May 08, 2023
InsightCloudSec is pleased to announce Release 23.5.9
🚧 **Important Changes to Review **
Client Certificates - Potential Breaking Changes
In 23.4.18, we upgraded the version of cryptography we use which places additional restrictions on the formatting of certificates used to authenticate to certain cloud providers like Azure. In certain cases, some Azure accounts may be configured with a badly-formatted client certificate which will now be rejected by cryptography. If you have any issues with Azure harvesting after updating to this release and you are using Client Certificate authentication for that cloud, please reach out to support for further remediation steps.Refer to the following link for additional details.
Release Highlights (23.5.9)
InsightCloudSec is pleased to announce Release 23.5.9. This release includes support for a new Saved Filters capability that allows users to filter the displayed data on a feature page and save that filtered view for later use. We have also added visibility and harvesting for AWS Kinesis Analytics Streaming Applications. In addition, 23.5.9 includes four updated Query Filters, 19 new Query Filters, and 17 bug fixes.
- Contact us through the unified Customer Support Portal with any questions.
📘 Self-Hosted Deployment Updates (23.5.9)
Release availability for self-hosted customers is Thursday, May 11, 2023. If you’re interested in learning more about becoming a hosted customer, reach out through our Customer Support Portal .
Our latest Terraform template (static files and modules) can be found here: https://s3.amazonaws.com/get.divvycloud.com/prodserv/divvycloud-prodserv-tf/example-usage/aws/release/divvycloud-tf-release.zip
Modules can be updated with the
terraform get -updatecommand.
New Permissions Required (23.5.9)
Note: Additional permissions references can be found at the end of the release notes under “Required Policies & Permissions”.
🚧 New Permissions: AWS
For AWS Commercial Read Only and GovCloud Standard (Read-Only) Users :
“kinesisanalytics:DescribeApplication”,
“kinesisanalytics:ListApplications”For AWS Commercial Power User Policy and AWS GovCloud Power Users :
“kinesisanalytics:*”These permissions support the newly added resource AWS Kinesis Analytics Streaming Applications [ENG-22654] for both AWS commercial and AWS GovCloud Standard (Read-only) and Power Users.
Note: We recommend our AWS commercial (non-GovCloud) Standard (Read-Only) Users employ AWS’ managed read-only policy, supplemented by a small additional InsightCloudSec policy. The benefit of using the AWS managed policy lies in AWS’ continuously updating the policy for new services, making it easier for the customer to harvest new resources and properties without changing harvesting policies. Details on this recommendation can be found at AWS IAM Policies Standard User (Read-Only) AWS-managed supplemental policy.
Features & Enhancements (23.5.9)
Saved Filters
Beginning with 23.5.9, InsightCloudSec includes support for a new Saved Filters capability. This capability allows users to filter the displayed data on a feature page and save that filtered view for later use. A Saved Filter can be set as the default view for a user on a feature page; it can also be shared globally so other users within the customer organization can use the Saved Filter(s). This capability is available as part of Layered Context , Identity Analysis , IaC , and Threat Findings .
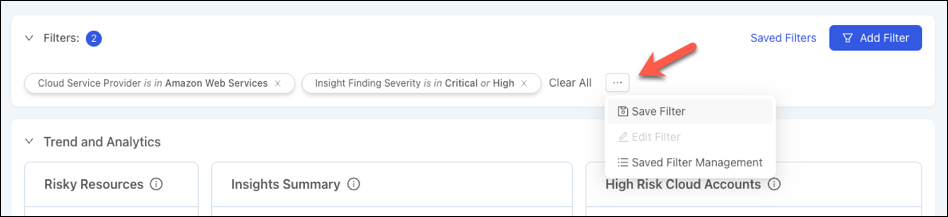
Additional Features & Enhancements
-
Expanded vulnerability assessment failure support in frontend service to provide better explanation/fix of the assessment result. [ENG-26633]
-
Expanded the response for the
delete_collection_dataendpoint to now send back a list of collection data IDs that were removed. [ENG-20660] -
Updated the API endpoint used to retrieve badges when building out new Insight Packs to support badges in use and those not in use. [ENG-17212]
-
Added a tooltip clarifying how we compress permissions in the resource panel to make it easier to analyze them. [ENG-26176]
-
Added the relationship between SSL Certificate Authorities and SSL Certificates. Now when viewing SSL Certificates created from an SSL Certificate Authority, you can see and link to the originating Authority. [ENG-26758]
Resources (23.5.9)
AWS
-
Added visibility and harvesting for AWS Kinesis Analytics Streaming Applications (Category Compute, new resource type Streaming Applications). New permissions are required: “kinesisanalytics:DescribeApplication” and “kinesisanalytics:ListApplications”. [ENG-22654]
-
Added the “Apply Policy” button within the Remediation tab of the Resource Panel allowing the InsightCloudSec remediation policy to be directly applied, this is only available for AWS IAM Users and Roles. The changes that are made to your AWS IAM User or Role will only be visible after the next Harvest of your cloud identities. Alternatively, you can manually run the “IdentityDetailHarvester” to see results more quickly. [ENG-24111]
-
Added compression (
compress_actions) to LPA remediation policies to fit the AWS character limit. [ENG-23976]
AZURE
- The
Deleteaction is now supported for Azure content delivery networks. [ENG-21148]
GCP
- The Artifact Registry resource now supports tagging for GCP. [ENG-17852]
Insights (23.5.9)
- We have updated Exemption Rules to include their creation date. For existing rules, we have included an SQL script to populate creation dates from API Activity when that data is available. [ENG-21008]
Query Filters (23.5.9)
AWS
-
Stored Parameter Is/Is Not Encrypted- Query Filter updated to optionally find encrypted stored parameters. [ENG-26619] -
Web Application Firewall With/Without Associated Resources- Broadened Query Filter to support AWS resources. [ENG-25826]
AZURE
-
Database Instance Azure Active Directory Admin not Configured- Updated this Query Filter name to remove the Azure labeling. Former name wasDatabase Instance Azure Active Directory Admin not Configured (Azure). [ENG-26265] -
Storage Account With Cross Tenant Replication Enabled- Updated this Query Filter name to remove the Azure Labeling. Former name wasStorage Account With Cross Tenant Replication Enabled. The filter has also been adjusted to account for storage accounts which have allow_cross_tenant_replication set to NULL. [ENG-25257] -
Added the following 19 Query Filters for Azure Cognitive Services:
-
Computer Vision (Cognitive Services) Configured with Public Access -
Computer Vision (Cognitive Services) without Managed Identity Enabled -
Content Moderator (Cognitive Services) Configured with Public Access -
Content Moderator (Cognitive Services) without Managed Identity Enabled -
Language Service (Cognitive Services) Configured with Public Access -
Language Service (Cognitive Services) using Microsoft Managed Encryption Key -
Language Service (Cognitive Services) without Managed Identity Enabled -
LUIS API (Cognitive Services) Configured with Public Access -
LUIS API (Cognitive Services) without Managed Identity Enabled -
Open AI (Cognitive Services) Configured with Public Access -
Open AI (Cognitive Services) without Managed Identity Enabled -
Personalizer (Cognitive Services) Configured with Public Access -
Personalizer (Cognitive Services) without Managed Identity Enabled -
Speech Service (Cognitive Services) Configured with Public Access -
Speech Service (Cognitive Services) using Microsoft Managed Encryption Key -
Speech Service (Cognitive Services) without Managed Identity Enabled -
Translator (Cognitive Services) Configured with Public Access -
Translator (Cognitive Services) using Microsoft Managed Encryption Key -
Translator (Cognitive Services) without Managed Identity Enabled
[ENG-25975]
-
Infrastructure as Code (IaC) (23.5.9)
-
Added IaC support for scanning DMS Replication Instance resources in CFTs when scanning via the API. [ENG-26774]
-
Added IaC support for scanning CloudTrail resources in CFTs when scanning via the API. [ENG-26773]
mimICS (23.5.9)
-
Updated the mimics version used for Terraform Cloud/Enterprise analysis from 1.0.5 to 1.2.0. This version of mimics includes Terraform analysis for AWS, so TFC/E analyses will now include actionable feedback where applicable. [ENG-26628]
-
Improved handling and display for errors in IaC scans created by the
mimicsCLI tool. [ENG-25472]
Bug Fixes (23.5.9)
-
Fixed a bug that prevented GCP CryptoKeys from being harvested. [ENG-26799]
-
Fixed issue with V1 IaC CFT scans of Load Balancers where the listener SSL policies were not persisted when simulating the resource. [ENG-26784]
-
Fixed an IaC conversion bug for AWS SQS resources that have SSE enabled. [ENG-26715]
-
Fixed a bug that prevented the harvesting of all Oracle Cloud Buckets. [ENG-26730]
-
Hardened AWS EDH for EC2 Instances to no longer trigger multiple hookpoints when the “Terminate Instances” action is processed. [ENG-26641]
-
Updated our public-facing logic for AWS Lambda and transit encryption logic for AWS S3 to accommodate case insensitivity supported by AWS for IAM policy conditions “AWS:SourceAccount” and “AWS:secureTransport”. See the AWS reference for details. [ENG-26640]
-
Fixed a bug involving missing display value: updated the transit encryption property of AWS Shared File Systems (EFS) to
Falseif transit encryption is not enforced. [ENG-26599] -
Resolved an issue with pagination when scoping clouds. [ENG-26551]
-
Fixed a bug where AWS::NoValue was not treated as an empty string. [ENG-26533]
-
Updated our Terraform IaC driver to evaluate whether an AWS Elasticsearch Domain is deployed outside a VPC when assessing whether it is publicly accessible. This is in addition to whether it has a permissive IAM policy. [ENG-26208]
-
Updated the Query Filter
Web Application Firewall Contains Rule Group Referenceto handle the edge case of someone renaming an AWS-managed rule. [ENG-25925] -
Fixed an issue where WAFs were not listing associated Load Balancers under the Related Resources view. [ENG-25826]
-
Fixed an issue where vulnerabilities sourced from IVM/Inspector2 were not included in the CSV report. [ENG-25814]
-
Fixed a bug with AWS IAM role parsing for IaC CFT analysis. [ENG-25812]
-
Fixed a bug where some columns were not populated in the Layered Context CSV export for Resources. [ENG-25595]
-
Updated harvester logic to correctly use the “Public Network Access” value from Azure when determining whether the container registry is open to the public. [ENG-24844]
-
We have fixed an issue when harvesting the
acceptance_requiredproperty for Azure Private Link Services. [ENG-22994]
📘 Policies & Permissions
InsightCloudSec offers the following policies and permissions (organized by Cloud Service Provider) to promote proper harvesting:
Alibaba Cloud
AWS
Note: These policies apply to Commercial, GovCloud, and China.
- Read Only Policy (AWS-Managed Supplement)
- Read Only Policy (Customer-Managed)
- Power User Policy
Azure
- Commercial
- GovCloud
GCP
- _For GCP, since permissions are tied to APIs there is no policy file to maintain. Refer to our list of Recommended
APIs that is maintained as part of our GCP coverage. _Oracle Cloud Infrastructure
Host Vulnerability Management
For any questions or concerns, as usual, reach out to us through your CSM, or the Customer Support Portal .