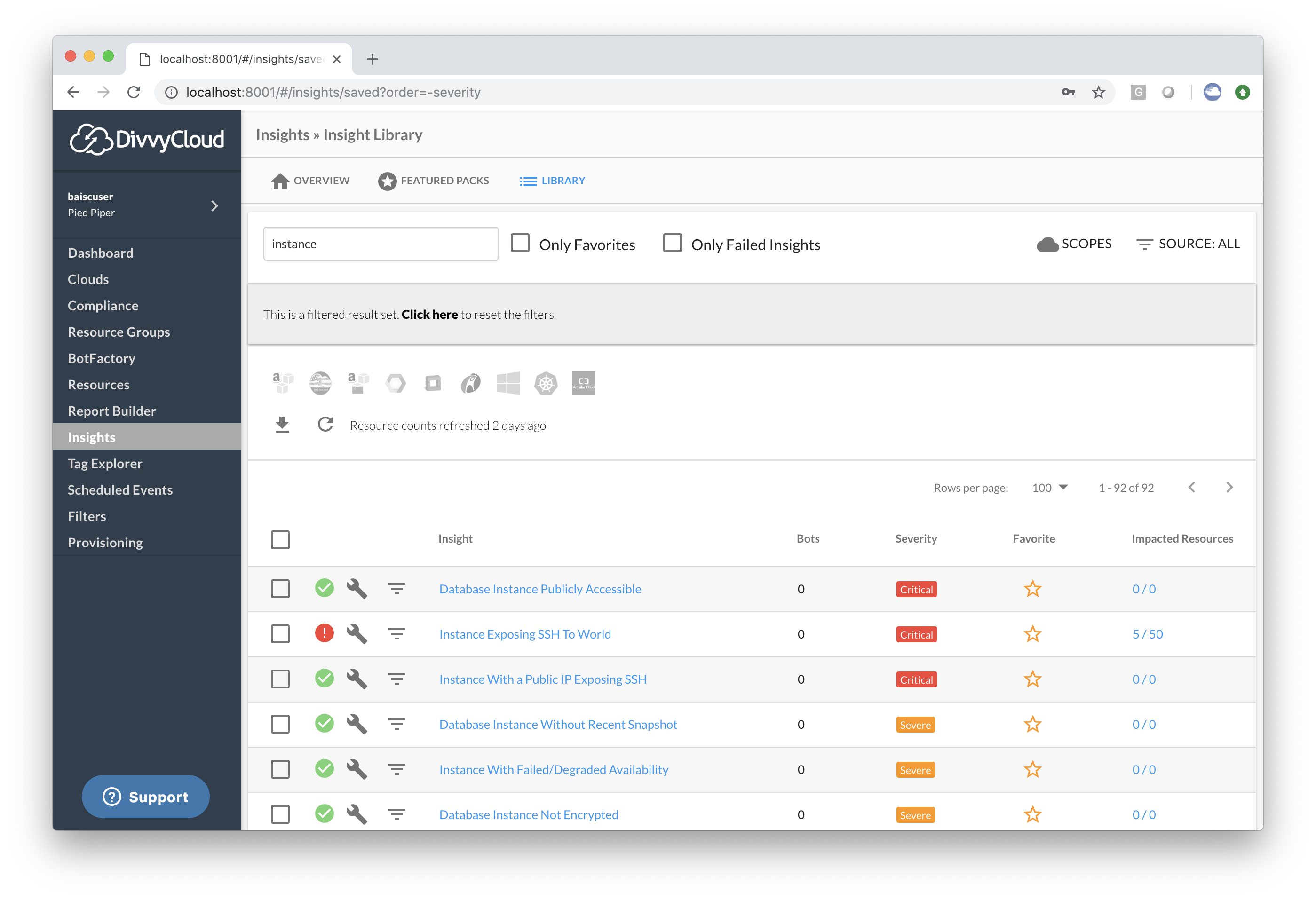
Basic User Insight Totals
Our team has made some improvements to the Insight Library for basic users. Now the Insight results and totals are only calculated for the clouds and resource groups that users have permission to view. These permission checks were previously applied when users went to drill down into the resource counts; however, based on customer feedback, we’ve taken the permissions into consideration when looking at the overview. This improvement should help mitigate confusion when browsing from the overview screen to the drill down view.
Google Project Auto Badging
When linking DivvyCloud to a Google Organization, customers can now opt-in to auto badge projects in the platform. For review, Badges are a key component of the platform, allowing administrators to fine-tune automation policies, insight results, compliance reporting, and identity access management. When auto badging is enabled, the labels that are assigned to projects will be automatically synchronized to badges in the DivvyCloud system. As shown in the screenshots below, with auto badging enabled, the labels in the GCP Console (first screenshot) will show as badges inside of DivvyCloud.
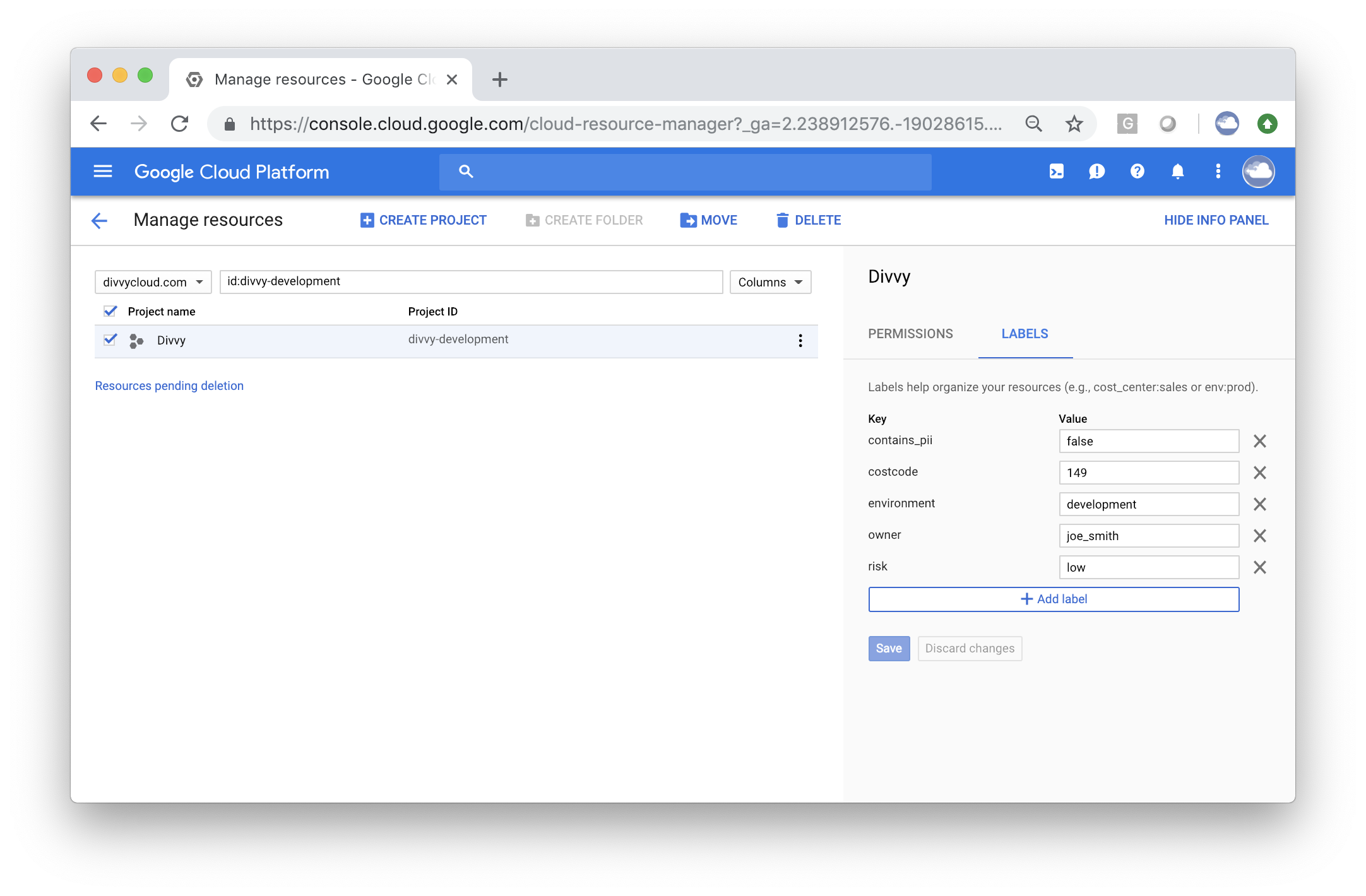
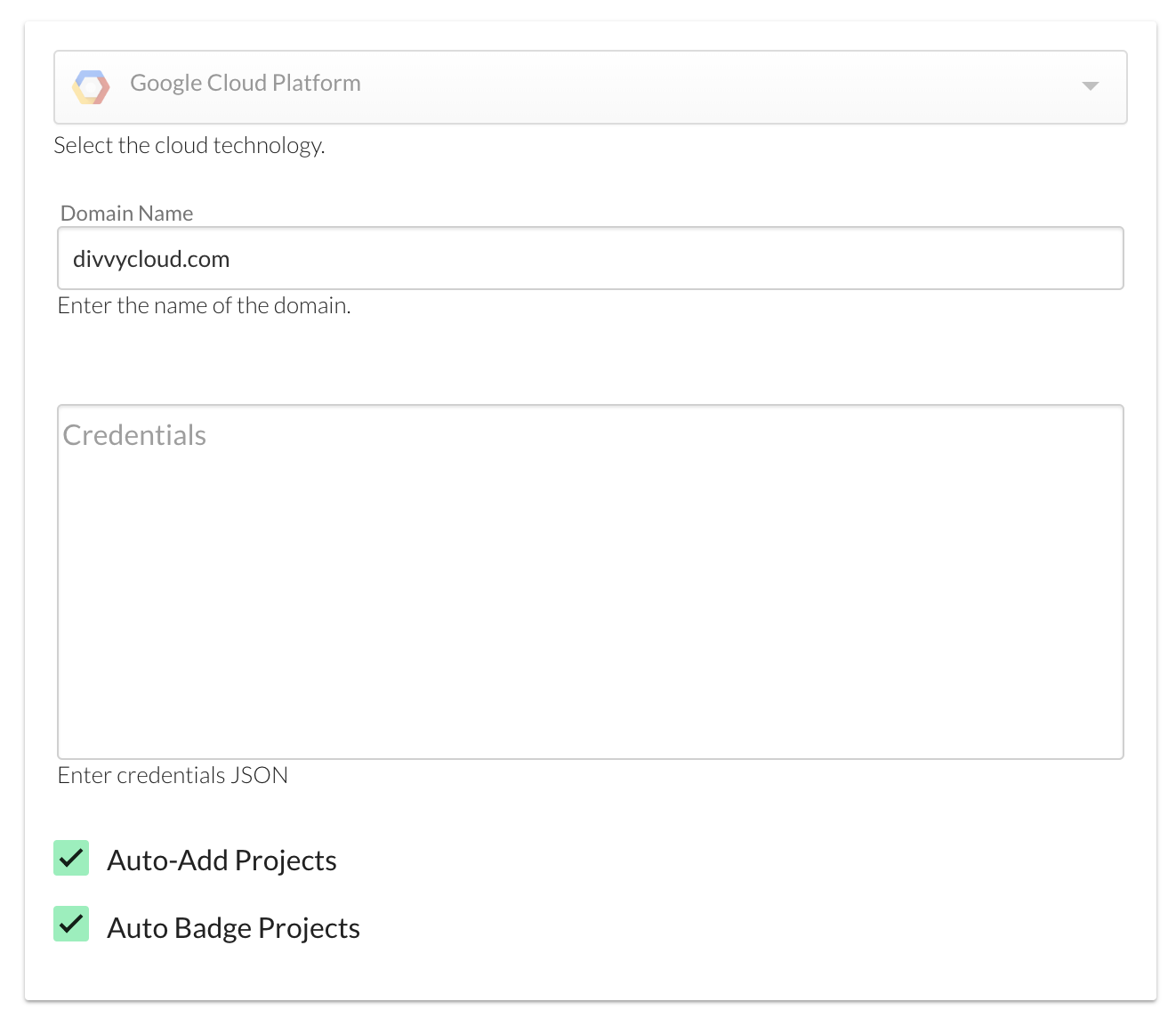
Resource Matrix Visibility
Customers can now access the resource matrix mapping directly from the Resources section of the tool. Simply highlight the resource in question and a tooltip will display with the mapping across AWS, Azure, Google Cloud Platform, and VMware.
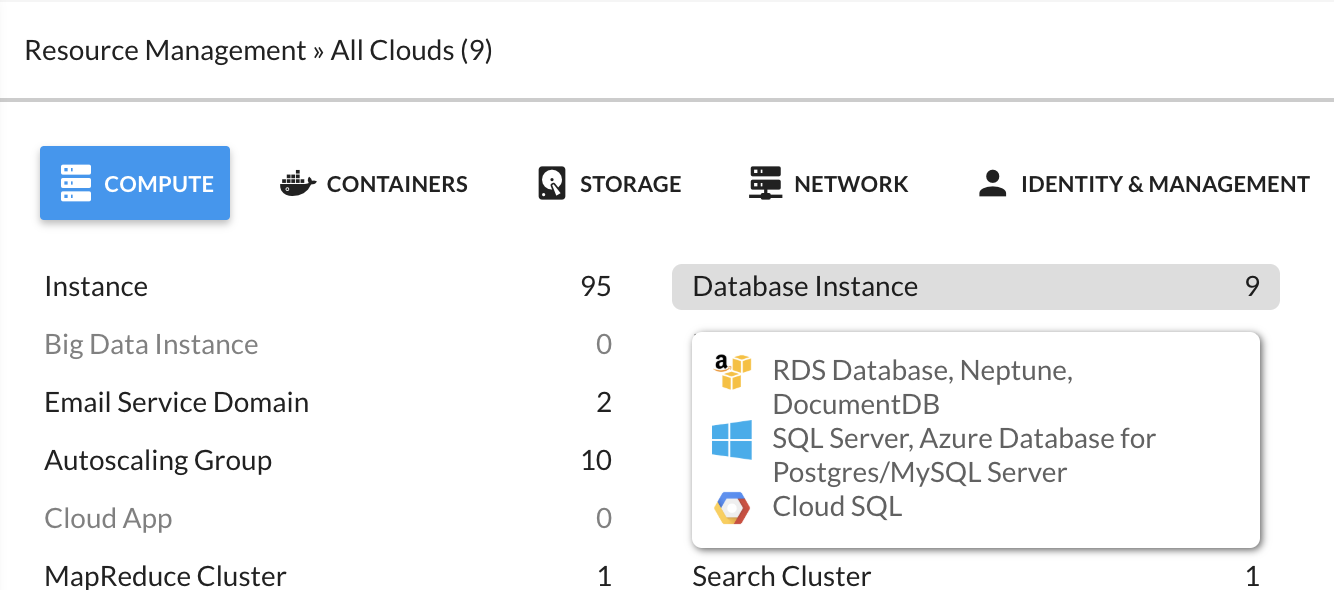
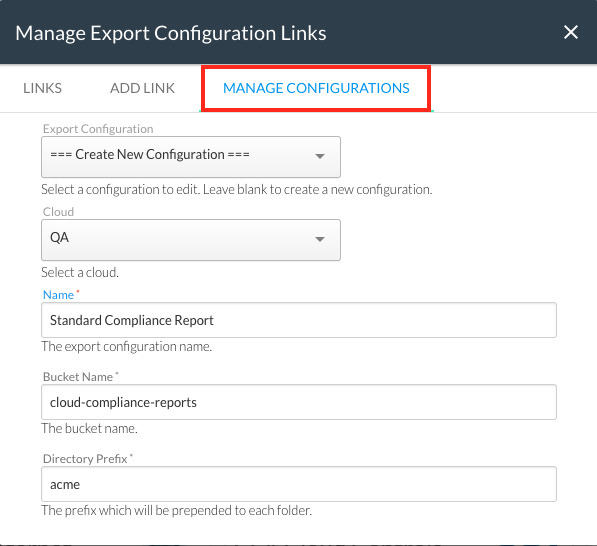
Data Exporter - Compliance Exporting
DivvyCloud now offers a new way to export compliance information from insight packs. Each user-configured report is generated daily and uploaded to the user’s AWS or GCP storage bucket-of-choice, using the credentials of an organization service account. For more information, see Compliance Exporting.
Additional Cloud Support/Enhancements Following are the additional services which DivvyCloud supports with Release 19.1. For a complete listing of supported services, follow the links provided to the specific cloud service provider.
Amazon Web Services
- Support for API Gateway
- Support for DocumentDB
- Support for Neptune
- Support for Secrets Manager
- Support for FSx Click here for a complete list of DivvyCloud-supported AWS services.
Google Cloud Platform
- Support for BigQuery
- Support for Billing
- Support for Load Balancing Click here for a complete list of DivvyCloud-supported Google Cloud Platform services.
Microsoft Azure
- Capture Azure Key Vault information for Storage Accounts
- Add visibility to the encryption configuration for Blob Storage Click here for a complete list of DivvyCloud-supported Microsoft Azure services.
Developer/Administrator Notes
New Cloud Permissions
Customers will need to adjust their AWS and Google Cloud Platform permissions to get visibility into the new services. Listed below are the new permissions required.
Amazon Web Services
"apigateway:GET",
"apigateway:GetRestApis",
"apigateway:GetRestStages",
"apigateway:GetRestApiKeys",
"apigateway:GetAuthorizers",
"fsx:DescribeFileSystems",
"secretsmanager:ListSecrets",
"secretsmanager:GetResourcePolicy",
"secretsmanager:DescribeSecret",
"tag:GetResources"Google Cloud Platform
"bigquery.tables.list",
"bigquery.datasets.list"Compliance Amazon Web Services
Prior to this 19.1 release, the insight Cloud Account Password Policy Not CIS Compliant, which is tied to the Cloud Account Fails AWS CIS Password Policy, was missing a few conditions that would have potentially made your cloud account fail this compliance check.
We have updated the Filter Cloud Account Fails AWS CIS Password Policy to include the following:
db_cls.password_policy['expire_passwords'] == 'false',
db_cls.password_policy['password_reuse_prevention'] < '24',
db_cls.password_policy['password_reuse_prevention'] == 'nullImmediate Action Needed
If you are using this Insight Cloud Account Password Policy Not CIS Compliant, or this filter Cloud Account Fails AWS CIS Password Policy, we recommend you immediately check to see if you pass that compliance check.
The difference for the filter Cloud Account Fails AWS CIS Password Policy is shown below.
Before
db_cls.password_policy['require_uppercase_characters'] == 'false',
db_cls.password_policy['require_lowercase_characters'] == 'false',
db_cls.password_policy['require_symbols'] == 'false',
db_cls.password_policy['require_numbers'] == 'false',
db_cls.password_policy['max_password_age'] > 90,
db_cls.password_policy['minimum_password_length'] < 14After
db_cls.password_policy['require_uppercase_characters'] == 'false',
db_cls.password_policy['require_lowercase_characters'] == 'false',
db_cls.password_policy['require_symbols'] == 'false',
db_cls.password_policy['require_numbers'] == 'false',
db_cls.password_policy['max_password_age'] > 90,
db_cls.password_policy['expire_passwords'] == 'false',
db_cls.password_policy['minimum_password_length'] < 14,
db_cls.password_policy['password_reuse_prevention'] < '24',
db_cls.password_policy['password_reuse_prevention'] == 'nullGeneral Enhancements
- The key used to encrypt Big Data Instances (AWS Redshift) is now stored, which enables customers to further inspect the encryption at rest configuration.
- Customers can now filter out Insights which are compliant/have zero results in both the Insight Library and the Compliance sections of the product.
- Insight scope changes are now sticky and persist as you navigate the tool.
- Supported cloud icons are now displayed for both filters and actions during Bot creation.
- Custom packs now have options to inherit compliance rules from system packs when being created.