Feb 22, 2022
InsightCloudSec is pleased to announce Minor Release 22.1.5
InsightCloudSec Software Release Notice - 22.1.5 Minor Release (02/23/2022)
Our latest Minor Release 22.1.5 is available for hosted customers on Wednesday, February 23, 2022. Availability for self-hosted customers is Thursday, February 24, 2022. If you’re interested in learning more about becoming a hosted customer, reach out through our Customer Support Portal .
Release Highlights (22.1.5 )
InsightCloudSec is pleased to announce Minor Release 22.1.5. This release features several changes to our Insights including: a new Center for Internet Security (CIS) - Azure 1.4.0 Compliance Pack, (which with this release provides a total of 45 Insights and 5 completely new Insights); revisions to our in-product content around Critical Insights; and updates around deprecated Azure Insights. We are also updating to our Compliance Scorecard subscription emails, expanding support for resources (AWS, Azure, and GCP), and adding API support for filtering the listing of Insights by their labels. 22.1.5 includes three new and one updated Query Filters, one new and one enhanced Bot action, and four bug fixes.
In addition, for our Cloud IAM Governance module, we have details around two bug fixes.
Contact us through the new unified Customer Support Portal with any questions.
Features & Enhancements (22.1.5 )
Center for Internet Security (CIS) - Azure 1.4.0 Compliance Pack The new Center for Internet Security (CIS) - Azure 1.4.0 Pack is a group of Insights that align with newly updated Azure CIS 1.4.0 Benchmarks. The CIS benchmarks provide prescriptive guidance for configuring security options for a subset of Azure Services with an emphasis on foundational, testable, and architecture agnostic settings. This Compliance Pack includes a total of 45 Insights including the following five new Insights [ENG-14389 & ENG-13761]:
Database Instance Vulnerability Assessment without Recurring Scans Enabled- New Insight identifies database instances that do not have a recurring scans enabled vulnerability assessments.Database Instance Vulnerability Assessment not associated with Storage Account- New Insight identifies database instances that do not have a storage account configured for storing vulnerability.Database Instance Vulnerability Assessment without Admin Email Notifications- New Insight identifies database instances that do not send email notifications to admins and subscription owners.Database Instance Vulnerability Assessment without Email Notifications- New Insight identifies database instances that do not send email notifications to concerned data owners/stakeholders.Instance using Unmanaged Disk- New Insight identifies instances using unmanaged disks.
Support for Filtering Insights
We have added API support for filtering the listing of Insights by their labels. For example, this command pulls down all Insights that are labeled cis controls:
curl '<insert_your_domain_here>/v2/public/insights/list?detail=false&v2_cache=true&labels=cis%20controls' \
-H 'Accept: application/json, text/plain, /' \
-H 'Cookie: session_timeout=60; session_id=<insert_your_session_id_here>;' \
--compressedNote the use of URL encoding to change the space in cis controls to cis%20controls. Multiple tags can be used in combination too, e.g., cis%20controls,security,best%20practice,security%20center
[ENG-13760]
Compliance Scorecard Updated the subject line behavior in the Compliance Scorecard subscription email. With this release, for users that have a subscription with 100% compliance, rather than force a user to click a link, authenticate, and download the details, the user will have this notification in the subject of the email. [ENG-12030]
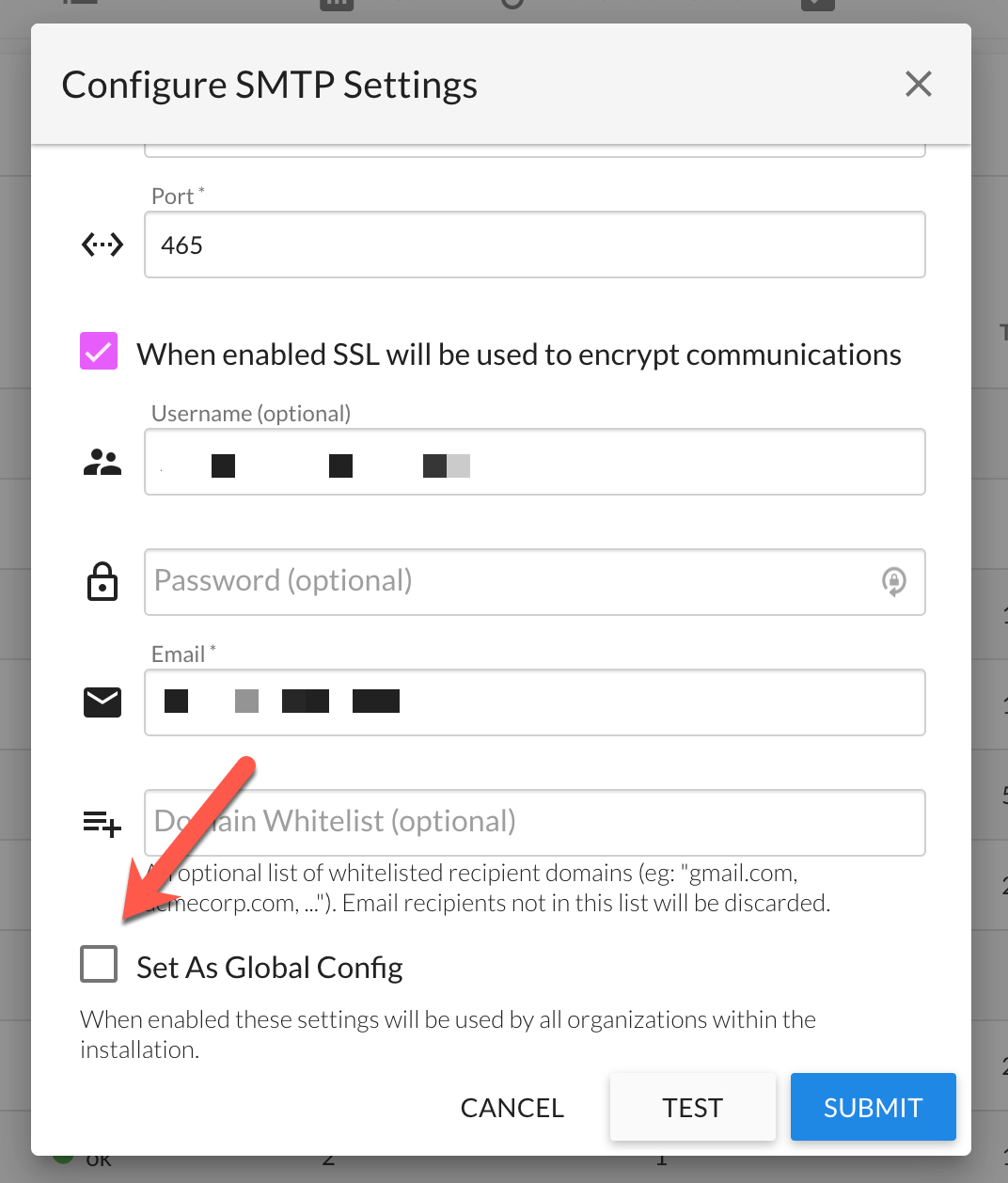
SMTP/Email Settings Updated InsightCloudSec email/SMTP settings to allow configuration in a single InsightCloudSec Organization to be used by all other Organizations. For customers with multiple Organizations, this can simplify email management. [ENG-13444]
Insight Library
Updated the Insight Library view to persist the Only Failed option as a parameter. This change allows for better direct linking and history. [ENG-13467]
Cloud Advisor Check We have updated Cloud Advisor Check status to better reflect failed checks for GCP and Azure. For GCP, instead of “error”, we have “failed resources”. For Azure, we have added indicators like “low usage”. [ENG-14349]
Resources (22.1.5 )
AWS
- Added a new column, “Public”, to AWS Secrets resource details list which will report if the secret is “Public” or “Not Public”. [ENG-14420]
- Added visibility, IaC, and filter support for the DynamoDB billing mode. Additional information can be referenced in the AWS blog for this feature. A new Query Filter,
Distributed Table Billing Mode (AWS)identifies distributed tables based on the configured billing mode. [ENG-14402]
AZURE
- Added functionality for category groups in Diagnostic Settings. Azure has added functionality to add ‘category groups’ for diagnostic settings; instead of having to add single categories, categories can be enabled in a category group. Customers using category groups will now be able to filter using these, with our Diagnostic Settings Query Filters (
Batch Environment Invalid Diagnostic Logging Configuration (Azure), etc.), and harvests won’t fail if these are used. Further information can be found on Microsoft’s Diagnostic Settings reference page. [ENG-13349]
Insights (22.1.5 )
Update of Critical Insights As part of our efforts to improve details within InsightCloudSec, we have updated critical Insight details within the product to have a more consistent format. Updates are being made incrementally by severity level. The updates to Insight details include [ENG-13507]:
- Insight titles will be provided in title case, i.e., a convention used for capitalizing the words in a title, subtitle, heading, or headline: capitalize the first word, the last word, and all major words in between.
- If an Insight only supports a single cloud, it will have the cloud service provider in parenthesis after the title, i.e., “(AWS)”.
- Added a Supported Clouds section in the Insight Info to let customers know which clouds are supported by the Insight.
- Added a section for IaC support, if applicable.
- Updated the Remediation section with details.
- Revised Insight titles that say “open to the world” (or some variant of this) to “open to the public” (or some variant of this) in order to make Insights referring to public-facing findings easier to search.
AZURE
-
Storage Container Soft Delete Disabled- New Insight for the Azure CIS 1.4.0 pack identifies storage containers which have Soft Delete disabled. The Azure Storage blobs contain data like ePHI, Financial, secret or personal. Erroneously modified or deleted accidentally by an application or other storage account user cause data loss or data unavailability. It is recommended the Azure Storage be made recoverable by enabling soft delete configuration. This is to save and recover data when blobs or blob snapshots are deleted. [ENG-14363] -
Added 5 new Insights for inclusion in the Azure CIS 1.4.0 pack. Refer to details under Features. [ENG-14389]
-
Removed 20 retired Azure Insights. The retired Insights are [ENG-13286]:
Activity Log Profile Not ConfiguredActivity Log Retention Less Than 365 DaysActivity Log Profile Does Not Capture All ActivitiesActivity Log Profile Not Configured For All RegionsCloud Account Security Center NSGs Recommendation Not EnabledCloud Account Security Center Setting 'Security Contact Emails' Not SetCloud Account Security Center Setting 'Send Me Emails About Alerts' DisabledCloud Account Security Center Setting 'Send Email Also To Subscription Owners' DisabledSecurity Center Automatic Provisioning Of Monitoring Agent Is OffSecurity Center System Updates Recommendation Is OffSecurity Center Security Configurations Recommendation Is OffSecurity Center Endpoint Protection Recommendation Is OffSecurity Center Disk Encryption Recommendation Is OffSecurity Center Web Application Firewall Recommendation Is OffSecurity Center Next Generation Firewall Recommendation Is OffSecurity Center Vulnerability Assessment Recommendation Is OffSecurity Center Storage Encryption Recommendation Is OffSecurity Center Adaptive Application Controls Recommendation Is OffSecurity Center SQL Auditing & Threat Detection Recommendation Is OffSecurity Center SQL Encryption Recommendation Is Off
Query Filters (22.1.5 )
AWS
Cloud Account Linked To Payer Account (AWS)- Enhanced this Query Filter by adding a “Not Linked” option to facilitate discovery in your cloud environment. [ENG-14370]Distributed Table Billing Mode (AWS)- New Query Filter, identifies distributed tables based on the configured billing mode. This Query Filter supports the added visibility for the DynamoDB billing mode. [ENG-14402]
AZURE
Function App Invalid Diagnostic Logging Configuration (Azure)- New filter identifies Function Apps without the proper diagnostic configuration. [ENG-14352]
MULTI-CLOUD/GENERAL
Resource Encryption Key Name Contains Regular Expression (Regex)- New Query Filter allows you to create an Insight that will track your use of approved keys, provided you use a standard naming convention, e.g.,<account-number><approved-name><service>-<region>. [ENG-14341]
Bot Actions (22.1.5 )
- “Disable Encryption Key” - New action for AWS KMS resources to disable encryption keys. This action is available via Resource Details and via Bot. [ENG-13470]
- “Cleanup Public Security Group Rules” - Enhanced the Bot action that cleans up public security group rules to include a new option that requires the rule to be an exact match to become a target for deletion. This selection will skip rules if it’s a port range/all protocols rule. [ENG-14304]
Bug Fixes (22.1.5 )
- [ENG-13799] Fixed a bug involving AWS GovCloud permission errors not showing in the UI. Updated our AWS GovCloud permissions check under Cloud Listing to verify that the recommended permissions are in place for Step Functions and Transcription Jobs.
- [ENG-13460] Fixed an issue involving validations of the LPA CloudTrail Sources name field. Name must now be composed of: lowercase letters, numbers and/or underscores, e.g., “lpa_source_name”. Spaces not permitted.
- [ENG-13328] Fixed an issue with the specified target for Azure Routes, when the target type is a virtual appliance.
- [ENG-12961] Fixed an issue where Azure Serverless Functions harvesting might fail.
Cloud IAM Governance (Access Explorer) Updates - 22.1.5 Minor Release (02/23/2022)
** The following updates are related to enhancements and bug fixes for our Cloud IAM Governance (Access Explorer) capabilities.** Contact us at Customer Support Portal with any questions.
Cloud IAM Governance Bug Fixes (22.1.5 )
- [ENG-13385] Fixed a bug involving the “Principal Explorer” option on the Resources Account view. The “Principal Explorer” option from Root Account view on Resources -> Cloud User -> “Root account” is now hidden. This information is not applicable for Root users.
- [ENG-13316] Fixed a bug where search results were not displaying when the user was on a page other than the first page in Access Explorer.